Monthly Archives: August 2015
Reflection DDoS Attacks Abusing RPC Portmapper
Level 3 Communications has discovered a new type of reflection DDoS attack that takes advantage of RPC Portmapper to overwhelm networking services.
IRS data breach more severe than originally thought
IRS admits that the data breach it experienced in May is far bigger than previously thought.
The post IRS data breach more severe than originally thought appeared first on We Live Security.
![]()
Phishing unravelled
Phishing may well be one of the oldest online scams in the world, but it’s also one of the most effective and commonly deployed. Here’s what to be aware of.
The post Phishing unravelled appeared first on We Live Security.
![]()
Six challenges for the Chief Information Security Officer

The increasingly complex landscape that society’s mass digitization has established, driven by mobility and permanent connectivity, coupled with the new risks and threats that are proliferating in the market – which are becoming more and more sophisticated-, has created new challenges for the Chief Information Security Officer (CISO). Let’s see what they are here.
-
The technological scenario is diversifying… and becoming more complicated
Although it may seem hard to believe, but not long ago people exclusively used personal computers and networks highly controlled by the IT manager in a way that, just by protecting the organization’s perimeter, the company was safe from possible attacks. But the technology landscape today is very different and systems on the premises (both personal and located at the company) have given way, on many occasions, to systems based on the supply model, known as cloud computing.
On the other hand, data is no longer generated and stored only in the data center but, mostly on mobile devices which proliferate amongst employees and which, on many occasions, are not even provided by the company, but are personal (although they are also used for work purposes without the access control applications used previously). Even the corporate network’s intelligence has jumped from the data center to the professionals’ devices. Furthermore, the network today is starting to provide connection to the most varied devices, and increasingly will be taking into account the trend towards the so-called Internet of Things.

This scenario requires CISOs to have a new approach which responds to these new models (cloud) and practices (the famous BYOD or the use of personal devices in the work environment). It is essential they have very specific policies in this respect and, above all, they should inform their employees about them, explaining what action should be taken to avoid risking their company’s information. It is also essential to protect the mobile device from the data center with the new software tools (many of which are delivered as a service or cloud model), and those which manage mobile devices, provided by the security suppliers, whilst not forgetting to shield the internal network and corporate assets.
In addition, with regards to the adoption of the cloud, it is necessary to agree with the cloud providers which security controls must be applied and, of course, only upload assets and core systems to the cloud if the safety standards are the highest and comply with the relevant regulations of data protection, etc.
-
Threats are getting more dangerous
The second but no less important challenge for CISOs is the change in the type of attacks and threats that has occurred in recent times. Cyberattacks that were conceived by hackers in the past to overcome an IT barrier have given way to persistent and targeted threats by groups of crooks whose purpose is information theft, espionage, or economic profit.
Chief Information Security Officers should be aware of this new reality and know that, although it is difficult to avoid the attacks, it is possible to mitigate its effect if they react quickly and they are ready. Experts recommend adopting a security approach based on methodology and betting on standards already recognized in the industry as CoBit or ISO 27000, and frequently conducting audits to see the degree of preparation when facing an incident of this type.
Improving risk management is possible, thanks to the constant monitoring of increasingly sophisticated threats that occur on computers and on the net. There are many tools already available on the market and their implementation and deployment (many work in service mode) is simple.
-
Budgets still tight
Recent years have been characterized by a fall, or at least an important adjustment in IT budgets still suffered by many companies, even though the economic situation is beginning to improve. Fortunately the senior management of all kinds of companies is increasingly aware that spending on information security is absolutely necessary. So while it is a challenge to justify expenditure in the IT area, the truth is that for security managers this task is easier, especially after some notorious attacks produced in the industry like the one suffered by Sony Pictures, amongst others.
Proof of this is that the expense on security has continued to increase exponentially in recent times (even in times of crisis) and, according to Gartner, it will reach 76 billion dollars globally this year 2015, which is to say that it will increase more than 8% compared to the year before. The growing adoption of the previously mentioned mobility and cloud computing technologies, as well as social networks, will promote the use of new technologies and security services of up to the year 2016, according to the consultant.
-
Scarcity of qualified personnel
The human resources related to information security are scarce and have a high cost, a reality which is another great challenge to the person in charge of this area. More problematic, however, is to be able to retain these professionals in a market where companies all bid for them. What can be done? It won’t hurt if the CISO, among his other roles, takes the time to promote talent and development promotion programs for employees in his area which wouldn’t only involve an economic consideration but would also bring benefits that go beyond that (flexible working environment, high level of training, etc.) in order to keep these so coveted and, at the same time, necessary employees.

-
Awareness and alignment with the business
Not only must the Chief Information Officer (CIO) be aligned with the business but also the Chief Information Security Officer. So that, beyond having solid knowledge in the field of communications and information technology and how to ensure security in applications and systems, the CIO will need to know how to guide your company to enter new markets, embrace new technologies and geographic areas in such a way that the business risks are mitigated as much as possible.
Having the ability to establish bridges between the business team and the systems engineers and application developers will also be a more than necessary task for the new Chief Information Officers.
-
Make security invisible for the user
As is the case of IT in general, it is necessary to work to make the information security invisible and transparent for the organization and its users (employees, partners, suppliers, customers). The work involved behind the scenes (linking security with the business information) is hard but necessary.
The post Six challenges for the Chief Information Security Officer appeared first on MediaCenter Panda Security.
How can I stop people from connecting to my Wi-Fi?

