------------------------------------------------------------------------
VMware Security Advisory
Advisory ID: VMSA-2015-0007
Synopsis: VMware vCenter and ESXi updates address critical security
issues
Issue date: 2015-10-01
Updated on: 2015-10-01
CVE number: CVE-2015-5177 CVE-2015-2342 CVE-2015-1047
------------------------------------------------------------------------
1. Summary
VMware vCenter and ESXi updates address critical security issues.
2. Relevant Releases
VMware ESXi 5.5 without patch ESXi550-201509101
VMware ESXi 5.1 without patch ESXi510-201510101
VMware ESXi 5.0 without patch ESXi500-201510101
VMware vCenter Server 6.0 prior to version 6.0 update 1
VMware vCenter Server 5.5 prior to version 5.5 update 3
VMware vCenter Server 5.1 prior to version 5.1 update u3b
VMware vCenter Server 5.0 prior to version 5.u update u3e
3. Problem Description
a. VMWare ESXi OpenSLP Remote Code Execution
VMware ESXi contains a double free flaw in OpenSLP's
SLPDProcessMessage() function. Exploitation of this issue may
allow an unauthenticated attacker to execute code remotely on
the ESXi host.
VMware would like to thank Qinghao Tang of QIHU 360 for reporting
this issue to us.
The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the identifier CVE-2015-5177 to this issue.
Column 4 of the following table lists the action required to
remediate the vulnerability in each release, if a solution is
available.
VMware Product Running Replace with/
Product Version on Apply Patch
==================== ======= =================
ESXi 6.0 ESXi not affected
ESXi 5.5 ESXi ESXi550-201509101
ESXi 5.1 ESXi ESXi510-201510101
ESXi 5.0 ESXi ESXi500-201510101
b. VMware vCenter Server JMX RMI Remote Code Execution
VMware vCenter Server contains a remotely accessible JMX RMI
service that is not securely configured. An unauthenticated remote
attacker that is able to connect to the service may be able use it
to execute arbitrary code on the vCenter server.
VMware would like to thank Doug McLeod of 7 Elements Ltd and an
anonymous researcher working through HP's Zero Day Initiative for
reporting this issue to us.
The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the identifier CVE-2015-2342 to this issue.
Column 4 of the following table lists the action required to
remediate the vulnerability in each release, if a solution is
available.
VMware Product Running Replace with/
Product Version on Apply Patch
============= ======= ======= ===============
VMware vCenter Server 6.0 Any 6.0 u1
VMware vCenter Server 5.5 Any 5.5 u3
VMware vCenter Server 5.1 Any 5.1 u3b
VMware vCenter Server 5.0 Any 5.0 u3e
c. VMware vCenter Server vpxd denial-of-service vulnerability
VMware vCenter Server does not properly sanitize long heartbeat
messages. Exploitation of this issue may allow an unauthenticated
attacker to create a denial-of-service condition in the vpxd
service.
VMware would like to thank the Google Security Team for reporting
this issue to us.
The Common Vulnerabilities and Exposures project (cve.mitre.org)
has assigned the identifier CVE-2015-1047 to this issue.
Column 4 of the following table lists the action required to
remediate the vulnerability in each release, if a solution is
available.
VMware Product Running Replace with/
Product Version on Apply Patch
============= ======= ======= ==============
VMware vCenter Server 6.0 Any not affected
VMware vCenter Server 5.5 Any 5.5u2
VMware vCenter Server 5.1 Any 5.1u3
VMware vCenter Server 5.0 Any 5.0u3e
4. Solution
Please review the patch/release notes for your product and version
and verify the checksum of your downloaded file.
ESXi
--------------------------------
Downloads:
https://www.vmware.com/patchmgr/findPatch.portal
Documentation:
http://kb.vmware.com/kb/2110247
http://kb.vmware.com/kb/2114875
http://kb.vmware.com/kb/2120209
vCenter Server
--------------------------------
Downloads and Documentation:
https://www.vmware.com/go/download-vsphere
5. References
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-5177
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-2342
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2015-1047
------------------------------------------------------------------------
6. Change log
2015-10-01 VMSA-2015-0007
Initial security advisory in conjunction with ESXi 5.0, 5.1 patches
and VMware vCenter Server 5.1 u3b, 5.0 u3e on 2015-10-01.
------------------------------------------------------------------------
7. Contact
E-mail list for product security notifications and announcements:
http://lists.vmware.com/cgi-bin/mailman/listinfo/security-announce
This Security Advisory is posted to the following lists:
security-announce at lists.vmware.com
bugtraq at securityfocus.com
fulldisclosure at seclists.org
E-mail: security at vmware.com
PGP key at: http://kb.vmware.com/kb/1055
VMware Security Advisories
http://www.vmware.com/security/advisories
Consolidated list of VMware Security Advisories
http://kb.vmware.com/kb/2078735
VMware Security Response Policy
https://www.vmware.com/support/policies/security_response.html
VMware Lifecycle Support Phases
https://www.vmware.com/support/policies/lifecycle.html
Twitter
https://twitter.com/VMwareSRC
Copyright 2015 VMware Inc. All rights reserved.
_______________________________________________
Security-announce mailing list
Security-announce-xEzmwC/hc7si8rCdYzckzA< at >public.gmane.org
http://lists.vmware.com/mailman/listinfo/security-announce
Monthly Archives: October 2015
Kaspersky Lab Joins Forces with ENABLE to Tackle Bullying and Nurture IT Innovation
Microsoft gaffe spooks users as weird Windows 7 update accidentally released
Good news – hackers hadn’t hijacked Microsoft’s Windows Update system. Bad news – users’ confidence will have been shaken again by Microsoft’s goof.
