Monthly Archives: April 2015
Media Alert: Kaspersky Lab Channel Sales Executive to Speak at Channel Focus North America
Using Technology to Celebrate Earth Day 2015
Given the enormous swings in climate change we are witnessing around the world, Earth Day takes on more meaning for many of us than ever before. Whether you acknowledge climate change, or not, protecting Mother Earth should be an imperative for us all. Here’s a reminder for all of us living in the tech world about a few steps we can take to help protect the earth:
Recycle your technology
If you have an old cell phone or smartphone that you can donate for a good cause, that’s a wonderful place to start. Carrier Verizon, for example, has a program where your donation aids victims of domestic violence. It’s safe to recycle or donate smartphones, just be sure to wipe the device and take out the memory card first!
For those of us who work from home, many of us have printers and accumulate empty printer cartridges that can pile up. You don’t want those to end up in a landfill, though sadly, millions do…to the tone (sorry for the pun) of 350 million a year, according to Cartridge World. So please contact your equipment manufacturers about recycling programs. For example, HP has a robust program.
In the UK, Recycle4charity is an initiative that works with dozens of charities to generate donations from recycling old mobiles and printer cartridges.
For more advice on recycling technology check out CNet’s latest report. And, iRecycle by Earth911 is a free app on both Android and iOS that details more than 1,600,000 ways to recycle more than 350 materials.
There’s an app for that…
An ever-growing number of eco-friendly apps out there can help us protect the planet. By one estimate from IBM’s Smarter Planet there were 400 million green-related apps downloaded in 2014. That’s a lot of apps!
Here are a few of my favorites:
- Monitor & reduce your energy consumption. By now, most people are familiar with the Nest thermostat to monitor and control your home thermostat. But there are many other examples such as The Wiser Energy Management System, by Schneider Electric. It’s a home energy management solution that lets you track and control your energy expenditures (and thus your costs).
- Eliminate junk mail. How often do you find your mailbox still cluttered with junk mail? PaperKarma by Reputation.com is a free app that allows you to take a picture of the unwanted mail, and then handles it from there, contacting the distributor and cancelling further contact.
- Travel energy-wise. Carma Carpool is an app available for free to cut down on costs, traffic jams, greenhouse gas emissions and overall pollution. Carma enables you to find rides and share your commute in many major cities in the U.S. and Ireland, as well as Oslo. It’s also a great way to use the Diamond lane, and the San Francisco Bay Area you get free tolls!
- Shop eco-wise. Many of us also like to shop for eco-friendly products in environmentally friendly stores. GoodGuides, which I’ve mentioned before, is a free app that helps you find health, environmental, and social performance ratings for over 120,000 food, personal care, and household products — from baby shampoo to bathroom cleaner.
- Get the game. Finally, the Earth Day Network has announced it will work developers of the “Angry Birds” game to create a game experience, called “Champions for Earth” to raise environmental awareness. Stay tuned. The game is due out in the fall.
I hope some of these ideas will help inspire you to celebrate Earth Day this Wednesday and every day.
![]()
![]()
Canada commits $36.4 million to cybersecurity measures in 2015 budget
The Conservatives’ 2015-16 federal budget sees some investment in security, with $36.4 million promised over five years to address cybersecurity threats.
The post Canada commits $36.4 million to cybersecurity measures in 2015 budget appeared first on We Live Security.
![]()
HomeAdvisor Bug Bounty #1 – Filter Bypass & Client Side Exception Handling Vulnerability
Posted by Vulnerability Lab on Apr 22
Document Title:
===============
HomeAdvisor (Bug Bounty #1) – Filter Bypass & Client Side Exception Handling Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1452
Release Date:
=============
2015-04-21
Vulnerability Laboratory ID (VL-ID):
====================================
1452
Common Vulnerability Scoring System:
====================================
3.6
Product & Service…
Panda Antivirus 2015 latest update: all about our three great innovations

