A vulnerability was discovered and patched in a third-party service that handles resumes on Facebook’s careers page.
Monthly Archives: December 2014
‘Worst virus ever’ POSTCARD hoax still circulating
[AUDIO VERSION: This is an audio version of this blog post. Click below to listen.]
During the Christmas holidays, my mother received this email from a well-meaning friend. Since her daughter works for the most trusted security company in the world, she immediately asked me about the authenticity of the message.
Here’s the email:
Subject: VIRUS COMING !
Hi All,
PLEASE FORWARD THIS WARNING AMONG FRIENDS, FAMILY AND CONTACTS!
You should be alert during the next few days. Do not open any message
with an attachment entitled POSTCARD FROM HALLMARK , regardless of who sent it to you.
It is a virus which opens A POSTCARD IMAGE, which ‘burns’ the whole
hard disc C of your computer.
This virus will be received from someone who has your e -mail address
in his/her contact list.
This is the reason you need to send this e -mail to all your contacts.
It is better to receive this message 25 times than to receive the virus
and open it.
If you receive an email entitled “POSTCARD,” even though it was sent to
you by a friend, do not open it! Shut down your computer immediately.
This is the worst virus announced by CNN.
It has been classified by Microsoft as the most destructive virus ever.
This virus was discovered by McAfee yesterday, and there is no repair
yet for this kind of Virus.
This virus simply destroys the Zero Sector of the Hard Disc, where the
vital information is kept.
COPY THIS E-MAIL AND SEND IT TO YOUR FRIENDS.
REMEMBER: IF YOU SEND IT TO THEM, YOU WILL BENEFIT ALL OF US
This particular email has been around for years, and you have probably seen one of its incarnations. Although there are real incidents of malware being distributed via e-cards, this is a bogus, unsubstantiated hoax.
 The language is quite strong – phrases like the worst virus and the most destructive virus ever are sure to get the attention of security-minded people. The problem is that the email fails to provide any authentic details to learn more about the threat, just vague announcements and classifications.
The language is quite strong – phrases like the worst virus and the most destructive virus ever are sure to get the attention of security-minded people. The problem is that the email fails to provide any authentic details to learn more about the threat, just vague announcements and classifications.
“The email doesn’t actually mention a specific virus,” said Jan Zika, an Avast Virus Lab analyst. “Sure some viruses use the “Postcard” social engineering method to trick users to click the link, but this email has been circulating for a couple of years now, and it never says which virus it is.”
The email does say what the virus can do, This virus simply destroys the Zero Sector of the Hard Disc, where the vital information is kept, and it burns the whole hard disc C of your computer. Pretty scary stuff!
“No, it cannot burn anything, and no, it is not most destructive virus ever,” said Zika. His advice? “It’s best to avoid such messages unless you can confirm that the threat is real.”
Protect yourself against email hoaxes
- Keep you antivirus protection up-to-date and scan regularly for viruses and malware. Both Avast Internet Security and Avast Premier include anti-spam filters to keep your inbox free of this kind of nonsense.
- Use caution when opening attachments or downloading files. Double check that it’s from a sender you know and trust.
- Before clicking on any links or attachments, try to verify that the email came from a legitimate source. If you can’t, then don’t click.
Multiple SQL Injections and Reflecting XSS in Absolut Engine v. 1.73 CMS
Posted by Steffen Rösemann on Dec 30
Advisory: Multiple SQL Injections and Reflecting XSS in Absolut Engine v.
1.73 CMS
Advisory ID: SROEADV-2014-08
Author: Steffen Rösemann
Affected Software: CMS Absolut Engine v. 1.73
Vendor URL: http://www.absolutengine.com/
Vendor Status: solved
CVE-ID: –
==========================
Vulnerability Description:
==========================
The (not actively developed) CMS Absolut Engine v. 1.73 has multiple SQL
injection vulnerabilities…
Security forecast for 2015
Our colleagues at PandaLabs have been making their predictions about what will be happening in the world of IT security in 2015. Do you want to know what we will be up against next year?
Security forecast for 2015
CryptoLocker
This type of malware has been in the spotlight in 2014, and these attacks are set to increase in 2015.
CryptoLocker operates in straightforward fashion: Once it gets into a computer, it encrypts all types of documents that could be valuable to the user (spreadsheets, documents, databases, photos, etc.) and blackmails the victim into paying a ransom to recover the files.
Payment is always demanded in bitcoins, so that it cannot be traced by the police, making this type of attack very attractive to cyber-criminals, as many users decide to pay in order to recover the hijacked information.
Targeted attacks
A small percentage of the millions of new malware strains that appear every month are specifically created to attack previously defined targets. These attacks, known as targeted attacks, are becoming more common and will be highly significant during 2015.
One of the greatest risks to tackle is that many companies are unaware that they could be the target of such attacks and therefore do not have appropriate measures for detecting or stopping them, or at least for detecting any anomaly and mitigating any damage as soon as possible.
Point-of-sale terminals
In 2014 we have seen an increase in attacks on the POS terminals used by all stores to accept and process customer payments.

