Resolved Bugs
1193945 – CVE-2015-1572 e2fsprogs: potential buffer overflow in closefs() (incomplete CVE-2015-0247 fix)
1193947 – CVE-2015-1572 e2fsprogs: potential buffer overflow in closefs() [fedora-all]
1194063 – [abrt] e2fsprogs: strlen(): dumpe2fs killed by SIGSEGV
1170803 – calls e2fsck on all ext volumes, provides no status indicator, and hangs indefinitely if e2fsck doesn’t exit
963283 – e2fsck.conf makes e2fsck ignore check intervals
1192861 – e2fsck seg faults on 6TB HDD<br
– Fix potential buffer overflow in closefs (#1193947, CVE-2015-1572)
– Fix dumpe2fs segfault with no arguments (#1194063)
– Don’t require fsck prior to resize2fs -P (#1170803)
Changes e2fsck.conf so that for filesystems with time-based check intervals set in the superblock, these time-based checks will work again. You may need to wait through an e2fsck on your next reboot in this case.
Monthly Archives: February 2015
Fedora 20 Security Update: e2fsprogs-1.42.12-3.fc20
Resolved Bugs
1193945 – CVE-2015-1572 e2fsprogs: potential buffer overflow in closefs() (incomplete CVE-2015-0247 fix)
1193947 – CVE-2015-1572 e2fsprogs: potential buffer overflow in closefs() [fedora-all]
1194063 – [abrt] e2fsprogs: strlen(): dumpe2fs killed by SIGSEGV
1170803 – calls e2fsck on all ext volumes, provides no status indicator, and hangs indefinitely if e2fsck doesn’t exit<br
– Fix potential buffer overflow in closefs (#1193947, CVE-2015-1572)
– Fix dumpe2fs segfault with no arguments (#1194063)
– Don’t require fsck prior to resize2fs -P (#1170803)
Fedora 20 Security Update: samba-4.1.17-1.fc20
Update to Samba 4.1.17 to address CVE-2015-0240 – RCE in netlogon.
Fedora 21 Security Update: qpid-cpp-0.30-11.fc21
Resolved Bugs
1186308 – CVE-2015-0223 qpid-cpp: anonymous access to qpidd cannot be prevented
1181721 – CVE-2015-0203 qpid-cpp: qpidd can be crashed by unauthenticated user
1184488 – build failure in qpid-cpp-0.30/src/tests/txshift.cpp<br
Fixed path to qpid-ha in the systemd service descriptor.
Resolves: BZ#1186308
Apply patch 10.
Resolves: BZ#1184488
Resolves: BZ#1181721
Fedora 21 Security Update: samba-4.1.17-1.fc21
Update to Samba 4.1.17 to address CVE-2015-0240 – RCE in netlogon.
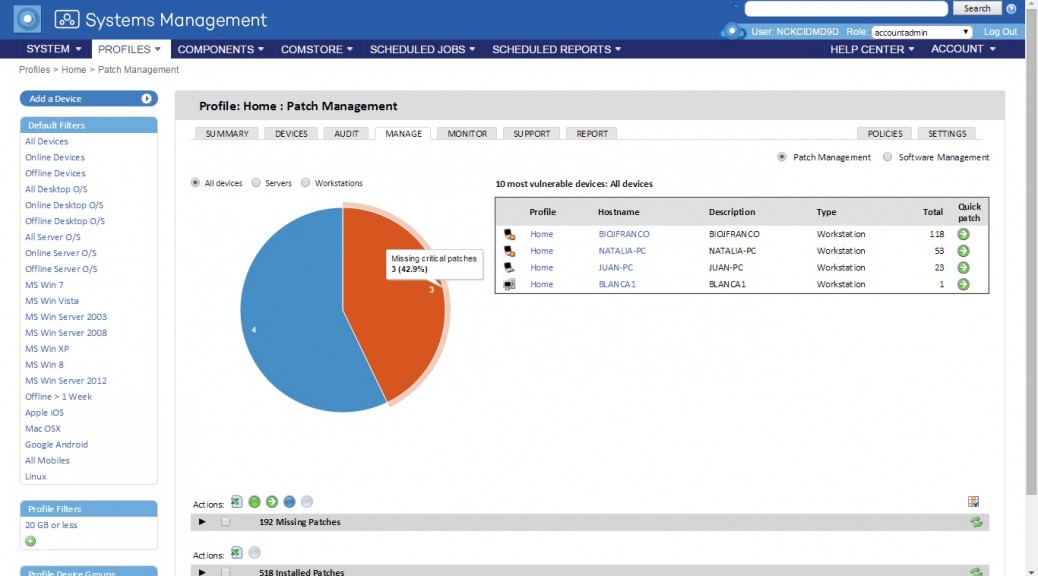
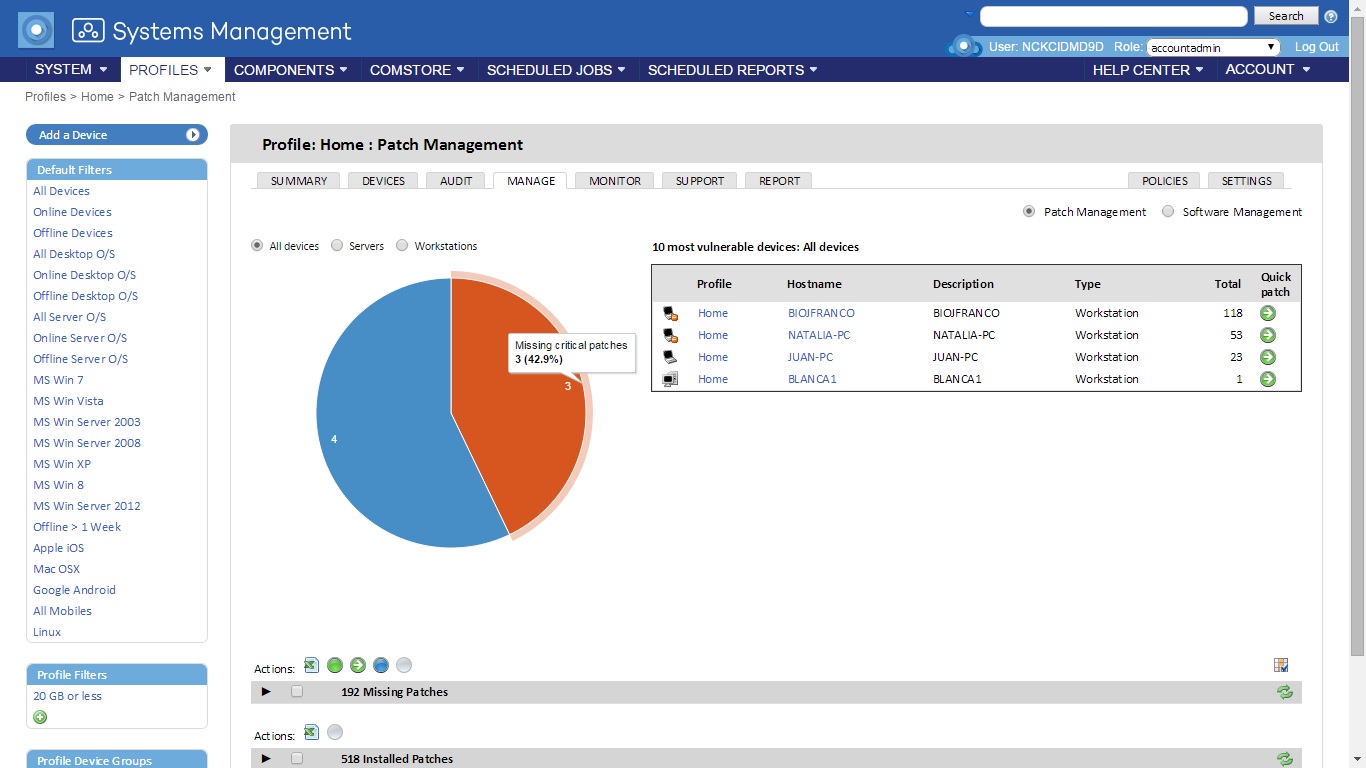
Systems Management strengthens its capabilities to control all types of devices
Panda Security announces the features of the new version of Systems Management, the cross-platform solution that allows you to manage, monitor and provide support to all types of devices from a web console, inside or outside the network.