If you are reading this after being informed by your computer that your product has been automatically updated, probably by now you have realized we have a new look&feel.
The panda bear located next to your PC’s clock which has always looked after your security while you enjoyed your online freedom has changed its looks to better represent our new corporate identity. Now we are Simplexity!
This new version 15.1, of consumer products, integrates some other important improvements like:
- Improvement of our XMT engine, it has now greater protection capacity against new threats. To prove this we just have to look at the latest results obtained in the last Real World Protection Test carried out by AV-Comparatives, in which this new version detected 99, 8% of the threats, that’s an excellent result!
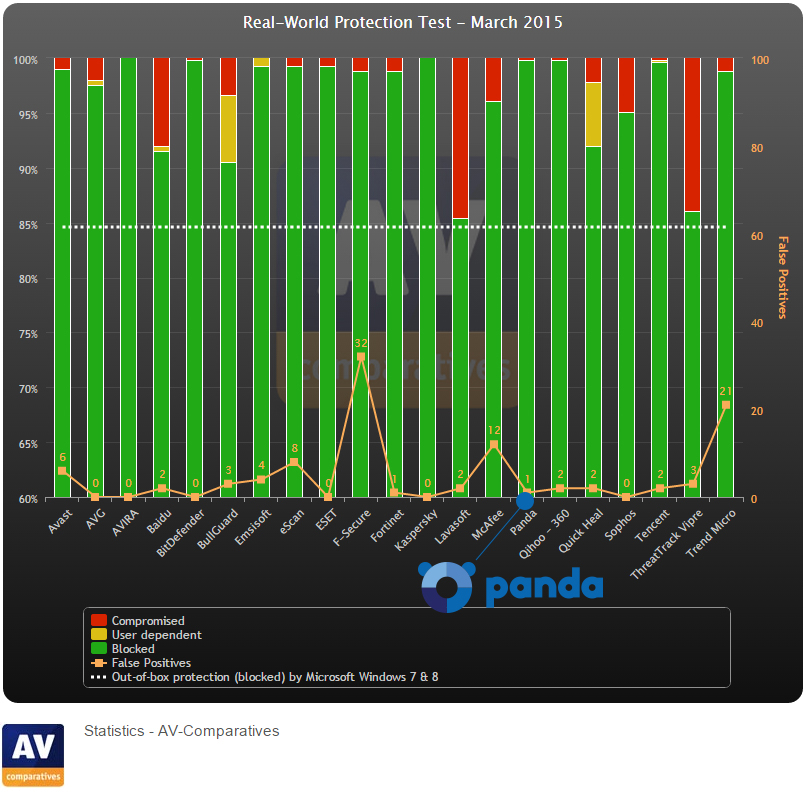
- Product performance maximization, integrating file copies and network analysis optimizations.
- The possibility of launching the virtual keyboard from the new icon’s menu and Parental Control predefined profiles (available in Panda Internet Security and higher), are some of the improvements included in our paid products.
As you can see, we keep adapting and improving our services after receiving our users’ community feedback.
You are the reason we keep working to improve our security solutions in all devices! In the next few weeks we will announce new features… Stay tuned!
The post Panda Antivirus 2015 latest update: all about our three great innovations appeared first on MediaCenter Panda Security.
CVE-2015-1484
Unquoted Windows search path vulnerability in the agent in Symantec Workspace Streaming (SWS) 6.1 before SP8 MP2 HF7 and 7.5 before SP1 HF4, when AppMgrService.exe is configured as a service, allows local users to gain privileges via a Trojan horse executable file in the %SYSTEMDRIVE% directory, as demonstrated by program.exe.
CVE-2015-1889
The Big SQL component in IBM InfoSphere BigInsights 3.0 through 3.0.0.2 allows remote authenticated users to bypass intended HDFS data-access restrictions via (1) a crafted CREATE HADOOP TABLE statement referencing the data of an arbitrary user or (2) an import of a certain Hive table definition with the HCAT_SYNC_OBJECTS procedure.
Mass emails without BCC and other unsafe (and illegal) habits

Either by mistake or ignorance, your company may be facing a hefty fine. You may ask yourself why? The answer, the daily emails your employees send to multiple clients massively. Do they send them using blind carbon copy (bcc)?
Inside the Spanish Organic Law on Personal Data Protection (LOPD) lies the exact explanation to why one of those emails sent to multiple clients without concealing their addresses may cost your company dear.
When managing a company’s client data base the responsibility is to protect them. This consists on not sharing or selling their information to others, people or companies. Here lays the problem with emails sent without bcc, every recipient can see who has received that same email which according to the LOPD is a serious offense.
It can turn out to be a very expensive mistake, if any of the recipients decided to report your company. The law provides fines between 40.000 and 300.000 euros, although normally sanctions end up being lower, depending on the number of affected clients or on how many times the mistake had been committed.
How to avoid it?
If you want to avoid making this mistakes is as simple as paying a bit of attention when sending mass emailing. Just add the recipients’ addresses through the Bcc button which is on the email top bar. This way the recipients’ addresses will be hidden and won’t be visible to those who had received that same email.
However, mass mailing without adding the recipients to the Bcc list is not the only problem a company might have while communicating, their presence in social networks can play an important role if used without caution.
We find Twitter is the most problematic one. If a company decided to follow unilaterally other users it may be breaking the Spanish Organic Law on Personal Data Protection and the Law of Services of the Information Society. You may wonder why? The reason is that a simple “follow” on Twitter is considered a commercial communication. And if the communication hadn’t been previously approved by the other user we will be looking at a case of spam.

In this case the solution is also simple, though it may be a bit painful for companies that will no longer be able to follow thousands of Twitter users. To do so and not be considered spam, companies must previously obtain the other users’ consent. In this case, the user following the company’s Twitter account may be understood as the necessary consent.
The whole company must be aware of the information its employees handle daily, everyone else’s information must be also protected, especially online. Something as simple as sending emails using bcc or choosing who our company follows on Twitter, may be enough to protect the information of others, and to avoid penalty.
The post Mass emails without BCC and other unsafe (and illegal) habits appeared first on MediaCenter Panda Security.
Android 0-day vulnerability – Drive by download
Posted by ma sh on Apr 22
Security Issue:
===============
It is possible to fool Android users into performing
undesired actions on their devices.
Namely, it is possible to force them downloading
malicious applications without being aware of it.
It seems to affect all versions of Android.
Reference (source):
===================
http://www.nes.fr/securitylab/?p=1865
Proof Of Concept:
=================
https://www.youtube.com/watch?v=ekvdO8tdJ34

