-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:202 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : ntp Date : April 10, 2015 Affected: Business Server 1.0, Business Server 2.0 _______________________________________________________________________ Problem Description: Multiple vulnerabilities has been found and corrected in ntp: The symmetric-key feature in the receive function in ntp_proto.c in ntpd in NTP before 4.2.8p2 requires a correct MAC only if the MAC field has a nonzero length, which makes it easier for man-in-the-middle attackers to spoof packets by omitting the MAC (CVE-2015-1798). The symmetric-key feature in the receive function in ntp_proto.c in ntpd in NTP before 4.2.8p2 performs state-variable updates upon receiving certain invalid packets, which ma
Monthly Archives: April 2015
[ MDVSA-2015:201 ] arj
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:201 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : arj Date : April 10, 2015 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: Multiple vulnerabilities has been found and corrected in arj: Jakub Wilk discovered that arj follows symlinks created during unpacking of an arj archive. A remote attacker could use this flaw to perform a directory traversal attack if a user or automated system were tricked into processing a specially crafted arj archive (CVE-2015-0556). Jakub Wilk discovered that arj does not sufficiently protect from directory traversal while unpacking an arj archive containing file paths with multiple leading slashes. A remote attacker
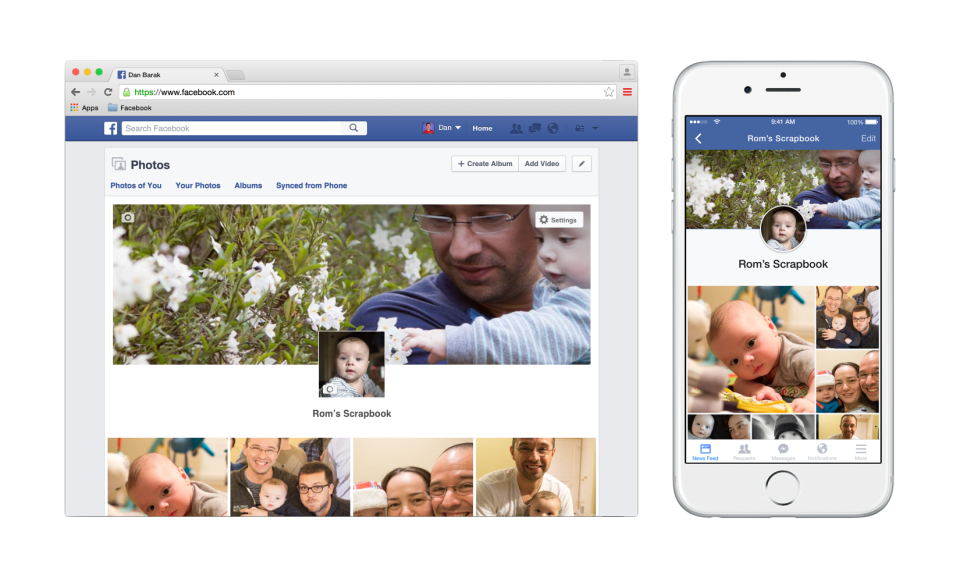
Facebook introduce Scrapbook for baby photos
On March 31st, Facebook began rolling out its new “Scrapbook” feature which loving parents can fill with pictures of their children without fear of flooding their friends’ Facebook feed.
While this is great news for those of us who loathe oversharing, it also makes it easier for parents to manage their privacy. By placing all their images in a Scrapbook, parents can easily control who can and cannot view them.
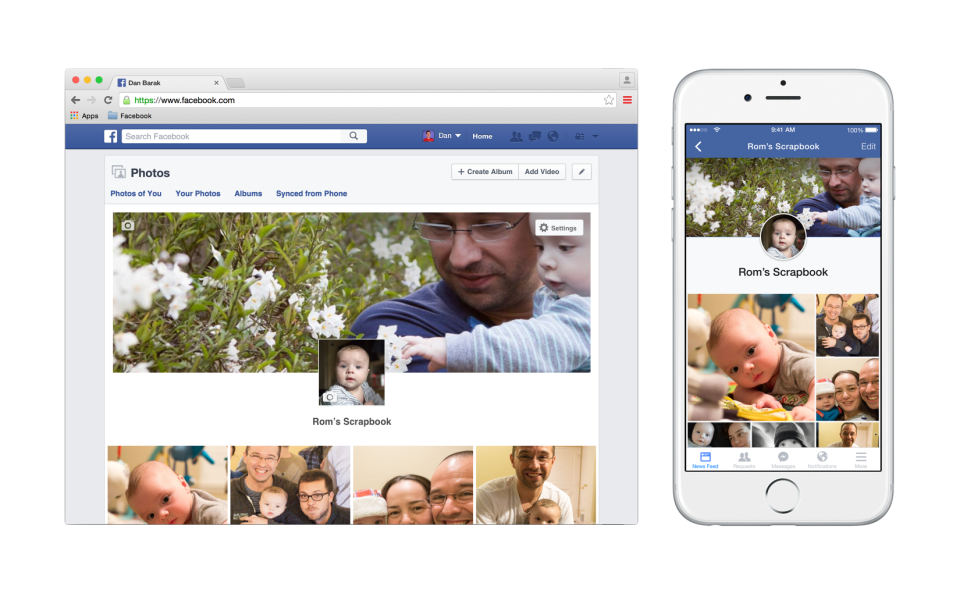
Scrapbook addresses the very clear demand for parents to document, store and share precious memories and highlights the trends that we highlighted in Digital Diaries research.
