Monthly Archives: February 2015
Be careful with Facebook! A researcher has hacked it using a Word document
Who hasn’t checked their Facebook page from work? In addition to a distraction, it has been proved that this practice is also a risk to the security of the company. A researcher has hacked the platform using a simple Microsoft Word text document.

Mohamed Ramadan is an Egyptian hacker who discovered a bug in Facebook last July that is very dangerous for user security but that had simply gone by unnoticed; it could be hacked with a simple Word document.
It was not discovered by chance; for some time, Ramadan had been looking for possible vulnerabilities to demonstrate his potential as an ethical hacker and he had already done so by finding bugs in the Facebook apps for Android, iOS and Windows. The time had come to go one better and try with the company’s websites and servers.
He knew that this was a significant challenge; not only is it one of the technologies that have implemented the most security measures, but for years many security experts have been reporting and patching new holes. The company had even claimed that all of the holes in its servers had been patched. But it was wrong.
After thoroughly researching the topic, the hacker discovered the website Careers at Facebook, where anyone can look for work in the company and upload their CV. So, he decided to give it a go. To start checking (and find out if the platform was secure), he tried uploading a file where CVs are usually uploaded and he noticed that only .pdf or .docx files were admitted.
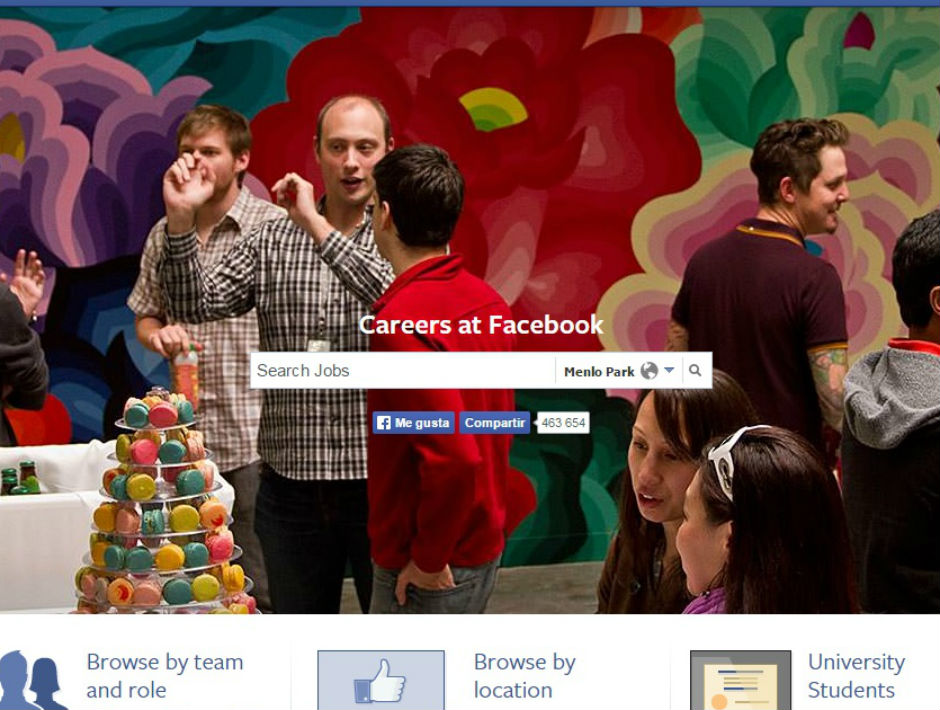
Docx files are compressed files and the data they contain can be modified if they are decompressed. So Ramadan took a .docx file and decompressed it (using the 7-zip program) in order to access its code and modify it. More specifically, he changed a line of code to command this Word document to communicate with a twin file hosted on his computer wherever it was.
Despite his good idea, Ramadan was aware that it could fail. It was probable that even if the modified document were sent to the server, the file would not be able to communicate with the twin file on his computer.
