CentOS Errata and Security Advisory 2015:0864 Important Upstream details at : https://rhn.redhat.com/errata/RHSA-2015-0864.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: 31b24c742e30d03eef068ac51f1ca07f5c3a02c4f4a988b4519a533b7dfb8c71 kernel-2.6.32-504.16.2.el6.i686.rpm 06a5262def11bbeee0572101b4b4243c5a31a55a4f45ea33f9ebbfa6cde30bc9 kernel-abi-whitelists-2.6.32-504.16.2.el6.noarch.rpm 8077fb249341e2a249345846384ad3d91916845ad0bd8a8ea4529ddf135bc59e kernel-debug-2.6.32-504.16.2.el6.i686.rpm 536ab05730074c92af1fbfdc5da7c21830637199c1aba53bcf760ddb3297adb4 kernel-debug-devel-2.6.32-504.16.2.el6.i686.rpm c04ee8bffa8b5165ca9695b43c57ee1f95916a229fa1aeddfc3a084fb8d26826 kernel-devel-2.6.32-504.16.2.el6.i686.rpm 3a5fec20c360b962eb6899bbafbad30fd135badfdf90b77276eb0f794254c97f kernel-doc-2.6.32-504.16.2.el6.noarch.rpm b0914773e170bcb9ea774e5061356d811517a4e1ee5a7857d8dd411072a62104 kernel-firmware-2.6.32-504.16.2.el6.noarch.rpm b74f7eb051545a2abd7a27c887b0d5e8484530b6f60b7fde60ad97db295631d9 kernel-headers-2.6.32-504.16.2.el6.i686.rpm bd45c211850f79ebf492917bcc2d783ae7f50b85f55709febb7d68a58d53beec perf-2.6.32-504.16.2.el6.i686.rpm 52b754590496e9624ccca4c74072df64a0c0e5bfc67bc0fb295cd1716585cacd python-perf-2.6.32-504.16.2.el6.i686.rpm x86_64: 9ca93dc7a0f0241828f5741e9dad3e5f8a76a2a4ae651fe667069c9870c269fa kernel-2.6.32-504.16.2.el6.x86_64.rpm 06a5262def11bbeee0572101b4b4243c5a31a55a4f45ea33f9ebbfa6cde30bc9 kernel-abi-whitelists-2.6.32-504.16.2.el6.noarch.rpm b01274ee4dbb1a15246a0009ebfbd7f71bd82f8d52e171ebf5fec38e81b42c9c kernel-debug-2.6.32-504.16.2.el6.x86_64.rpm 23ed9a596107aff6ee765973d7c712649d6a7d1edd273de4d580afe3164fd61d kernel-debug-devel-2.6.32-504.16.2.el6.x86_64.rpm 57728d7d7d067cd724b055e023ed89e93619a0029eb252588242400cbda486cb kernel-devel-2.6.32-504.16.2.el6.x86_64.rpm 3a5fec20c360b962eb6899bbafbad30fd135badfdf90b77276eb0f794254c97f kernel-doc-2.6.32-504.16.2.el6.noarch.rpm b0914773e170bcb9ea774e5061356d811517a4e1ee5a7857d8dd411072a62104 kernel-firmware-2.6.32-504.16.2.el6.noarch.rpm 96b5e16c3489f088748889d18d16f1f813aaee1cc98dc9455b4068cb52943c9c kernel-headers-2.6.32-504.16.2.el6.x86_64.rpm 04510214dd0ed77628cbc24a2787692422e953ba83329cdbfcf397f410667557 perf-2.6.32-504.16.2.el6.x86_64.rpm 715a06476e838580ddbefa8321e683f26f37dbfedba61e019928a84cb548d0ba python-perf-2.6.32-504.16.2.el6.x86_64.rpm Source: 702f6044ee3d062f68de8dbc71eca0ca0ef000efd6a8cb9951beddb3d507e382 kernel-2.6.32-504.16.2.el6.src.rpm
Monthly Archives: April 2015
CESA-2015:0867 Important CentOS 6 qemu-kvmSecurity Update
CentOS Errata and Security Advisory 2015:0867 Important Upstream details at : https://rhn.redhat.com/errata/RHSA-2015-0867.html The following updated files have been uploaded and are currently syncing to the mirrors: ( sha256sum Filename ) i386: f1b2ea595fd1df5cd0b5031ad6389073912cb4d175f094d32c887a79d7b2721e qemu-guest-agent-0.12.1.2-2.448.el6_6.2.i686.rpm x86_64: e277198df13167b1a279608f309968cbeea3b7813b56b3a039a5f8296fb0b535 qemu-guest-agent-0.12.1.2-2.448.el6_6.2.x86_64.rpm a755460458bfd8ebb0c0e894b7caf5c2d94390ce96051cb2d815fb15162d7f28 qemu-img-0.12.1.2-2.448.el6_6.2.x86_64.rpm a008fe54259159fe522e5cccc12c52ab1aa662d318f1b2eb003b30cb01209d3b qemu-kvm-0.12.1.2-2.448.el6_6.2.x86_64.rpm 8193a3930e0f9f96b1e5cea4e42a3d537092c039f0117e30c6d5313faff17a3e qemu-kvm-tools-0.12.1.2-2.448.el6_6.2.x86_64.rpm Source: d8f563e6ebe7ccb31b6ce0ac6490b0496ae0b50967a105380dd930a4d7606add qemu-kvm-0.12.1.2-2.448.el6_6.2.src.rpm
