Lael Cellier discovered two buffer overflow vulnerabilities in git, a
fast, scalable, distributed revision control system, which could be
exploited for remote execution of arbitrary code.
Monthly Archives: March 2016
Avira PE Section Header Parsing Heap Underflow
Avira suffers from a heap underflow vulnerability when parsing PE section headers.
XOOPS 2.5.7.2 Cross Site Request Forgery
XOOPS version 2.5.7.2 suffers from a cross site request forgery vulnerability.
XOOPS 2.5.7.2 Directory Traversal
XOOPS version 2.5.7.2 has checks to defend against directory traversal attacks. However, they can be easily bypassed by simply issuing “…/./” instead of “../”.
Solarwinds Dameware Mini Remote Code Execution
A certain remote message parsing function inside the Dameware Mini Remote Control service does not properly validate the input size of an incoming string before passing it to wsprintfw. As a result, a specially crafted message can overflow into the bordering format field and subsequently overflow the stack frame. Exploitation of this vulnerability does not require authentication and can lead to SYSTEM level privilege on any system running the dwmrcs daemon.
XOOPS 2.5.7.2 Weak Crypto
XOOPS version 2.5.7.2 uses weak one way hash crypto MD5 along with unsalted passwords stored in the database.
TGIF: Avast security news wrap-up for March 2016
Get your Avast update on ransomware, mobile security, social media, and enterprise security.
 Mac users get first taste of ransomware
Mac users get first taste of ransomware
Mac users got attacked by ransomware in the first fully functional attack on OS X. Now that hackers have proven that Mac users are a viable target, it’s time to move on from the myth that Macs are impervious to attack and get protection.
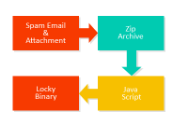 A closer look at the Locky ransomware
A closer look at the Locky ransomware
Ransomware attacks targeting PC users are quite successful. New variants are introduced, but they have the same format- encrypt your files and demand payment for the key to unlock them. The Avast Virus Lab did a deep analysis of ransomware dubbed Locky. This is deep look was followed by Locky’s JavaScript downloader, which describes the phishing campaign that has emerged as the main infection vector.
![]()
Ever Wondered How Facebook Decides — How much Bounty Should be Paid?
Facebook pays Millions of dollars every year to researchers and white hat hackers from all around the world to stamp out security holes in its products and infrastructure under its Bug Bounty Program.
Facebook recognizes and rewards bug hunters to encourage more people to help the company keep Facebook users safe and secure from outside entities, malicious hackers or others.
Recently, the
![]()
FBI warn that automobiles are vulnerable to cyberattacks
The Federal Bureau of Investigation has issued a public service announcement warning drivers that automobiles are “increasingly vulnerable” to cyberattacks.
The post FBI warn that automobiles are vulnerable to cyberattacks appeared first on We Live Security.
![]()
The Best Way to Send and Receive End-to-End Encrypted Emails
How many of you know the fact that your daily e-mails are passaged through a deep espionage filter?
This was unknown until the whistleblower Edward Snowden broke all the surveillance secrets, which made privacy and security important for all Internet users than ever before.
I often get asked “How to send encrypted email?”, “How can I protect my emails from prying eyes?” and “Which is
![]()
