A third of small to medium sized businesses surveyed by AVG had never heard of ransomware, demonstrating an urgent need for education on one of the fastest growing malware categories.
Ransomware is one of the world’s fastest growing malware categories. In June, we surveyed businesses to understand who had heard of the term ‘ransomware’ and what they understood about it. 381 of our small-to-medium business (SMB) customers in the US and UK responded to our questions and the results proved revealing and concerning.
Here are the key points:
68% of respondents said they had heard of the term ‘ransomware.’
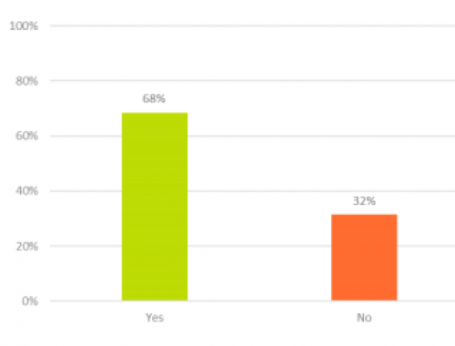
That may look like a good percentage, but this also indicates that even with security industry, media and governments working hard to educate businesses about the risks, nearly 1 in 3 is still not aware of this significant risk.
So what is ransomware and how does it impact businesses?
Ransomware is a generic term for a category of malware that restricts access to a device or the file(s) on a device until a ransom is paid. It’s a method for criminals to make money by infecting the device and has become very effective at causing havoc for a business or organization that is unfortunate enough to become a victim.
It’s not new, which is why the 32% concerns me. The first cases were reported as far back as 2005, which took the form of fake antivirus software claiming you had issues that required payment in order to be fixed.
Over time, ransomware morphed into scareware messages. Scareware messages, designed to trick users into downloading malicious software and often disguised as communications from law enforcement, typically claim that a device has been infected or that the usage history of a device shows illegal activity—or in some cases blatantly locking files until you call and pay the ransom.
The 68% of respondents claiming to know what ransomware is had very different opinions, many of them inaccurate. When asked to explain the term, it turns out that 36% (of the 68%) didn’t actually know what it was.
A major security concern
Since 2013 when Cryptolocker ransomware first surfaced, ransomware has now become a major security issue with organizations being held to ransom – and in some cases paying to get their data unlocked. Numerous incidents have been cited where thousands of dollars have been paid: hospitals, charities, hairdressers have all been held to ransom. One university has suffered 21 attacks in the last year alone!
The true scale of the problem is somewhat hard to define though because, understandably, many businesses and organisations are reluctant to reveal they’ve been held to ransom because of fears about being targeted again, or losing existing or new customers.
People are held to ransom in just a few seconds
Unsuspecting victims are infected through emails impersonating customer support personnel from well-known company brands. Once activated, the malware encrypts files and demands payment, typically a few hundred dollars within a timeframe of 48 or 72 hours.
Last year alone, the FBI received 2,453 complaints about ransomware hold-ups last year, costing the victims more than $24 million dollars! Earlier this year, the UK National Crime Agency claimed ransomware attacks have increased in frequency and complexity, and now include public threats by the perpetrators to publish victim data online, as well as the permanent encryption of valuable data.
4 ways to protect your computers and networks against ransomware
- Stay vigilant. One of the most common methods of infecting a system is via a spearheading email with a malicious attachment or link. If you are not expecting the email, or it looks suspicious in any way, do not open it and delete it.
- Back up your software and systems. It’s really important you keep your software and operating system updated. Back-up your files regularly and don’t forget to keep your backup media disconnected from your PC. Otherwise, your backups might get encrypted as well. This also applies to storage and network drives e.g. Google Drive, Dropbox, etc.
- Use the latest protection software. At AVG, we take ransomware very seriously and our AVG Internet Security and AntiVirus Business Edition solutions detect and block ransomware and other malware variants from infecting your devices and servers – leaving you to focus on what matters.
- Don’t pay. If you do fall victim, do not pay. Funding these criminals only encourages them to attack other people. Research the specific infection to see if there is a decryption tool. We offer 7 of these tools for free with more on the way.
Don’t be the 1 in 3
Taking proactive steps to protect your organization from a ransomware attack is essential to the smooth running of your business—it is your livelihood, after all. Contingency and remediation planning are also crucial to business recovery and continuity, and these plans should be tested regularly.


![]()