iPassword Manager v2.6 iOS – Persistent Vulnerabilities
Posted by Vulnerability Lab on Apr 22
Document Title:
===============
iPassword Manager v2.6 iOS – Persistent Vulnerabilities
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1453
Release Date:
=============
2015-04-21
Vulnerability Laboratory ID (VL-ID):
====================================
1455
Common Vulnerability Scoring System:
====================================
3.7
Product & Service Introduction:…
Apple iOS 8.0 – 8.0.2 – Controls Re Auth Bypass Vulnerability
Posted by Vulnerability Lab on Apr 22
Document Title:
===============
Apple iOS 8.0 – 8.0.2 – Controls Re Auth Bypass Vulnerability
References (Source):
====================
http://www.vulnerability-lab.com/get_content.php?id=1322
Video: http://www.vulnerability-lab.com/get_content.php?id=1334
Release Date:
=============
2015-03-02
Vulnerability Laboratory ID (VL-ID):
====================================
1322
Common Vulnerability Scoring System:…
AVG Managed Workplace 9.1 Press Kit
Press Release
AVG Business Extends Global Footprint with Latest Release of AVG Business Managed Workplace Platform
Managed Workplace 9.1 English
Managed Workplace 9.1 German
Secure-Sign-On German
CloudCare German
![]()
![]()
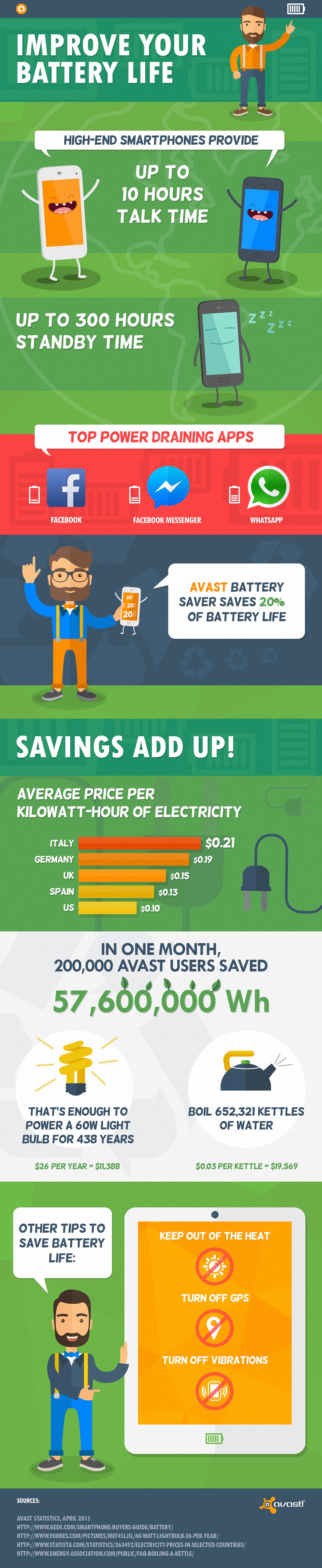
Avast highlights Battery Saver users for their positive impact on the environment
Today is Earth Day. It’s a day that people, organizations, corporations, and governments around the world demonstrate their commitment to protect the Earth and help advance a sustainable future. Every action, no matter how small, counts – from eating less meat to recycling or composting to reducing your energy footprint; it all contributes to a cleaner, greener world now and in the future.
Avast users do their part to save the Earth
Since our minds are on all things green this Earth Day, we want to highlight a particular bunch of Avast customers. These Android users simply came to Avast to find a way to save some of their smartphone’s battery power. Little did they realize when they installed Avast Battery Saver on their Android device that together they were making a difference that even we were surprised about.
In the first month that Avast Battery Saver was available, 200,000 customers downloaded and actively used it on their Android phone or tablet. This infographic shows how that cumulative use added up to real energy savings.
Do your part for Earth Day, and save up to 20% battery power everyday! Install Avast Battery Saver for free from Google Play.
AVG Business Extends Global Footprint with Latest Release of AVG Business Managed Workplace Platform
AMSTERDAM and SAN FRANCISCO – April 22, 2015 – AVG® Technologies N.V. (NYSE: AVG), the online security company™ for 200 million active users, today announced the immediate availability of the most comprehensive version of AVG Business Managed Workplace, AVG’s fully integrated, open ecosystem remote monitoring and management (RMM) platform.
