Red Hat Security Advisory 2016-0103-01 – The kernel packages contain the Linux kernel, the core of any Linux operating system. It was found that the x86 ISA is prone to a denial of service attack inside a virtualized environment in the form of an infinite loop in the microcode due to the way delivering of benign exceptions such as #DB is handled. A privileged user inside a guest could use this flaw to create denial of service conditions on the host kernel. A use-after-free flaw was found in the way the Linux kernel’s key management subsystem handled keyring object reference counting in certain error path of the join_session_keyring() function. A local, unprivileged user could use this flaw to escalate their privileges on the system.
Monthly Archives: February 2016
Baumer VeriSens Application Suite 2.6.2 Buffer Overflow
Baumer VeriSens Application Suite version 2.6.2 suffers from a vulnerability that is caused due to a boundary error in baselibs.dll library when processing device job file, which can be exploited to cause a buffer overflow when a user opens e.g. a specially crafted .APP file. Successful exploitation could allow execution of arbitrary code on the affected machine.
Oracle 9i XDB FTP Pass Overflow
Oracle 9i XDB FTP PASS overflow for win32. Ported to python from the oracle9i_xdb_ftp_pass.rb exploit.
The need for managed services will continue to grow in 2016 — AVG Business is here to support you
Industry research is already indicating the growth of managed services in 2016 as the channel continues to recognize its potential for SMB clients. According to one recent study from market research organization Techaisle, as much as 71% of U.S. SMB channel partners surveyed are currently offering one or more managed services solutions and another 18% are planning to offer the services within the year.
Here at AVG Business, that’s no surprise. More of our partners are moving toward a proactive approach and transitioning to managed service models, moving away from reactive strategies that are difficult to manage and maintain for their SMB clients.
Yet, successful implementation is key to unlocking the power of managed services. Simplifying the experience for both the partner and SMB customer is critical. Depending on the technology in place or the type of service contract, there could be multiple steps required before both the channel partner and SMB can realize the benefits of a centrally planned and automated security defense.
The benefits of this type of defense reach far and wide. A centrally planned solution enables AVG channel partners to efficiently deliver their unique service offerings within one standardized service delivery platform. This puts automated, service standardization in place to enable a scalable offering to better address the security needs of their SMB customers.
At AVG Business, we’re committed to helping our partners effectively unlock the power of all AVG security solutions in their marketing, selling, and implementation of managed services so they too can see the magic behind this proactive, planned and automated approach.
Here are just a few of the AVG partners experiencing great results:
- Dave Barnard, owner of DB Computer Services came to AVG Business because he’d been told by a friendly competitor that our AVG Managed Workplace solution had “every tool a MSP needs” – something we were happy to prove. According to Dave, DB Computer Services is now able to “offer an outsourced IT support solution that is complete, simple to understand, predictable, affordable and scales with the growth of our clients’ businesses.”
- For Darren Nichol, the Technical Director of pckwikfix, the move to managed services was about “standing out in the crowd by continuing to truly care and put our customers before sales targets.” The proof of this came just a few weeks after purchasing AVG Managed Workplace – the team was able to convert more than 50 clients to the streamlined monthly subscription model. With routine jobs now automated, fully integrated systems and access to unprecedented detail, Nichol says the team is “starting to get a feel for the freedom we now have to be more hands on with customers’ more interesting challenges.”
- Meanwhile Chris Carter, technical infrastructure consultant at APH, was so convinced by AVG Managed Workplace’s new premium remote control feature, plus the quality of our technical and sales support, that it migrated its entire base of managed service clients from a standard antivirus product to the full-service AVG Business platform.
We have done a lot of work toward addressing the business needs of AVG partners, including within our AVG Managed Workplace technology platform, as well as best practices on how to fulfill service contracts in the most efficient and profitable way.
We are listening and responding – and we will have more updates and news to share this year.
Until then, please continue to share your feedback in 2016!
![]()
![]()
eBay Vulnerability Exposes Users to Phishing, Data Theft
Researchers are warning that visitors to eBay.com could be tricked into opening a page on the site that could expose them to phishing attacks and data theft.
