Red Hat Enterprise Linux: Updated packages are now available for Red Hat OpenShift Enterprise release 2.2.
These packages are required to avoid dependency issues with the Red Hat
Enterprise Linux 6.8 base channel.
Monthly Archives: May 2016
USN-2960-1: Oxide vulnerabilities
Ubuntu Security Notice USN-2960-1
18th May, 2016
oxide-qt vulnerabilities
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 16.04 LTS
- Ubuntu 15.10
- Ubuntu 14.04 LTS
Summary
Several security issues were fixed in Oxide.
Software description
- oxide-qt
– Web browser engine for Qt (QML plugin)
Details
An out of bounds write was discovered in Blink. If a user were tricked in
to opening a specially crafted website, an attacker could potentially
exploit this to cause a denial of service via renderer crash, or execute
arbitrary code. (CVE-2016-1660)
It was discovered that Blink assumes that a frame which passes same-origin
checks is local in some cases. If a user were tricked in to opening a
specially crafted website, an attacker could potentially exploit this to
cause a denial of service via renderer crash, or execute arbitrary code.
(CVE-2016-1661)
A use-after-free was discovered in the V8 bindings in Blink. If a user
were tricked in to opening a specially crafted website, an attacker could
potentially exploit this to cause a denial of service via renderer crash,
or execute arbitrary code. (CVE-2016-1663)
It was discovered that the JSGenericLowering class in V8 mishandles
comparison operators. If a user were tricked in to opening a specially
crafted website, an attacker could potentially exploit this to obtain
sensitive information. (CVE-2016-1665)
Multiple security issues were discovered in Chromium. If a user were
tricked in to opening a specially crafted website, an attacker could
potentially exploit these to read uninitialized memory, cause a denial
of service via application crash or execute arbitrary code.
(CVE-2016-1666)
It was discovered that the TreeScope::adoptIfNeeded function in Blink
does not prevent script execution during node-adoption operations. If a
user were tricked in to opening a specially crafted website, an attacker
could potentially exploit this to bypass same origin restrictions.
(CVE-2016-1667)
It was discovered that the forEachForBinding in the V8 bindings in Blink
uses an improper creation context. If a user were tricked in to opening a
specially crafted website, an attacker could potentially exploit this to
bypass same origin restrictions. (CVE-2016-1668)
A buffer overflow was discovered in V8. If a user were tricked in to
opening a specially crafted website, an attacker could potentially exploit
this to cause a denial of service via renderer crash, or execute arbitrary
code. (CVE-2016-1669)
A race condition was discovered in ResourceDispatcherHostImpl in Chromium.
An attacker could potentially exploit this to make arbitrary HTTP
requests. (CVE-2016-1670)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 16.04 LTS:
-
liboxideqtcore0
1.14.9-0ubuntu0.16.04.1
- Ubuntu 15.10:
-
liboxideqtcore0
1.14.9-0ubuntu0.15.10.1
- Ubuntu 14.04 LTS:
-
liboxideqtcore0
1.14.9-0ubuntu0.14.04.1
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
In general, a standard system update will make all the necessary changes.
References
USN-2973-1: Thunderbird vulnerabilities
Ubuntu Security Notice USN-2973-1
18th May, 2016
thunderbird vulnerabilities
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 16.04 LTS
- Ubuntu 15.10
- Ubuntu 14.04 LTS
- Ubuntu 12.04 LTS
Summary
Several security issues were fixed in Thunderbird.
Software description
- thunderbird
– Mozilla Open Source mail and newsgroup client
Details
Christian Holler, Tyson Smith, and Phil Ringalda discovered multiple
memory safety issues in Thunderbird. If a user were tricked in to opening
a specially crafted message, an attacker could potentially exploit these
to cause a denial of service via application crash, or execute arbitrary
code. (CVE-2016-2805, CVE-2016-2807)
Hanno Böck discovered that calculations with mp_div and mp_exptmod in NSS
produce incorrect results in some circumstances, resulting in
cryptographic weaknesses. (CVE-2016-1938)
A use-after-free was discovered in ssl3_HandleECDHServerKeyExchange in
NSS. A remote attacker could potentially exploit this to cause a denial of
service via application crash, or execute arbitrary code. (CVE-2016-1978)
A use-after-free was discovered in PK11_ImportDERPrivateKeyInfoAndReturnKey
in NSS. A remote attacker could potentially exploit this to cause a denial
of service via application crash, or execute arbitrary code.