In fact, as many as 30% of parents have shared a pre-natal scan via social media, creating a Digital Footprint for their child long before they are even born.
And it doesn’t stop there; later stages of Digital Diaries highlight the sharenting phenomenon where parents don’t consider the long term consequences of sharing every detail of their child’s life.
Scrapbook may help parents keep a handle on the visibility of their baby photos but as such is exacerbating the sharenting issue.
Today’s children are growing up in digital world that doesn’t forget and a world where their every moment is being captured and stored on line. Before we share anything, it’s important to remember that.
![]()
![]()
[ MDVSA-2015:200 ] mediawiki
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:200 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : mediawiki Date : April 10, 2015 Affected: Business Server 1.0 _______________________________________________________________________ Problem Description: Updated mediawiki packages fix security vulnerabilities: In MediaWiki before 1.23.9, one could circumvent the SVG MIME blacklist for embedded resources. This allowed an attacker to embed JavaScript in the SVG (CVE-2015-2931). In MediaWiki before 1.23.9, the SVG filter to prevent injecting JavaScript using animate elements was incorrect (CVE-2015-2932). In MediaWiki before 1.23.9, a stored XSS vulnerability exists due to the way attributes were expanded in MediaWiki's Html class, in combination with LanguageCo
[ MDVSA-2015:199 ] less
-----BEGIN PGP SIGNED MESSAGE----- Hash: SHA1 _______________________________________________________________________ Mandriva Linux Security Advisory MDVSA-2015:199 http://www.mandriva.com/en/support/security/ _______________________________________________________________________ Package : less Date : April 10, 2015 Affected: Business Server 1.0, Business Server 2.0 _______________________________________________________________________ Problem Description: Updated less package fixes security vulnerability: Malformed UTF-8 data could have caused an out of bounds read in the UTF-8 decoding routines, causing an invalid read access (CVE-2014-9488). _______________________________________________________________________ References: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-9488 http://advisories.mageia.org/MGASA-2015-0139.html _______________________________________________________________________ Updated Packages: Mandriva Business Server
WebDAV Uploading Script
Simple PHP script that explores WebDAV vulnerable sites that allow arbitrary uploads.
Fedora 21 Security Update: qpid-cpp-0.32-1.fc21.1
Resolved Bugs
1186308 – CVE-2015-0223 qpid-cpp: anonymous access to qpidd cannot be prevented
1181721 – CVE-2015-0203 qpid-cpp: 3 qpidd DoS issues in AMQP 0-10 protocol handling
1184488 – build failure in qpid-cpp-0.30/src/tests/txshift.cpp<br
Bumped the release to force a build against Proton 0.9 in F22.
Added qpidtoollibs to the qpid-tools package.
Fixed path to qpid-ha in the systemd service descriptor.
Resolves: BZ#1186308
Apply patch 10.
Resolves: BZ#1184488
Resolves: BZ#1181721
Fedora 20 Security Update: netcf-0.2.8-1.fc20
Resolved Bugs
1172176 – CVE-2014-8119 netcf: augeas path expression injection via interface name
1207396 – CVE-2014-8119 netcf: augeas path expression injection via interface name [fedora-all]<br
Security fix for CVE 2014-8119, as well as adding a few other minor bugfixes and enhancements (support for multiple IPv4 addresses, simultaneous static & dhcp for IPv4)
[Tool] nsec3map v0.3 – DNSSEC Zone Enumerator
Posted by An Onion on Apr 10
nsec3map is a DNS zone enumerator that makes use of DNSSEC NSEC or NSEC3
records. It allows to discover hosts quickly and with a minimal number
of DNS queries (usually just one query per resource record).
In NSEC mode, it can be configured to send “A” queries, which can be
useful in cases where the nameserver blocks the direct querying of NSEC
records.
In NSEC3 mode, the tool finds a domain name which is not covered
by any received…
DSA-3218 wesnoth-1.10 – security update
Ignacio R. Morelle discovered that missing path restrictions in the
Battle of Wesnoth
game could result in the disclosure of arbitrary
files in the user’s home directory if malicious campaigns/maps are
loaded.