WordPress Releases Security Update
Original release date: February 02, 2016
WordPress 4.4.1 and prior versions contain two security vulnerabilities. Exploitation of one of these vulnerabilities could allow a remote attacker to obtain sensitive information.
Users and administrators are encouraged to review the WordPress Security and Maintenance Release and upgrade to WordPress 4.4.2.
This product is provided subject to this Notification and this Privacy & Use policy.
NASA HACKED! AnonSec tried to Crash $222 Million Drone into Pacific Ocean
Here’s How AnonSec Hacked into NASA
Hacker Attempted to Crash $222 Million Drone into the Pacific Ocean
However, in a statement emailed to Forbes, NASA has denied alleged hacking incident, says leaked information could be part of freely available datasets, and there is no proof that a drone was hijacked.
“Control of our Global Hawk aircraft was not compromised. NASA has no evidence to indicate the alleged hacked data are anything other than already publicly available data. NASA takes cybersecurity very seriously and will continue to fully investigate all of these allegations.”
Why Did AnonSec Hack into NASA?
“One of the main purposes of the Operation was to bring awareness to the reality of Chemtrails/CloudSeeding/Geoengineering/Weather Modification, whatever you want to call it, they all represent the same thing.”
“NASA even has several missions dedicated to studying Aerosols and their affects (sic) on the environment and weather, so we targeted their systems.”
- Cloud seeding: A weather alteration method that uses silver iodide to create precipitation in clouds which results to cause more rainfall to fight carbon emission which ultimately manipulates the nature.
- Geoengineering: Geoengineering aims to tackle climate change by removing CO2 from the air or limiting the sunlight reaching the planet.
![]()
WordPress 4.4.2 Security and Maintenance Release
WordPress 4.4.2 is now available. This is a security release for all previous versions and we strongly encourage you to update your sites immediately.
WordPress versions 4.4.1 and earlier are affected by two security issues: a possible SSRF for certain local URIs, reported by Ronni Skansing; and an open redirection attack, reported by Shailesh Suthar.
Thank you to both reporters for practicing responsible disclosure.
In addition to the security issues above, WordPress 4.4.2 fixes 17 bugs from 4.4 and 4.4.1. For more information, see the release notes or consult the list of changes.
Download WordPress 4.4.2 or venture over to Dashboard → Updates and simply click “Update Now.” Sites that support automatic background updates are already beginning to update to WordPress 4.4.2.
Thanks to everyone who contributed to 4.4.2:
Andrea Fercia, berengerzyla, Boone Gorges, Chandra Patel, Chris Christoff, Dion Hulse, Dominik Schilling, firebird75, Ivan Kristianto, Jennifer M. Dodd, salvoaranzulla
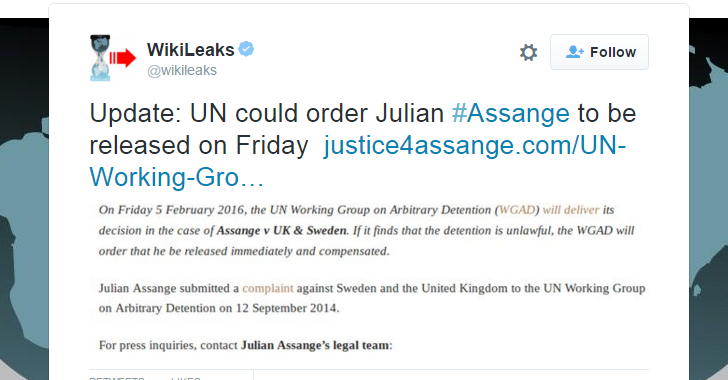
Wikileak's Julian Assange Could Be Set Free On Friday by United Nation
The decision of the United Nations investigation into the Julian Assange case is set to be revealed and could order the release of Wikileaks founder on February 5.
- First to Sweden where he is facing sexual assault allegations, which he has always denied.
- Ultimately to the United States where he could face cyber espionage charges for publishing classified US military and diplomat documents via his website Wikileaks.
![]()
HP Client Security Manager 8.3.4 Cross Site Scripting
HP Client Security Manager version 8.3.4 suffers from a cross site scripting vulnerability.