(CVE-2016-1979)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 16.04 LTS:
-
thunderbird
1:38.8.0+build1-0ubuntu0.16.04.1
- Ubuntu 15.10:
-
thunderbird
1:38.8.0+build1-0ubuntu0.15.10.1
- Ubuntu 14.04 LTS:
-
thunderbird
1:38.8.0+build1-0ubuntu0.14.04.1
- Ubuntu 12.04 LTS:
-
thunderbird
1:38.8.0+build1-0ubuntu0.12.04.1
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
After a standard system update you need to restart Thunderbird to make
all the necessary changes.
References
USN-2936-3: Firefox regression
Ubuntu Security Notice USN-2936-3
18th May, 2016
firefox regression
A security issue affects these releases of Ubuntu and its
derivatives:
- Ubuntu 16.04 LTS
- Ubuntu 15.10
- Ubuntu 14.04 LTS
- Ubuntu 12.04 LTS
Summary
USN-2936-1 introduced a regression in Firefox.
Software description
- firefox
– Mozilla Open Source web browser
Details
USN-2936-1 fixed vulnerabilities in Firefox. The update caused an issue
where a device update POST request was sent every time about:preferences#sync
was shown. This update fixes the problem.
We apologize for the inconvenience.
Original advisory details:
Christian Holler, Tyson Smith, Phil Ringalda, Gary Kwong, Jesse Ruderman,
Mats Palmgren, Carsten Book, Boris Zbarsky, David Bolter, Randell Jesup,
Andrew McCreight, and Steve Fink discovered multiple memory safety issues
in Firefox. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit these to cause a denial of
service via application crash, or execute arbitrary code with the
privileges of the user invoking Firefox. (CVE-2016-2804, CVE-2016-2806,
CVE-2016-2807)
An invalid write was discovered when using the JavaScript .watch() method in
some circumstances. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit this to cause a denial of
service via application crash, or execute arbitrary code with the
privileges of the user invoking Firefox. (CVE-2016-2808)
Looben Yang discovered a use-after-free and buffer overflow in service
workers. If a user were tricked in to opening a specially crafted website,
an attacker could potentially exploit these to cause a denial of service
via application crash, or execute arbitrary code with the privileges of
the user invoking Firefox. (CVE-2016-2811, CVE-2016-2812)
Sascha Just discovered a buffer overflow in libstagefright in some
circumstances. If a user were tricked in to opening a specially crafted
website, an attacker could potentially exploit this to cause a denial of
service via application crash, or execute arbitrary code with the
privileges of the user invoking Firefox. (CVE-2016-2814)
Muneaki Nishimura discovered that CSP is not applied correctly to web
content sent with the multipart/x-mixed-replace MIME type. An attacker
could potentially exploit this to conduct cross-site scripting (XSS)
attacks when they would otherwise be prevented. (CVE-2016-2816)
Muneaki Nishimura discovered that the chrome.tabs.update API for web
extensions allows for navigation to javascript: URLs. A malicious
extension could potentially exploit this to conduct cross-site scripting
(XSS) attacks. (CVE-2016-2817)
Mark Goodwin discovered that about:healthreport accepts certain events
from any content present in the remote-report iframe. If another
vulnerability allowed the injection of web content in the remote-report
iframe, an attacker could potentially exploit this to change the user’s
sharing preferences. (CVE-2016-2820)
Update instructions
The problem can be corrected by updating your system to the following
package version:
- Ubuntu 16.04 LTS:
-
firefox
46.0.1+build1-0ubuntu0.16.04.2
- Ubuntu 15.10:
-
firefox
46.0.1+build1-0ubuntu0.15.10.2
- Ubuntu 14.04 LTS:
-
firefox
46.0.1+build1-0ubuntu0.14.04.3
- Ubuntu 12.04 LTS:
-
firefox
46.0.1+build1-0ubuntu0.12.04.2
To update your system, please follow these instructions:
https://wiki.ubuntu.com/Security/Upgrades.