Paying for a fast and reliable Wi-Fi connection at home only to find out that your neighbor is stealing the signal from you is pretty annoying. Not only is it frustrating, but there is also the legal aspect to think of – everything that is viewed and downloaded by the Wi-Fi connection is your responsibility.
In the majority of cases it isn’t enough to protect your network by using the long and complicated password that comes with the router. Nor is it enough if you change it and create an even more difficult one.
If you want to know who is connecting to your Wi-Fi and how to stop your connection from being open to the public, the best thing you can do is use the Wi-Fi protector and monitor that you can find in the new line of 2016 Panda product.
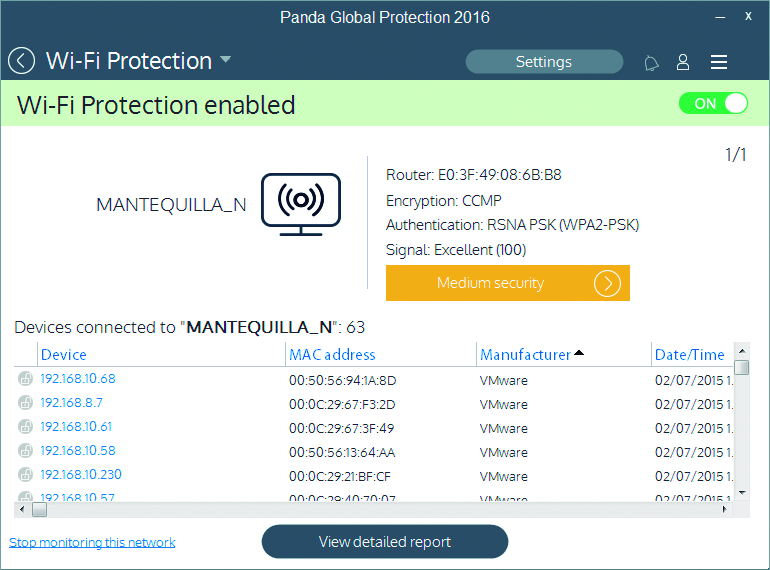
This feature allows you to see all of the devices that are connected to your network and lets you block an intruder if you detect one. This will stop them from being able to reconnect again.
Furthermore, the monitor will provide you with the following information:
- Wi-Fi networks that you are connected to: network name, Mac router address, encryption, signal strength.
- Device information: name or Mac, manufacturer, date/time of connection, etc. It allows you to give the devices nicknames so as to recognize them easily.
- Information on the saturation of the default channel: by changing to the channel recommended by Panda, you can increase your connection speed.
- History of connections made with different devices. This lets you review who has connected to the network and identify intruders.
So, are you ready to protect your Wi-Fi connection?
The post How can I stop people from connecting to my Wi-Fi? appeared first on MediaCenter Panda Security.
NICE news about the cybersecurity skills shortage (and a call for papers)
The cybersecurity skills gap is a security problem and in the US the National Initiative For Cybersecurity Education (NICE) is seeking to reduce that gap.
The post NICE news about the cybersecurity skills shortage (and a call for papers) appeared first on We Live Security.
![]()
FreeBSD-SA-15:20.expat
Could someone be watching you through your webcam?
A few weeks ago in Toronto, Chelsea Clark and her boyfriend we’re snuggling in their own home watching Netflix together on his laptop. This sounds very similar to what lots of people do to relax at home in the evening. What makes this story stand out is that someone was in the room with them.

Some people cover the webcam with a bandage to protect their privacy
Turns out that the next day when Clark looked at her Facebook page, she saw intimate images of herself and her boyfriend from the night before sent from an unknown person. The person, identified as Mahmoud Abdul in Cairo, Egypt, uploaded the pictures with a message that said “Really, cute couple [sic]”. The pictures were apparently taken from the laptop’s webcam.
This type of story is not new. This past March, a young man turned himself into the FBI and was sentenced to 18 months in federal prison for the computer hacking of Miss Teen USA, Cassidy Wolf. He watched her through her computer’s webcam for months, and took intimate photos of her in her own bedroom. He then attempted to blackmail her, asking for money for not posting the videos and photos.
You may remember the stories we shared with you on this blog about baby monitors that were hacked in Ohio and in Texas. In both incidents, a hacker took control of the monitor and screamed obscenities and shouted abuse at the toddlers while they were sleeping.
These are stories that make your hair stand up on the back of your neck, especially when you think about the lengths we go to while securing our homes from intruders. We lock the doors and windows, we install burglar alarms and motion-sensitive lighting — all to keep bad guys out. But these days, it’s what we bring inside our house that makes us vulnerable.
How to protect yourself from webcam or CCTV hacks
- The best defense is to make sure that your computer is always up-to-date. Update your antivirus program to the latest version and keep your virus definitions current, update your browsers and plugins and patch your software, even well-known names like Adobe, Oracle, and Microsoft. Avast Software Updater can help you stay on top of all that.
- Make sure your router is protected. Avast Home Network Security checks your home network for security issues to help prevent attacks on your router or devices. This video explains,
- If you have an external camera, such as a CCTV device, then do what you can to understand how it works and what security measures are in place. This may include changing the default password and settings.
- Many people tape a piece of paper or stick a bandage over their camera when they’re not using it.
- As always, do not click on links in emails or other messages that are unexpected or come from strangers.
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()
MS15-093 – Critical: Security Update for Internet Explorer (3088903) – Version: 1.0
Severity Rating: Critical
Revision Note: V1.0 (August 18, 2015): Bulletin published.
Summary: This security update resolves a vulnerability in Internet Explorer. The vulnerability could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Customers whose accounts are configured to have fewer user rights on the system could be less impacted than those who operate with administrative user rights.