So before uploading the modified Word document to the Facebook server, he checked if it were possible to get a result from uploading this document to any other server (more specifically, to one he programmed for the purpose). The result was as expected; a few minutes after performing the test, the external server that he had just created tried to communicate with his computer, so Facebook’s would too, and it did.
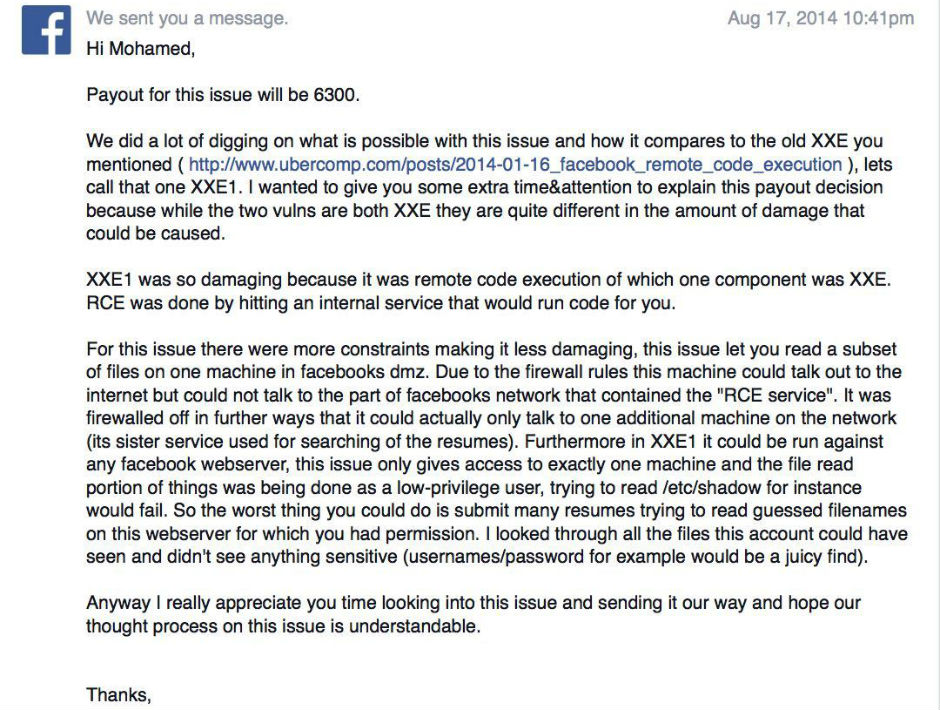
“I forced Facebook’s servers to connect to my computer using a simple Word document,” says Ramadan on his page.
With this trick Mohamed Ramadan was able to contact the data belonging to anyone who had uploaded their CV to the Facebook platform, and also their profiles on the social network and the computers that these people normally use.
Therefore, any company’s data could be compromised if its employees use Facebook at work from the company’s computers. In this case the page that had the problem was Careers at Facebook and fortunately, it was Ramadan who detected it. However, the vulnerability on this server could have affected many others, according to the expert.
Although the bug has been fixed – and Ramadan has collected a reward of $6300 – its existence shows that compromising Facebook accounts is easier than it seems.
The post Be careful with Facebook! A researcher has hacked it using a Word document appeared first on MediaCenter Panda Security.
Canary Watch Site Launches to Track Warrant Canaries
In the years since Edward Snowden began putting much of the NSA‘s business in the street, including its reliance on the secret FISA court and National security Letters, warrant canaries have emerged as a key method for ISPs, telecoms and other technology providers to let the public know whether they have received any secret orders. But […]
Kaspersky Anti-Virus Engine to be Integrated into GBS’ Flagship Product
Hacked dating website Topface buys back stolen personal data from hacker
A Russian dating website that had 20 million email addresses stolen last week, has paid the hackers not to sell the information, TechWeek Europe reports.
The post Hacked dating website Topface buys back stolen personal data from hacker appeared first on We Live Security.
The New Hacker’s List and an Old Debate: Would you Hire Hackers or Not?
The recent opening of the Hacker List portal brings to mind the age-old question: Would you hire a hacker?