The latest version of Systems Management includes new features that allow simple and centralized management. One of its main features is that agents can be installed remotely from the web management console. Once a Systems Management agent has been installed on a device, it will automatically detect network computers that do not have Systems Management in order to install it at a click. Another of its key features is the ability to add individual patches to the policies created, offering greater control in patch management.
Greater security for iOS phones
In addition to the features currently supported on smartphones and tablets, which allow you to carry out a hardware and software inventory, geolocalize them and wipe them remotely; the security of iOS devices can be significantly strengthened by defining the characteristics of the passwords set by the user. Furthermore, functions can be blocked, such as installing games and apps to ensure more productive use of the device and the VPN and Wi-Fi settings of handsets can be configured centrally.
“The new features of Systems Management offer companies simpler management and increase user productivity”, says Manuel Santamaría, Product Manager Director at Panda Security. “All of this results in cost reduction, favouring independence of the IT administrator and providing the best security for the client’s IT network”, he concludes.
The post Systems Management strengthens its capabilities to control all types of devices appeared first on MediaCenter Panda Security.
Top 10 breaches of 2014 attacked ‘old vulnerabilities’, says HP
A report by HP has found that 44 percent of all of the breaches in 2014 were caused by known vulnerabilities, between two and four years old.
The post Top 10 breaches of 2014 attacked ‘old vulnerabilities’, says HP appeared first on We Live Security.
FreeBSD-SA-15:04.igmp
FreeBSD-SA-15:05.bind
CESA-2015:0265 Critical CentOS 7 firefox SecurityUpdate
CentOS Errata and Security Advisory 2015:0265 Critical Upstream details at : https://rhn.redhat.com/errata/RHSA-2015-0265.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) x86_64: bb5ccc0f99270fe4513cf433de7780f18e00d24a2c544050c4b7bb45cd1e40b0 firefox-31.5.0-2.el7.centos.i686.rpm 59ef15c77888ba36e166177960ae34ccd135d22157d9306f3ef31722e8dd3afc firefox-31.5.0-2.el7.centos.x86_64.rpm 97efe63b7aab8bcbbdf17cba51aea4a68662755181b79feff8bb9fa0a845f348 xulrunner-31.5.0-1.el7.centos.i686.rpm b232b11d86bcd3017c1becbb0727f5a84bea5b95a30a58e29b289a64e069022f xulrunner-31.5.0-1.el7.centos.x86_64.rpm b79179ace2c967097f99a7f14cb4ee68af720248521cc10afd9ceae277f406f9 xulrunner-devel-31.5.0-1.el7.centos.i686.rpm 8721c0fad03ab5ef877200787bea9ba354ac97bba1474bd2db65bf6858bf4f4b xulrunner-devel-31.5.0-1.el7.centos.x86_64.rpm Source: 02135f20d1e24d14b2b587de7242900d57a504133eca7d97bdae81e52db1a87d firefox-31.5.0-2.el7.centos.src.rpm 5df824f2eed96f62e869beb42ca1cd4486a5936cede043598c1bf762ff76d939 xulrunner-31.5.0-1.el7.centos.src.rpm