Cyber-criminals are attacking these terminals and consequently stealing the credit card details of customers. As a result, an activity that users did not think of as a risk, such as paying at a supermarket, gas station, clothes store, etc., is starting to pose a potential threat to which hundreds of millions of people around the world have already fallen victim.
APTs
APTs (Advanced Persistent Threats) are a type of targeted attack aimed at companies or strategic institutions. Behind these attacks are usually countries that invest huge sums of money in ensuring that the targeted attack goes undetected for a long time.
Although we will not see mass APT attacks in 2015, new cases will be discovered that will have probably been around for years but will only just start coming to light.
Internet of Things
The number of Internet-enabled devices is increasing dramatically, and we are not just referring to computers or cell phones but other devices.
From IP cameras to printers, all of these ‘new’ devices that form part of the Internet share a feature that makes them a highly vulnerable target for cyber-criminals: They are devices that users do not pay much attention to and consequently, for example, they are rarely updated. As a result, as soon as a security flaw is found in the software on any one of these, compromising the device will be child’s play for any cyber-criminal. To make matters worse, these devices are connected to internal networks, home or corporate, making them ideal entry points for carrying out all types of wider attacks.
Smartphones
Smartphone attacks, or more specifically attacks on devices running Android, are going to reach new heights. Not only will the attacks increase but so will their complexity, with a single goal: to steal passwords.
We store a growing amount of data on our smartphones and cyber-criminals are going to try to get it at any cost.
Although malware on cell phones was somewhat anecdotal a couple of years ago, more malware for Android has appeared in 2014 than all of the malware targeting any mobile device ever.
It seems that in 2015 these threats will skyrocket, and the number of victims will also increase.Therefore it will be essential to use antivirus products for these devices.
You can download the full report here. ![]()
The post Security forecast for 2015 appeared first on MediaCenter Panda Security.
Three resolutions that will change tech in 2015
As we come to the end of 2014, it is time to reflect on the developments of the last 12 months and also look ahead at what improvements we can make in the year to come.
Personally, there were three major issues in technology that caught my eye in 2014 and they form the basis for my New Year’s Resolutions for 2015.
Cybersecurity and privacy
2014 was a watershed year for cybersecurity and privacy issues. With security breaches impacting many of our most trusted brands, retailers and banks (Sony, Target, Home Depot, JP Morgan Chase to name a few).
The good news is people are now more aware of online privacy. The bad news is that these attacks look to remain an issue for the foreseeable future.
In 2015, each of us has a responsibility to be the best digital citizens we can be, and do our part to protect ourselves, our privacy, our data and devices online. I’m getting involved through AVG’s Smart User Mission which aims to educate the next generation of connected people as they come online around the globe.

Photo Courtesy of Barbara Kinney, Clinton Global Initiative
As businesses, we have an ongoing responsibility to our customers to ensure their data is protected. That means upping our game in the increasingly changing and challenging cyber security environment.
Diversity in the tech industry
This important issue finally gained a much-deserved attention in 2014. Over the past year, we’ve seen Silicon Valley’s first major reporting on diversity in the workforce, after some high profile prodding by civil rights champion Rev. Jesse Jackson. Among others, a book released by Stanford scholar Vivek Wadhwa on Innovating Women and Babson College’s report on VC funding for women entrepreneurs drew further attention to the disparity issues women face in tech.
While the diversity numbers are not pretty, the good news is tackling the diversity issue in technology has gained momentum and has resulted in some positive actions; among them the Diversity 2.0 Summit and The National Venture Capital Association has taken steps to increase opportunities for women and minorities.
I am looking forward to doing my part, and I am delighted to have been selected as a speaker at the 2015 SXSW Interactive program with a Core Conversation on “Boardroom or Baby” on March 14th.
We’ve made good progress but, without doubt, there is much more to be done. I believe that in 2015 we should all make an effort to support diversity in technology. It can only bring benefits to everyone involved.
Boomers and technology
It’s hard to believe, but the last of the Baby Boomer generation (1946-1964) turned 50 this month. Last fall, the PBS series The Boomer List chronicled an amazing list of 50 people who represent the iconic generation and the impact they have had culture and our lives from arts and entertainment to science and technology, including Apple co-founder Steve Wozniak (below).
Though Boomers helped invent the digital age – and we get little credit for it – we are often viewed as neophytes and often marketed to by tech companies as novices (if, in fact, at all).

Image courtesy of technmarketing.com
My final resolution for 2015 is to do what I can to change the way that the technology talks to the older generations. I’ll start by sharing new AVG research along with my thoughts on the tech industry’s need to adapt to new and different needs of this audience during my talk on “The Fear Factor” at the 2015 International Consumer Electronics Show’s Lifelong Tech Summit on January 6 in Las Vegas. If you are attending CES, please come check it out.
Here’s to a very happy, healthy, fulfilling and safe 2015 for us all. Look forward to seeing you in the New Year!