The post The New Hacker’s List and an Old Debate: Would you Hire Hackers or Not? appeared first on We Live Security.
BMW fixes security flaw that left more than 2 million cars unlocked
BMW has patched a bug in its ConnectedDrive system that left 2.2 million cars vulnerable to being hacked and unlocked.
The post BMW fixes security flaw that left more than 2 million cars unlocked appeared first on We Live Security.
Apps on Google Play Pose As Games and Infect Millions of Users with Adware
A couple of days ago, a user posted a comment on our forum regarding apps harboring adware that can be found on Google Play. This didn’t seem like anything spectacular at the beginning, but once I took a closer look it turned out that this malware was a bit bigger than I initially thought. First of all, the apps are on Google Play, meaning that they have a huge target audience – in English speaking and other language regions as well. Second, the apps were already downloaded by millions of users and third, I was surprised that the adware lead to some legitimate companies.
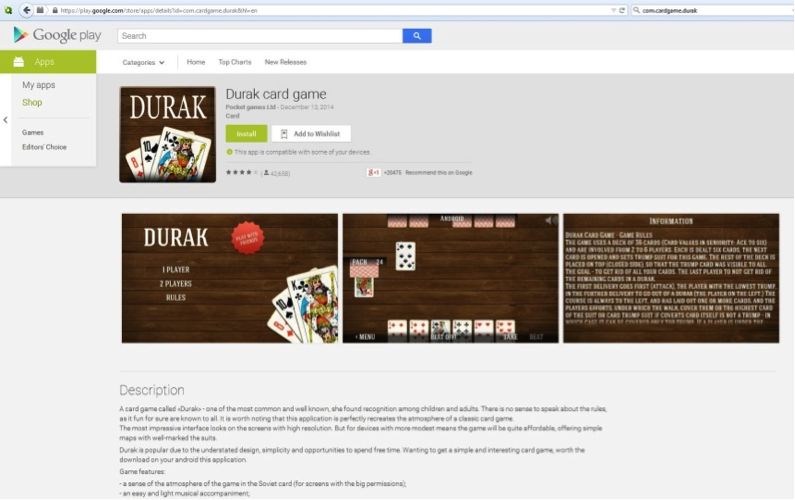 The Durak card game app was the most widespread of the malicious apps with 5 – 10 million installations according to Google Play.
The Durak card game app was the most widespread of the malicious apps with 5 – 10 million installations according to Google Play.

When you install Durak, it seems to be a completely normal and well working gaming app. This was the same for the other apps, which included an IQ test and a history app. This impression remains until you reboot your device and wait for a couple of days. After a week, you might start to feel there is something wrong with your device. Some of the apps wait up to 30 days until they show their true colors. After 30 days, I guess not many people would know which app is causing abnormal behavior on their phone, right? ![]()
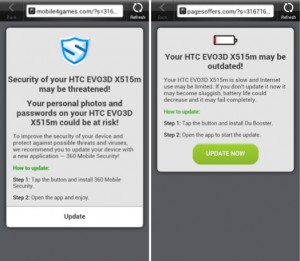 Each time you unlock your device an ad is presented to you, warning you about a problem, e.g. that your device is infected, out of date or full of porn. This, of course, is a complete lie. You are then asked to take action, however, if you approve you get re-directed to harmful threats on fake pages, like dubious app stores and apps that attempt to send premium SMS behind your back or to apps that simply collect too much of your data for comfort while offering you no additional value.
Each time you unlock your device an ad is presented to you, warning you about a problem, e.g. that your device is infected, out of date or full of porn. This, of course, is a complete lie. You are then asked to take action, however, if you approve you get re-directed to harmful threats on fake pages, like dubious app stores and apps that attempt to send premium SMS behind your back or to apps that simply collect too much of your data for comfort while offering you no additional value.
