VSAT SAILOR SAT COM 900 remote bypass administrative password changing exploit.
Monthly Archives: January 2015
FCC Warns Businesses WiFi Blocking is Illegal
In the wake of a recent enforcement action against Marriott for blocking guests’ WiFi hotspots in their hotels, the FCC is warning other hotel operators and business owners that such blocking is illegal and the commission’s Enforcement Bureau is taking note. Marriott last year paid a fine of $600,000 to settle an FCC enforcement action […]
Researcher Says Aussie Spooks Help Code Five Eyes Mega Malware
Bill Gates Warns Tech World To Watch Out For Terminators
US Tech Firms Ask China To Postpone 'Intrusive' Rules
Dutch Judge Allows Russian Hacker To Be Sent To US
Celebrity hacks – why do they continue?
This week we saw yet another hack of a top celebrity, this time the Twitter account of pop star Taylor Swift. The bad guys, whoever they are, hacked the account sent out messages, distributed personal information and claim to have personal pictures.
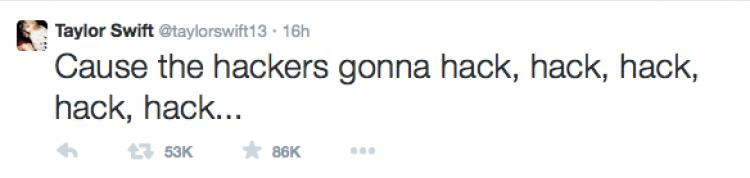
Its not uncommon for accounts to be hacked, especially when the security is reliant on just a password, but Twitter offers users much more than this.
Most online services today offer two factor authentication as an additional layer of security. The concept of this is very simple as to login you need to have something and know something. The most common use of this authentication is your ATM card, you need the card and you need to know the number.
The same theory applies on online accounts. You enter your login and password, and then the service waits for you to type in a verification number that is automatically sent to your phone. The phone is something you have and the code is something you know. Of course your phone is protected with a pin which adds yet another layer of security.
Hacking a celebrity’s account would be difficult if they switched on this two factor authentication. Here lies the problem, celebrities may tweet some things themselves, but it’s likely that they have a team managing their social media accounts for them.
Having multiple people running an account prevents the use of two factor authentication as the code can be only sent to one phone.
I am sure I just upset many celebrity fans who thought that celebrities actually managed their own social accounts. The reality is that celebrities are busy people and social networks are marketing tools that their teams use to keep them in the news.
In the case of Taylor Swift, the hack may of course be more complex and someone could have cloned her phone. This would take effort, access to the device and would have put the hackers in a much riskier environment. I hope that they have secured the data and account and that the damage is limited as no one should be hacked. Having the right security settings is the best protection.
How to set up two factor authentication
- Login in to Twitter and go to settings. If you’re on a PC then this entered by clicking on your picture in the top right corner.
- In the left hand menu select ‘Security and Privacy’
- There are a few options, SMS to a phone or using the app. Select the one of your choice.
- Scroll down and save the changes
I use the text to a phone option but either of the SMS or app options require you and your phone to be together to access your account so both offer effective protection.
Now that you have successfully enabled two factor authentication, your account should be a lot more secure.
Follow me on twitter @tonyatavg
Title image courtesy of billboard.com
Admin Alert: Kaspersky Lab Reports Twice as Many Digital Certificates Used to Sign Malware in 2014
MSIL/Agent.PYO: Have botnet, will travel
ESET’s researchers recently encountered a piece of malware targeting the filling of the forms belonging to the Consulate of Poland. To understand why it is first necessary to have a brief look at the application process for visas.
The post MSIL/Agent.PYO: Have botnet, will travel appeared first on We Live Security.
AVG Technologies to Announce Financial Results
AMSTERDAM, January 29, 2015 – AVG Technologies N.V. (NYSE: AVG) today announced it will report its fourth quarter and fiscal year 2014 financial results for the period ended December 31, 2014 following the close of market on February 18, 2015.
On that day, management will hold a webcast and conference call at 5:00 p.m. ET/2:00 p.m. PT/ 11 PM CET to review and discuss the Company’s results.
- What: AVG Technologies N.V. Fourth Quarter and Fiscal Year 2014 Financial Results Conference Call
- When: Wednesday, February 18, 2015
- Time: 5:00 p.m. ET/2:00 p.m. PT/ 11 PM CET
Live Call: Participant Access: Dial in 5-10 minutes prior to the start time using the phone numbers and Conference ID below:
+1 646 254 3363 (USA)
+1 416 216 4141 (Canada)
+44 (0)20 3427 1909 (UK)
Conference ID: 5098060
Live/ replay webcast: AVG Investors Page
About AVG Technologies (AVG)
AVG is the online security company providing leading software and services to secure devices, data and people. AVG has over 188 million active users, as of September 30, 2014, using AVG’s products and services including Internet security, performance optimization, and personal privacy and identity protection. By choosing AVG’s products, users become part of a trusted global community that engages directly with AVG to provide feedback and offer mutual support to other customers.