The post Microsoft gaffe spooks users as weird Windows 7 update accidentally released appeared first on We Live Security.
![]()
Sharing and the fine art of stopping malware
Sharing is a critical life skill, and I’m talking about more than snacks and your favorite toy. It is an essential part of stopping malware. But unlike trading brownies or matchbox cars, sharing malware samples is complicated.
The post Sharing and the fine art of stopping malware appeared first on Avira Blog.
AVG kicks off National Cyber Security Awareness Month with updated product suite
I am delighted that that we have released our updated Protection and Performance products and suites – consciously timed with the inauguration of National Cyber Security Awareness Month.
Introduced in the US by President Obama, National Cyber Security Awareness Month was conceived to raise awareness and education about cybersecurity, and help citizens protect the nation in the event of a cyber-incident. Throughout October, companies and organizations will be holding conversations, hosting events and taking part in Summits as they look to educate us to “Stop. Think. Connect”.
AVG fully supports this initiative, and is involved in a number of similar, designated days and months throughout the year, such as European Cyber Security Month, which aim to further security education. As we increasingly live our lives online, and the everyday devices in our homes become connected, cybersecurity has rapidly become a personal issue as well as a one of global importance. Most of us now own multiple devices and use apps for everything we do; but our growing dependency on technology, while simple to use, they bring high levels of complexity; and all too often, security and privacy become an afterthought. One of AVG’s goals is to take the complexity of your everyday, online environment and simplify it, making it as easy as possible for you to secure and manage you and your families’ digital lives and keep them protected.
The digital landscape is always evolving, and so too, must the products you use to protect yourself. The latest release of AVG’s protection products and suites are now auto-updated on a continual basis, so users will always have the latest features and capabilities without any required action on their part, removing the need for you to accept or search for an upgrades.
The new release adds significant protection capabilities, including Real-Time Cloud Detection, AI Detection and Improved Malware Detection, are also focused on real-time protection – ensuring customers are always secured against the latest threats.
These product releases continue to underscore our leadership in online security and commitment to protecting devices, data and people, at home and at work – in the August test results from AV-Test, AVG Internet Security scored 100% for both real-time and wide spread malware detection. Make sure to check back here on our blog, AVG Now, throughout the month, to hear more product and service news, and to read some of our top cybersecurity tips.
You can find out more about the latest AVG Performance and Protection products here: http://now.avg.com/avg-new-protection-performance-press-kit/
![]()
![]()
Has the dislike button finally arrived to Facebook? Of course not, don’t be fooled!
It’s been a few weeks since Mark Zuckerberg revealed that Facebook was working on incorporating the much awaited dislike button into its website, finally allowing users to give the thumbs down to posts that they don’t like.
As expected, some scheming cybercriminals have taken it upon themselves to introduce the dislike option ahead of the official Facebook launch. However, you’re not going to like what you get if you download it.
What’s most likely to happen if you download this fake dislike option is that you will pass all control of your account to the cybercriminals and, even worse, they could install malware on your computer rendering it unusable.
How can we find this supposed dislike button on our profiles? There are a few versions:
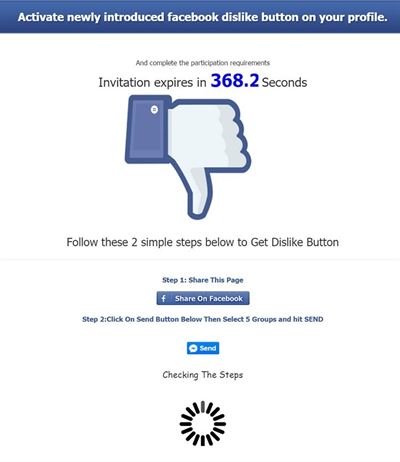
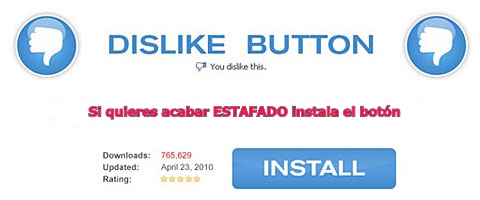
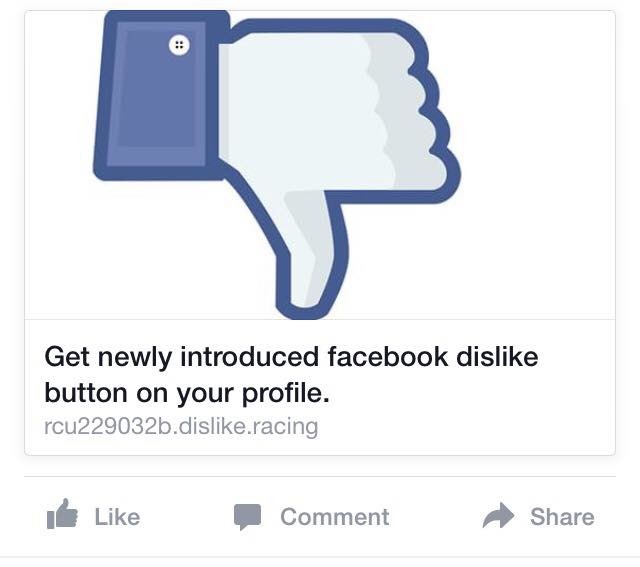
So, now you know that if you find anything like this on your profile that you should ignore it. Also, don’t share these fraudulent pages on your timeline!
The post Has the dislike button finally arrived to Facebook? Of course not, don’t be fooled! appeared first on MediaCenter Panda Security.