Featuring Secure Sign-On and Backup and Disaster Recovery extensions and including seamless Microsoft365 and VMware integration, AVG Business Managed Workplace makes it easy for partners to deploy and administer remote IT management services to their business customers. Released in key markets worldwide, including Australia, Canada, New Zealand, the Nordics, the United Kingdom, and the United States, and it is also localized for partners in Austria, Germany and Switzerland through AVG’s new regional offices.
AVG Business Managed Workplace Version 9.1 delivers an enriched social media-style user interface that streamlines workflows to simplify the lives of IT providers, Managed Service Providers and their small-to-medium sized business customers. The integration of remote mobile security through AVG Secure Sign-On and the Backup and Disaster Recovery management capabilities enable new site on-boarding in fifteen minutes or less*. Dedicated, global customer service and technical support is available to all partners, with a value-add two-tier premium Network Operations Center support service offering 24×7 response and remediation available for additional support in English speaking markets.
“We chose AVG Business Managed Workplace as our remote monitoring platform for its simple single screen user interface and the fact that it was very easy to deploy. This allows our staff to proactively respond to our customer needs as well improving productivity. AVG Business is providing us a great service with comprehensive training and local support that we need and ensures that we get real value from their technical support services,” said Roger Lundström, CTO Protelosolutions AB.
Among the key benefits provided to partners by the latest enhancements are:
- Faster, easier navigation and monitoring – Enhanced, intuitive new user interface** enables fast, simple navigation. The display of important customer systems information at-a-glance, sleek design and optimized workflows deliver an improved user experience allowing partners to not waste any time in training.
- Simple security deployment for cloud and mobile applications – An intuitive, guided process simplifies deployment and enables actionable information to be delivered directly to the central dashboard for ease of administration.
- Secure Sign-On – Single sign-on, cloud identity, identity management and multi-factor authentication come together in a system that solves the Bring-Your-Own-Device challenge by tackling small business IT concerns around employees using a ‘real world’ mix of personal and company-issued devices to do business both inside and outside the four walls of the office. Availability with Active Directory and multi-factor authentication makes deployment straightforward and provides extra security measures.
- Ready available BDR services integration – Full BDR integration lets partners build new recurring revenue streams via premium data protection services for customers, including server backup, endpoint backup, data archive, file sharing and disaster recovery to any on-premise, hosted cloud or in-house datacentre location.
- Industry-leading Premium Network Operations Center (NOC) services – A new two-tier premium NOC services option enables skilled IT resources to be extended to 24×7 response without hiring additional headcount.
- Richer connectivity experience with leading industry applications – Open ecosystem approach makes it easier than ever to seamlessly manage popular applications such as Microsoft Office 365 and VMware as well as leading connectivity tools like ScreenConnect, TeamViewer and LogMeIn Pro.
“Success for us is making it easy for our partners to move to AVG Business Managed Workplace because we know that success for them is being able to deploy and administer IT services easily and flexibly to their business customers. Our centralized approach through a ‘single pane of glass’ user interface integrates the core AVG functionality with industry-standard solutions including Microsoft365 and VMware for maximum productivity. This lets partners see all the information they need to make the best informed decision for their business,” said Mike Foreman, General Manager, AVG Business. “Being able to deliver the platform in local language to partners in Germany and Switzerland is a significant milestone in the growth of AVG Business and testament to the partner demand we are seeing in new markets.”
* Based on AVG internal tests
** Images in English language and German language available here: http://now.avg.com/avg-managed-workplace-9-1-press-kit/
![]()
![]()
Re: Photo Manager Pro 4.4.0 iOS – Code Execution Vulnerability
Posted by Mario Vilas on Apr 22
This looks like a reflected XSS, not a code execution vulnerability as the
term is commonly understood.
Netgear WNR2000v4 Multiple Vulnerabilities
Posted by endeavor on Apr 22
I’m releasing a few vulnerabilities for the WNR2000v4 Netgear router.
Netgear is currently working these issues.
Quick Fix
———
If you own a WNR2000v4, set a strong password and set security questions
to jibberish.
Timeline
——–
FEB2015 – “MW” Volunteers to be victim to router pwning games.
06MAR2015 – WNR2000v4 Arrives
12MAR2015 – Exploit complete
13MAR2015 – Exploit demoed
~01APR2015 – MW switches to DD-WRT…
Google Analytics by Yoast stored XSS #2
Posted by Jouko Pynnonen on Apr 22
*Overview*
Google Analytics by Yoast is one of the most popular WordPress plug-ins
with over 7 million downloads and “1+ million” active installs. Last month
Yoast patched a stored XSS we reported in the plug-in. Shortly after this
we identified another bug of a similar severity. The second stored XSS has
now been corrected.
An unauthenticated attacker can store JavaScript in the WordPress
administrator’s Dashboard on the target…