Researchers in Europe have published research examining weak, homegrown cryptography used in the Open Smart Grid Protocol.
Monthly Archives: May 2015
Cisco Patches Remote Code Execution Bugs in UCS Central
Cisco has patched a critical input validation vulnerability in its UCS Central software.
Is online voting a security risk?
The world is moving online and so too now is politics. But as online, electronic voting (e-voting) increasingly becomes reality, are we opening ourselves up to vote rigging by power-hungry politicians or fame-seeking hackers?
The post Is online voting a security risk? appeared first on We Live Security.
![]()
Yahoo eMarketing Cross Site Scripting
Yahoo eMarketing suffered from a cross site scripting vulnerability.
Album Streamer 2.0 Directory Traversal
Album Streamer version 2.0 suffers from a directory traversal vulnerability.
WordPress Ultimate Profile Builder 2.3.3 CSRF / Cross Site Scripting
WordPress Ultimate Profile Builder plugin version 2.3.3 suffers from cross site request forgery and cross site scripting vulnerabilities.
WordPress ClickBank Ads 1.7 CSRF / Cross Site Scripting
WordPress ClickBank Ads plugin version 1.7 suffers from cross site request forgery and cross site scripting vulnerabilities.
Google introduce new account security measure
One of the most convenient things about having a Google account is that you can use it to log into various accounts across the web.
However, according to a Google blog, users that log in to third party sites using their Google credentials are potentially at risk of phishing attacks.

To help protect users, Google has introduced a new free to use Chrome extension called Password Alert. Here’s how it works:
“Once you’ve installed and initialized Password Alert, Chrome will remember a “scrambled” version of your Google Account password. It only remembers this information for security purposes and doesn’t share it with anyone. If you type your password into a site that isn’t a Google sign-in page, Password Alert will show you a notice like the one below. This alert will tell you that you’re at risk of being phished so you can update your password and protect yourself.”
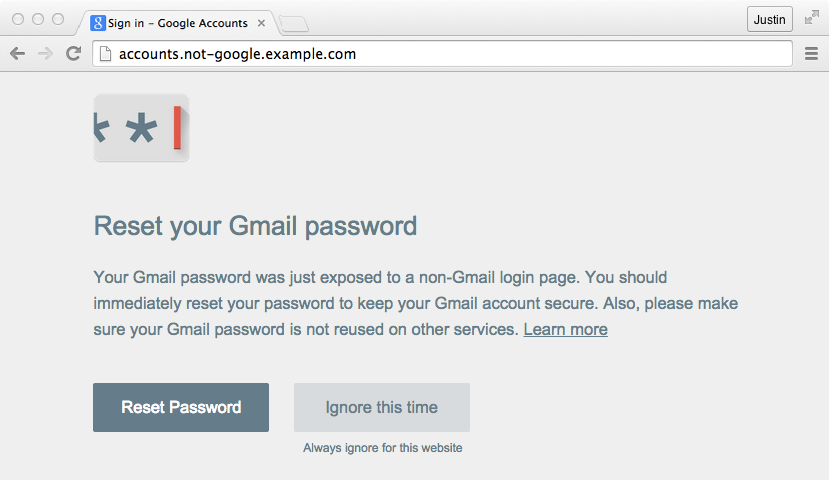
While the extension is designed to provide Google users with an extra level of protection when surfing the web it is still a work in progress.
Security researchers have already discovered a number of workarounds the extension but Google is continuing to work on the vulnerabilities.
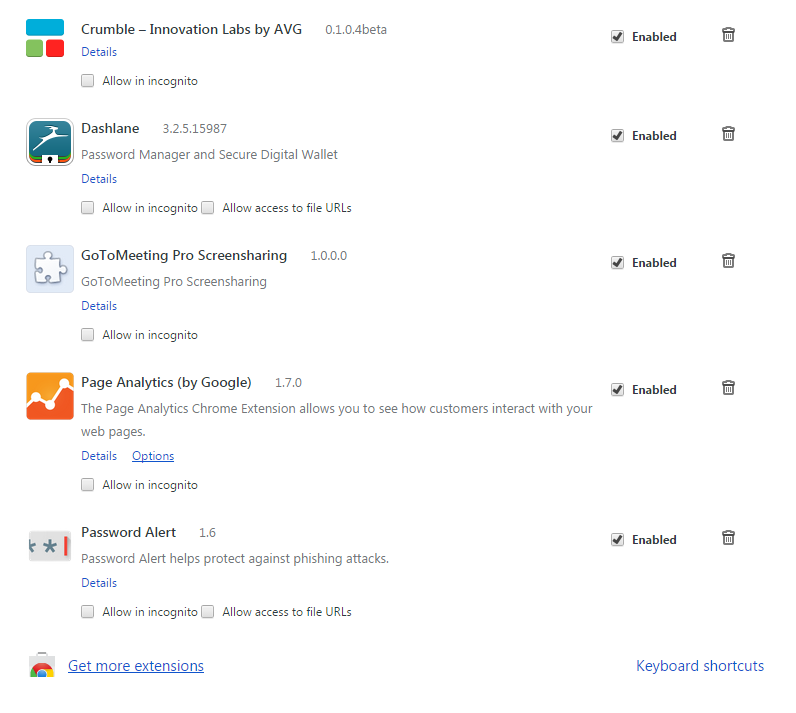
How to check which extensions you are running.
Checking which Chrome extensions are active is quick and easy. Within Chrome, open the menu in the top right and select More Tools. Select Extensions from the menu.
Here you can view which extensions are currently running, add and remove extensions.
Faraday 1.0.10
Faraday is a tool that introduces a new concept called IPE, or Integrated Penetration-Test Environment. It is a multiuser penetration test IDE designed for distribution, indexation and analysis of the generated data during the process of a security audit. The main purpose of Faraday is to re-use the available tools in the community to take advantage of them in a multiuser way.
WordPress Ultimate Product Catalogue 3.1.2 SQL Injection
WordPress Ultimate Product Catalogue plugin versions 3.1.2 and below suffer from multiple remote SQL injection vulnerabilities.