An even bigger surprise was that users were sometimes directed to security apps on Google Play. These security apps are, of course, harmless, but would security providers really want to promote their apps via adware? Even if you install the security apps, the undesirable ads popping up on your phone don‘t stop. This kind of threat can be considered good social engineering. Most people won‘t be able to find the source of the problem and will face fake ads each time they unlock their device. I believe that most people will trust that there is a problem that can be solved with one of the apps advertised “solutions” and will follow the recommended steps, which may lead to an investment into unwanted apps from untrusted sources.
Avast Mobile Premium detects these apps, protecting its users from the annoying adware. Additionally, the apps’ descriptions should make users skeptical about the legitimacy of the apps. Both in English and in other languages such as German, were written poorly: “A card game called ‘Durak‘ – one of the most common and well known game“.
The apps‘ secure hash algorithm (SHA256) is the following: BDFBF9DE49E71331FFDFD04839B2B0810802F8C8BB9BE93B5A7E370958762836 9502DFC2D14C962CF1A1A9CDF01BD56416E60DAFC088BC54C177096D033410ED FCF88C8268A7AC97BF10C323EB2828E2025FEEA13CDC6554770E7591CDED462D
Passwords aren’t enough for small business security
From Target to Sony Pictures, security breaches at businesses of all sizes were in the headlines throughout 2014. We are only in February but the data breach stories show no sign of abating.
Whether it’s a specific hacking attack on a British shoe retailer or hacktivism at companies with millions of online members, the loss or compromise of passwords is frequently a common factor.
Ever since they emerged in the late ‘90s, passwords have been our primary security measure. Fast forward to today and we often find that employees are still routinely using the same style of basic password – except now these passwords are required to protect smartphones and tablets carrying sensitive company-related data, as well as social media and cloud-based applications used regularly in the workplace.
It’s clear that conventional password use is no longer fit for 21st century purpose and businesses must adopt additional measures to ensure their passwords are up to the task.
Extra levels of authentication are needed to verify the identity of employees using their passwords, and businesses should start to enforce these as standard within their organization especially if they have in place bring your own device (BYOD) policies.
AVG has created this short eBook to help you develop a BYOD policy that fits your business:
In my view, many of the user identity breaches reported in the news could have been prevented with better password practices and stronger, multi-factor authentication methods.
Five top tips for more effective password management in 2015:
- Make sure security measures include formal staff training on password best practice. Passwords need to be strong, long and as secure as possible – complicate them by using “passphrases” rather than individual words – e.g. rather than “spotthedog” use “5p0tth360g”
- There is no harm in turning on “two-step authentication”. Most services are offering this now and is a simple code based system that send you a numeric password by SMS/Text to secure you login credentials
- Create a single profile for all corporate log-ins, with segmented privileges for individual employees within the same profile. This way, when someone leaves the company, they can be removed automatically.
- Some mobile phones now provide both identity and access management capabilities. Encourage employees to adopt these and incorporate them as part of your BYOD policy.
- To aid productivity, make it easier for employees to work anywhere, anytime with mobile technology by moving to a single sign-on environment where every employee has one-click to access to a secure area in the cloud containing all of their work accounts and applications.
This constant flow of data breach stories in the media has done much to raise awareness of the issues around passwords. Education is positive, of course, but action must be taken to foil the hackers.
If your business is supported by a mobile workforce equipped with either work or personal devices which provide ready access to company-sensitive systems and information, ask yourself that important question: what password practices do I need to implement to keep those devices and that data secure?
Don’t take it for granted that your people have the knowledge to handle this themselves. Instead make sure you equip them to help protect your company.
MSA-2015-02: Hewlett-Packard UCMDB – JMX-Console Authentication Bypass
Posted by Advisories on Feb 03
Mogwai Security Advisory MSA-2015-02
———————————————————————-
Title: Hewlett-Packard UCMDB – JMX-Console Authentication
Bypass
CVE-ID: CVE-2014-7883
Product: Hewlett-Packard Universal CMDB (UCMDB)
Affected versions: UCMDB 10.10 (Other versions might also be affected)
Impact: high
Remote: yes
Product link:…