After a standard system update you need to restart Firefox to make
all the necessary changes.
References
Hacker Steals Money from Bank and Donates $11,000 to Anti-ISIS Group
Meet this Robin Hood Hacker:
Phineas Fisher, who breached Hacking Team last year, revealed on Reddit Wednesday that he hacked a bank and donated the money to Kurdish anti-capitalists in Rojava autonomous region in northern Syria that borders territory held by the ISIS (Islamic State militant group).
<!– adsense –>
Fisher, also known as “Hack Back” and “@GammaGroupPR,” claimed responsibility
![]()
How to Decrypt TeslaCrypt Ransomware Files Using Master Key
Here’s some good news for victims who are trying to unlock and remove TeslaCrypt ransomware.
Now, you can decrypt all your important files that have been encrypted by TeslaCrypt ransomware.
So, stop Googling about How to decrypt TeslaCrypt Ransomware encrypted files, as the malware authors themselves provided the solution to your problem.
<!– adsense –>
Since its launch in March last year,
![]()
Time to change your LinkedIn password
LinkedIn members’ login credentials are being sold on the dark web.
The 2012 breach of social networking site LinkedIn, has come back to haunt us. That breach resulted in 6.5 million members’ credentials being stolen. Articles published in the last day report that the number was way short of reality – it’s actually more than 167 million email and password combinations – or nearly all the members of LinkedIn.

![]()
Time to change your LinkedIn password
LinkedIn members’ login credentials are being sold on the dark web.
The 2012 breach of social networking site LinkedIn, has come back to haunt us. That breach resulted in 6.5 million members’ credentials being stolen. Articles published in the last day report that the number was way short of reality – it’s actually more than 167 million email and password combinations – or nearly all the members of LinkedIn.

![]()
Protecting Cloud APIs Critical to Mitigating Total Compromise
When it comes to cloud computing, APIs more or less drive everything, but in the eyes of some researchers, existing security controls haven’t kept pace.
Locky is far from dead
A brief update on Locky, the latest ransomware targeting PCs.
Beware of emails from random email addresses with subject lines like “Upcoming Payment – 1 Month Notice”. These emails typically come with a zip attachment that attackers have created to run a script that downloads and runs the now well-known ransomware, Locky. These phishing emails prove that Locky is not going anywhere anytime soon.
The emails are written in typical phishing style. The attacker tries to entice a potential victim to read the email and subsequently download the attachment. Attackers seem to be targeting small and medium sized businesses, to gain access to valuable company data.
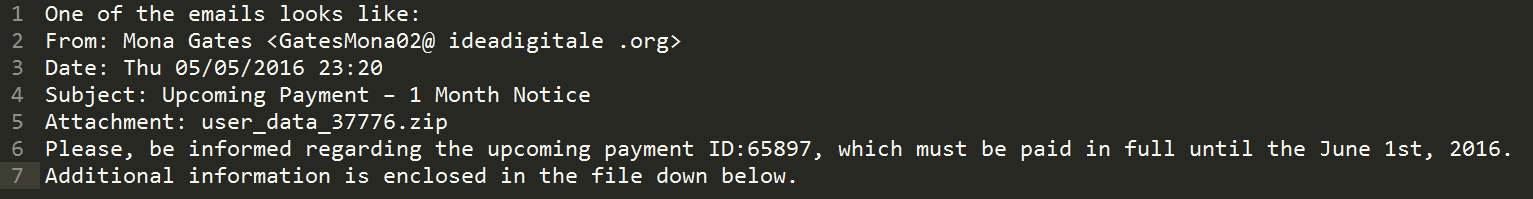 Content of the email.
Content of the email.
![]()