Comodo Chromodo Browser suffers from an unquoted service path privilege escalation vulnerability.
Monthly Archives: October 2016
Advance MLM Script SQL Injection
Advance MLM Script suffers from a remote SQL injection vulnerability.
Hackers From Lizard Squad And Poodle Corp Arrested
Hack Warnings Prompt Cyber Security Fatigue
Witbe Remote Code Execution
Witbe suffers from a remote code execution vulnerability.
Our insulin pumps could be hacked, warns Johnson & Johnson
The Animas OneTouch Ping insulin pump contains vulnerabilities that could be exploited by a malicious attacker to remotely trigger an insulin injection.
The post Our insulin pumps could be hacked, warns Johnson & Johnson appeared first on WeLiveSecurity.
![]()
Android malware surges again
For most people, their smartphone has become the most important gateway to the internet. We use our phones to check facts on the move, plan journeys, update shopping lists and check our bank balance.
Simple-to-use apps have put information and services at our fingertips. In fact, the world now uses smartphones and tablets online more than any traditional computers and laptops.
So it’s no surprise that hackers and cybercriminals have turned their attentions to attacking your smartphone.
The Android factor
The relatively low cost of Android-powered smartphones, has helped the mobile operating system establish a significant majority of the mobile market. Android handsets outnumber iPhones by nearly 9 to 1 for instance.
This, coupled with the relative ease of crafting malware for the Android platform, has seen a massive increase in mobile attacks. In July this year, an estimated 10 million Android phones were infected with malware that spied on their owners for instance.
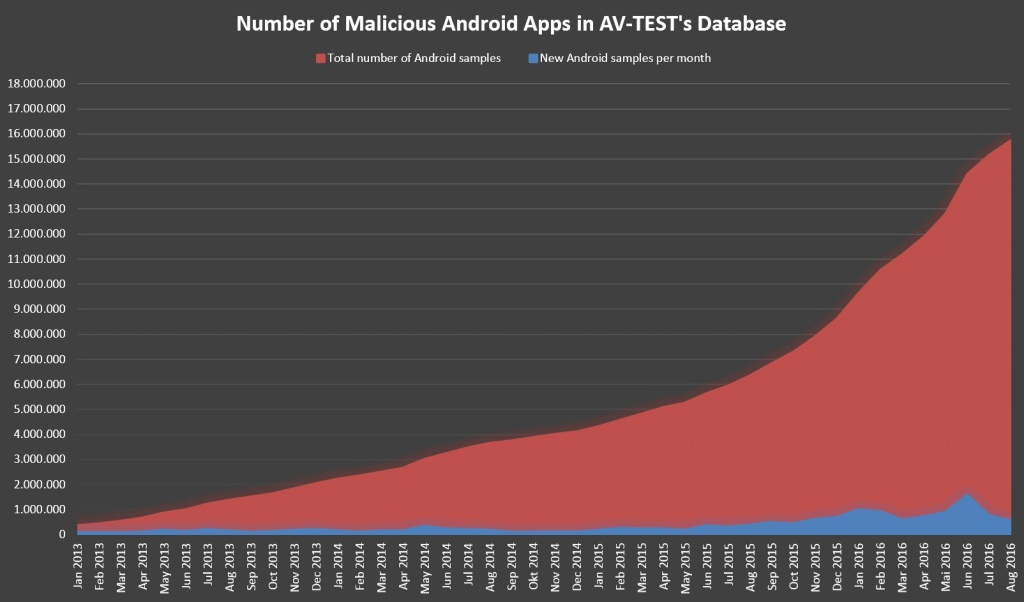
The problem has become steadily worse over time. In January 2013, AV-TEST database of malicious Android apps contained less than 500,000 examples. By August 2016, the total topped 16 million as the number of new malware variants released continues to grow.
The open nature of Android that allows anyone to create software and access key system resources – seen by many as one of the operating system’s strengths – makes it even easier for hackers to create malware and infect phones. This problem is compounded by the infrequency of software updates to patch these vulnerabilities, leaving Android users at risks for months.
Protecting your Android handset against malware
Just like your PC, you have the responsibility for keeping malware from being installed on your phone. There are however a few easy steps to counter the most obvious risks.
1. Always use an official app store
The Google Play app store is the largest, and most trustworthy source of apps for your phone. All of the apps available there have been checked to ensure they do not contain malware, so you should be safe installing them.
Other app stores or websites are not so stringent, so there is a much higher risk of infection when using them.
2. Treat email with caution
Email has been a particularly effective way of installing malware on PCs, so cybercriminals use many of the same techniques on your phone. Always treat email attachments with caution, and never open anything that looks suspicious.
And if you are prompted to download software unexpectedly, there’s a reasonable chance that someone is trying to trick you into installing malware.
3. Consider installing an ad blocker
Malware can sometimes be downloaded and installed without warning via infected banner ads. Installing an ad blocker app can help prevent compromised banner ads from being displayed – which also stops malware from being downloaded.
4. Install an antivirus app
Your home PC is protected by antivirus software – and your Android smartphone needs the same level of protection. Leaving your phone open to malware installation is a serious risk – and cybercriminals will take advantage eventually.
Panda Mobile Security (also available in the trusted Google Play store) offers maximum protection against malware along with a number of useful tools should your phone be stolen. You are protected against Android viruses and information theft at all times.
Get protected now
These practical steps will help to improve your device security – and stop the most common malware attacks. And because they are simple and straightforward, you can get started right now.
To learn more about protecting your Android smartphone, please check out this guide.
The post Android malware surges again appeared first on Panda Security Mediacenter.
How to handle multiple devices and passwords at once
Feeling overwhelmed by the number of devices and passwords you have to manage and remember? Here are four top tips how to help handle this tech overload.
The post How to handle multiple devices and passwords at once appeared first on WeLiveSecurity.
![]()
CVE-2015-0721
Cisco NX-OS 4.0 through 7.3 on Multilayer Director and Nexus 1000V, 2000, 3000, 3500, 4000, 5000, 5500, 5600, 6000, 7000, 7700, and 9000 devices allows remote authenticated users to bypass intended AAA restrictions and obtain privileged CLI access via crafted parameters in an SSH connection negotiation, aka Bug IDs CSCum35502, CSCuw78669, CSCuw79754, and CSCux88492.
CVE-2015-6393
Cisco NX-OS 4.1 through 7.3 and 11.0 through 11.2 on Nexus 2000, 3000, 3500, 5000, 5500, 5600, 6000, 7000, 7700, and 9000 devices allows remote attackers to cause a denial of service (device crash) via malformed IPv4 DHCP packets to the DHCPv4 relay agent, aka Bug IDs CSCuq39250, CSCus21733, CSCus21739, CSCut76171, and CSCux67182.