Ubuntu Security Notice 2365-1 – Nicolas Ruff discovered that LibVNCServer incorrectly handled memory when being advertised large screen sizes by the server. If a user were tricked into connecting to a malicious server, an attacker could use this issue to cause a denial of service, or possibly execute arbitrary code. Nicolas Ruff discovered that LibVNCServer incorrectly handled large ClientCutText messages. A remote attacker could use this issue to cause a server to crash, resulting in a denial of service. Various other issues were also addressed.
Monthly Archives: September 2014
Red Hat Security Advisory 2014-1318-01
Red Hat Security Advisory 2014-1318-01 – Red Hat Enterprise MRG is a next-generation IT infrastructure for enterprise computing. MRG offers increased performance, reliability, interoperability, and faster computing for enterprise customers. MRG Realtime provides the highest levels of predictability for consistent low-latency response times to meet the needs of time-sensitive workloads. MRG Realtime also provides new levels of determinism by optimizing lengthy kernel code paths to ensure that they do not become bottlenecks. This allows for better prioritization of applications, resulting in consistent, predictable response times for high-priority applications.
Red Hat Security Advisory 2014-1320-01
Red Hat Security Advisory 2014-1320-01 – Red Hat JBoss Enterprise Web Platform is a platform for Java applications, which integrates the JBoss Web Server with JBoss Hibernate and JBoss Seam. It was found that the fix for CVE-2012-5783 was incomplete: the code added to check that the server host name matches the domain name in a subject’s Common Name field in X.509 certificates was flawed. A man-in-the-middle attacker could use this flaw to spoof an SSL server using a specially crafted X.509 certificate. It was discovered that the HttpClient incorrectly extracted host name from an X.509 certificate subject’s Common Name field. A man-in-the-middle attacker could use this flaw to spoof an SSL server using a specially crafted X.509 certificate.
CVE-2014-4330
The Dumper method in Data::Dumper before 2.154, as used in Perl 5.20.1 and earlier, allows context-dependent attackers to cause a denial of service (stack consumption and crash) via an Array-Reference with many nested Array-References, which triggers a large number of recursive calls to the DD_dump function. (CVSS:2.1) (Last Update:2014-10-01)
DSA-3040 rsyslog – security update
Rainer Gerhards, the rsyslog project leader, reported a vulnerability in
Rsyslog, a system for log processing. As a consequence of this
vulnerability an attacker can send malformed messages to a server, if
this one accepts data from untrusted sources, and trigger a denial of
service attack.
Bacula-web 5.2.10 SQL Injection
Bacula-web version 5.2.10 suffers from a remote SQL injection vulnerability.
Apple Patches Shellshock Vulnerability in Bash for OS X
Apple released its patch for the Bash vulnerability, repairing versions of OS X vulnerable to Shellshock exploits.
ManageEngine OpManager / Social IT Arbitrary File Upload
This Metasploit module exploits a file upload vulnerability in ManageEngine OpManager and Social IT. The vulnerability exists in the FileCollector servlet which accepts unauthenticated file uploads. This Metasploit module has been tested successfully on OpManager v8.8 – v11.3 and on version 11.0 of SocialIT for Windows and Linux.
WPScan Vulnerability Database a New WordPress Security Resource
Researcher Ryan Dewhurst released the WPScan Vulnerability Database, a database housing security vulnerabilities in WordPress core code, plug-ins and themes. It’s available for pen-testers, WordPress administrators and developers.
Avast safeguards your teen’s smartphone
Teenagers are responsible for their smartphones. Help them keep it safe with a few easy additions.
Seven out of ten high schoolers take a smartphone to school. Not only are these phones being used for surfing the Internet or social networking, but they help kids navigate around campus, connect with teachers and other students, and follow streaming campus news. Many parents see equipping their teenager with a mobile phone as a safety tool and a way to keep in closer contact, especially if an emergency arises.
The first thing to do after buying your teenager a smartphone
Most kids are using a device with an Android operating system and no added security protection. The first thing you should do is to download a security app to protect the phone and data on it.
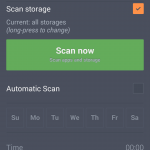
The newest version of avast! Mobile Security & Antivirus is out now, with a completely re-imagined user interface, making it simpler and even more user friendly than it was before. Avast! Mobile Security is free, and it will instantly begin protecting your child from downloading bad apps, protect against spyware and block malware, and backup contacts, SMS/call logs, and photos.
Install avast! Mobile Security and Antivirus from the Google Play store.
The second thing to do after buying your teenager a smartphone
High school students are busy people, with lots of activities, so it’s likely that your teen’s smartphone will be misplaced. Avast! Anti-theft is a stand-alone app that can be installed separately from avast! Mobile Security. You can use the phone locator features to find the lost or stolen phone, control it remotely, and lock it down.
Once you install avast! Mobile Security, you will be asked to set up the anti-theft module. You can read about that and the remote features you’ll have access to from your my.avast.com account in our avast! Mobile Security FAQs.
Install avast! Anti-Theft from the Google Play store.
Other things to do
- Set up a password for the smartphone. This is easy to do and will serve as the first line of defense against nosy people and thieves.
- Add important numbers to the contact list. Add your mobile number as well as a work line, grandparents, the school, and emergency contacts.
- Know the school’s rules. If phone usage is prohibited during school hours or allowed only during breaks, that’s important information to know.
- Talk to your kids about privacy. This includes a conversation about uploading photos and videos, sexting, and oversharing on social networks.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.