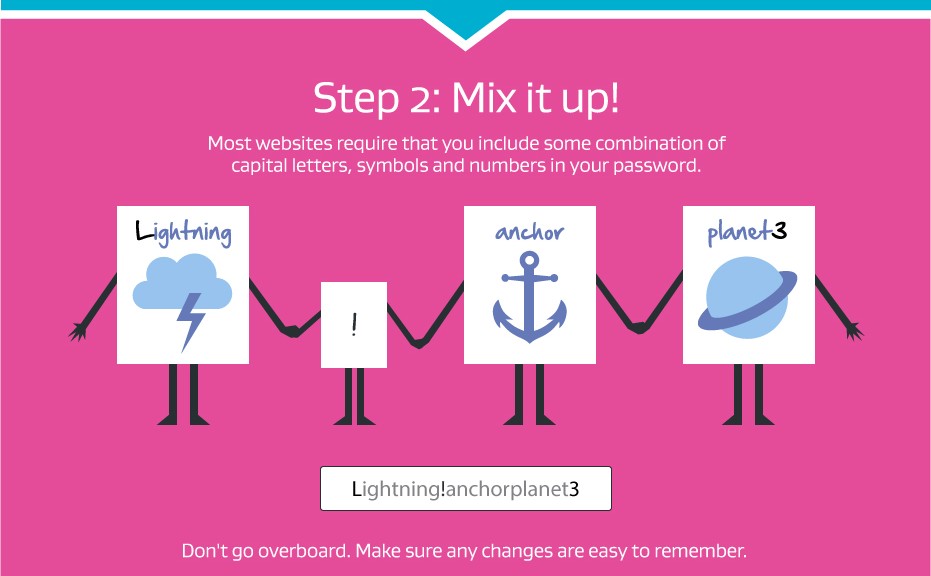
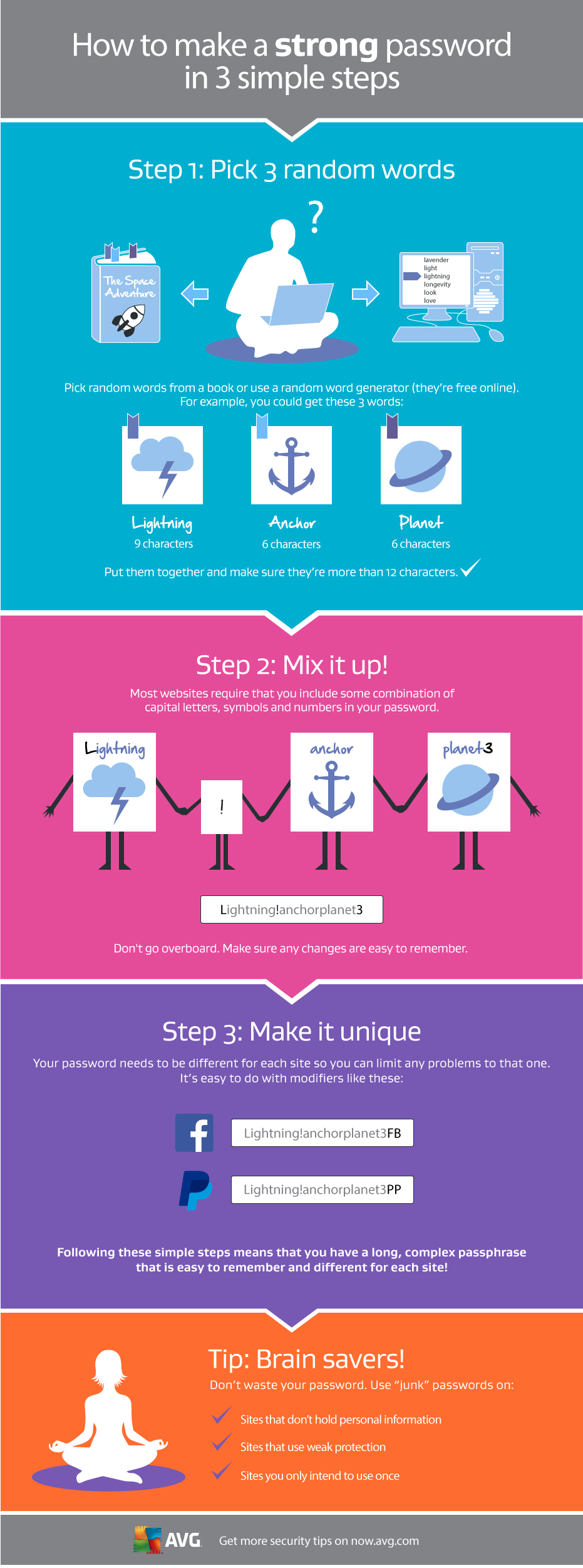
Bad news if you are a customer of Carphone Warehouse, a leading UK retailer for mobile phones and call plans. Late last week, the company announced that it had suffered a large data breach affecting as many as 2.4 million customers.
The information leaked includes names, addresses, dates of birth and bank details. While as many as 90,000 encrypted credit card details were also stolen.
In a statement, Sebastian James, group chief executive of Dixons Carphone, said:
“We take the security of customer data extremely seriously, and we are very sorry that people have been affected by this attack on our systems.
“We are, of course, informing anyone that may have been affected, and have put in place additional security measures.”
“We took immediate action to secure these systems and launched an investigation with a leading cyber security firm to determine exactly what data was affected.”
If you think that you are potentially affected by this hack, here are two things that you should do as soon as possible to help mitigate any risk posed by unauthorized access to your bank accounts or credit cards.
Suspend your credit card
Naturally, one of the first things you should do is contact your credit card issuer and suspend your card. This means that you’re no longer vulnerable to credit card fraud if the card number has been stolen.
Your bank will issue a new credit card with a new number that wasn’t compromised in a breach.
Set up ID monitoring
I also highly recommend registering with an ID monitoring service. These scour the web searching for your credentials whenever and wherever they pop up. This allows you to take preemptive action against potential scammers.
There are instances of this being offered to data breach victims for free. Target did just that last year after their large hack. Should Carphone Warehouse contact you to say you’re information has been leaked, you should ask them about a similar service.
Beware of more scams
A word of caution, we’re likely to see some phishing attempts from fraudsters offering remedial services for data breach victims. Be very cautious about any email that arrives talking about compensation or other enticing services. Double check that any correspondence you receive is directly from Carphone Warehouse. If in doubt, contact them directly yourself rather than opening a suspicious email.
![]()
![]()