CVE-2014-4630 (rsa_bsafe, rsa_bsafe_ssl-j)
EMC RSA BSAFE Micro Edition Suite (MES) 4.0.x before 4.0.6 and RSA BSAFE SSL-J before 6.1.4 do not ensure that a server’s X.509 certificate is the same during renegotiation as it was before renegotiation, which allows man-in-the-middle attackers to obtain sensitive information or modify TLS session data via a “triple handshake attack.”
CVE-2014-4634 (appsync, replication_manager)
Unquoted Windows search path vulnerability in EMC Replication Manager through 5.5.2 and AppSync before 2.1.0 allows local users to gain privileges via a Trojan horse application with a name composed of an initial substring of a path that contains a space character.
Cforms 14.7 Remote Code Execution
Cforms version 14.7 suffers from a remote code execution vulnerability.
On Neuroscience and Phishing Attacks
All kinds of fun facts bounce around the internet. You might have seen the one about contextual reading: It deson’t mttaer in waht oredr the ltteers in a wrod aepapr, you can sitll raed it wouthit pobelrm. See how this neuro-scientific peculiarity helps phishing criminals earn lots of money and what simple things you can do to protect yourself.
Why are URLs so important?
As I work in the URL detection team of Avira’s Protection Labs, you might not be surprised by me saying that URLs are a very important part of our daily lives. In ancient times, ten or fifteen years ago that is, data was shared through floppy disks, which were still in heavy use back then. (You know, the legacy industrial equipment that looks like the ‘Save’ button in your applications.) Times have changed and so has the industry. In today’s world, files are distributed over the Internet. File hosting services, like Dropbox and OneDrive, flourish like never before. The Internet actually consists of many subsystems like email, file sharing and the Word Wide Web. Also known as just the Web, the latter represents what you usually do in your browser: click on links, enter URLs in the browser bar, search the web; those are all examples of how you use URLs to access the Web.
What is a domain?
Avira’s domain entered in a web browser
Domains exist because they are easier to remember than IP addresses (which domains point to). They operate pretty much like a phone book. You do not remember the phone number of a person to call, you look them up in the phone book. This establishes the connection between person and callable number. While you still have to enter the number yourself on the phone, your browser will take that burden off of you. So, when you enter www.wikipedia.org in your browser, it will look up and redirect you to the proper IP address of the web server that hosts the site. If you enter www.wikkepedia.org, you will not be redirected to the site you intended to visit but rather receive a browser warning, stating that the website does not exist – just like the well-known “The person you’ve called is temporarily not available” message you hear on the phone when you dial the wrong number.
Some typos are intentional
“Where does the neuroscience bit come into play?”, you might ask. Cyber criminals are able to register this domain and host advertisements. Once you accidentally enter the wrong URL, you will be redirected to this so-called typosquatted domain and thus will have accessed ads. This in turn generates money for the advertiser. Check out my other article about online advertisements for further information. The important thing to remember is, that this is possible not due to careless surfing. It works because the human brain operates with contextual sections.
Some just want to make a few bucks by registering a misspelled domain in order to sell it back to the brand owner. One could register www.citybank.com and sell it to www.citibank.com, as this is a common misspelling.
From Malware to Phishing
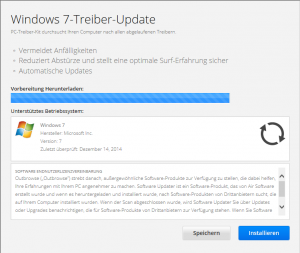
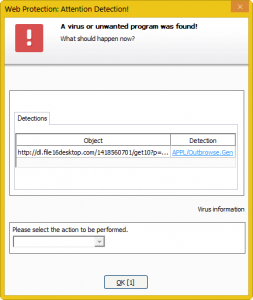
Other unfair practices include redirection to potentially unwanted applications (abbreviated PUA). Your browser will typically show a warning about the state of your computer – telling you it might be infected, your drivers might be out of date or that you have won a million dollars. To give you a practical example: I found this software recommending driver updates for my computer while going through misspelled Wikipedia links (I omit the direct URL for obvious reasons). A click on “Installieren” (region-specific, as I am browsing from Germany), tries to install the software that I do not actually intend to have on my PC. Fortunately, I am one of the lucky people having Avira security products installed. The Web Protection kicks in and saves me from accidentally installing PUA on my PC.
What to do about it?
No antimalware solution will ever give you 100% security. They are considered to provide you with something in between base and enhanced detection of malicious software on your PC. Nowadays, those programs also include effective web protection like cloud-based scanning of URLs. Avira offers both traditional antimalware solutions and an unobtrusive browser plugin to protect you against most of it. However, you should never solely rely on software to protect you. It helps a lot to know about the risks. You just might look twice the next time. ![]()
Resources and recommended reading
Breaking the Code: Why Yuor Barin Can Raed Tihs
Typosquatting
We knew the web was big…
How Big Is The Internet?
TypoSquatting – Malicious Domains Malware Domains
The post On Neuroscience and Phishing Attacks appeared first on Avira Blog.