March, April, May and June. During the last four months, Panda Security has obtained the best rate protection in the Real World Protection Test by Av-Comparatives.
It’s possible that you don’t know exactly what this means, so that’s where we come in! The test reflects real conditions in which the security solutions of different companies are analyzed and examined.
It is an independent laboratory, so the conclusions drawn from the tests are really important.
In these tests, Panda participated with our free antivirus, Panda Antivirus Free, and successfully detected and blocked 99% of the threats.
It’s easy for us to say this to you in words, but we think you’ll appreciate it more with this info-graph.
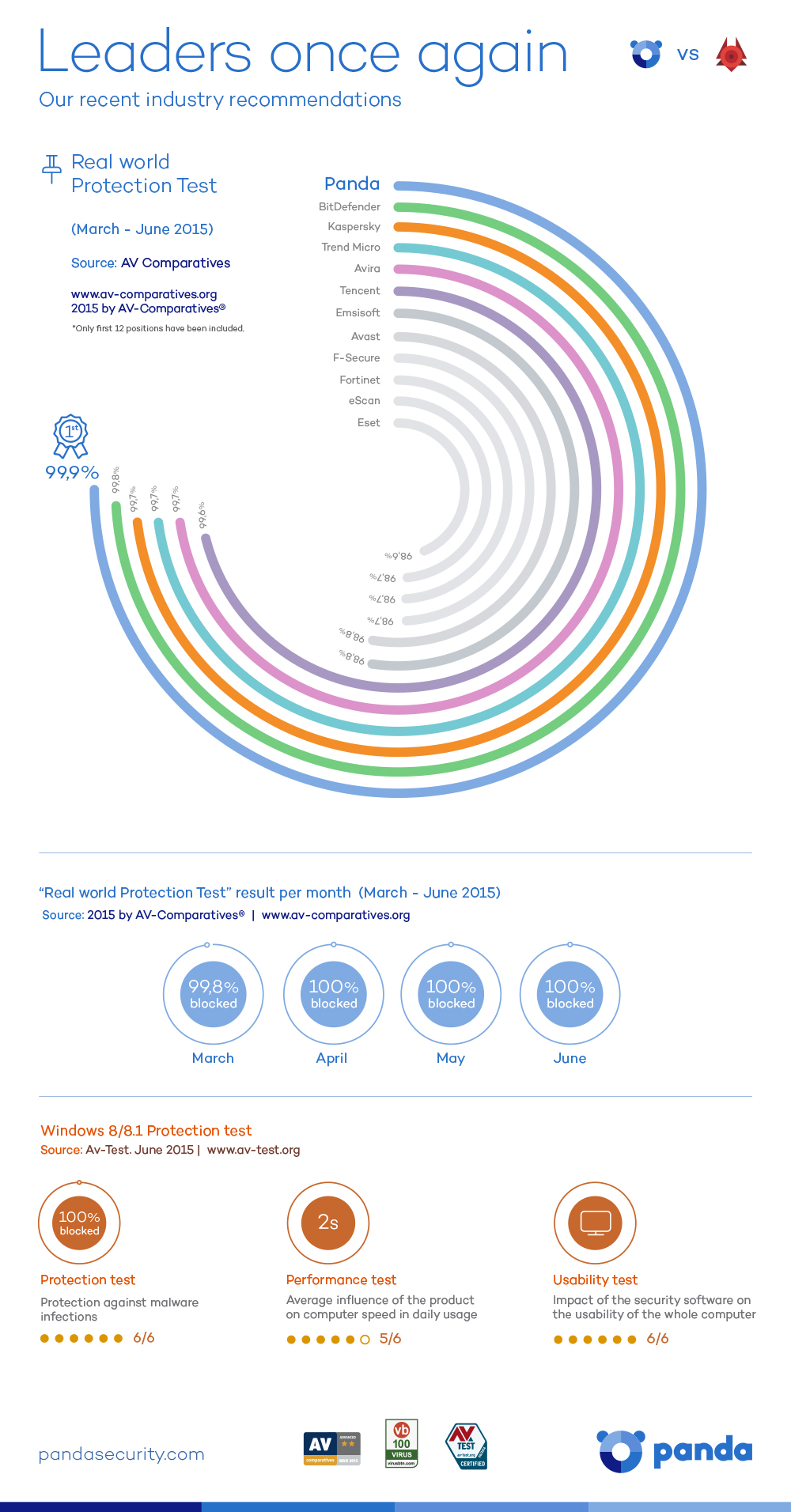
So, there you have it, if you want the best protection… you need Panda!
If you want to share the info-graph you can do it with this code!
The post Panda Security detects and blocks 99.9% of threats! appeared first on MediaCenter Panda Security.