Cross-site scripting (XSS) vulnerability in the NetComm NB16WV-02 router with firmware NB16WV_R0.09 allows remote authenticated users to inject arbitrary web script or HTML via the S801F0334 parameter to hdd.htm.
Monthly Archives: March 2017
CVE-2017-7285
A vulnerability in the network stack of MikroTik Version 6.38.5 released 2017-03-09 could allow an unauthenticated remote attacker to exhaust all available CPU via a flood of TCP RST packets, preventing the affected router from accepting new TCP connections.
CVE-2015-4556
The string-translate* procedure in the data-structures unit in CHICKEN before 4.10.0 allows remote attackers to cause a denial of service (crash).
CVE-2015-8234
The image signature algorithm in OpenStack Glance 11.0.0 allows remote attackers to bypass the signature verification process via a crafted image, which triggers an MD5 collision.
University @Avira: Predicting error-related user behavior in Avira Antivirus

The best way to learn Data Science is to do data science. Following this motto, Avira collaborated with the University of Liechtenstein and participated at the winter semester 2016/2017 seminar “Data Science” with a real-world data science problem. Liene Blija, Christian Holder, Jan Plojhar, and Martin Lukšík — four brave students — accepted the challenge to […]
The post University @Avira: Predicting error-related user behavior in Avira Antivirus appeared first on Avira Blog.
Changes coming to TLS: Part One
Transport layer Security version 1.3 (TLS 1.3) is the latest version of the SSL/TLS protocol which is currently under development by the IETF. It offers several security and performance improvements as compared to the previous versions. While there are several technical resouces which discuss the finer aspects of this new protocol, this two-part article is a quick reference to new features and major changes in the TLS protocol.
Faster Handshakes
In TLS, before data can be encrypted, a secure channel needs to created. This is achieved via the handshake protocol in which a cipher suite is negotiated between the client and the server and key share materials are exchanged.
The handshake is initiated by the TLS client utilizing a ClientHello message sent to the server. This message contains, among other things, a list of cipher suites which the client is capable of supporting. The server replies to this message in its ServerHello message by picking one of the cipher suites from the client list and, along with it, the server also sends its key share and the site’s certificate to the client.
The client receives all of the above, generates its own key share, combines it with the server key share and generates bulk encryption keys for the session. The client then sends the server its key share and sends a FINISHED message which contains a signed hash of all the data which was previously exchanged. The server does the same thing by sending its own FINISHED message.

This ends the handshake and results in a cipher suite and a bulk encryption key being negotiated between the client and the server and takes two full rounds of data exchange.1
TLS 1.3 aims to make this faster by reducing the handshake to just one round trip (1-RTT). In TLS 1.3 the ClientHello not only contains a list of supported ciphers, but also it makes a guess as to what key agreement protocol the server is likely to chose and sends a key share for that particular protocol.

As soon as the server selects the key agreement protocol it sends its own key share and, at the same time, generates the bulk encryption key (since it already has the client key share). In doing so, the computers can switch to encrypted messages one whole round trip in advance. The ServerHello also contains the FINISHED message. The client receives the server key share, generates bulk encryption keys, sends the FINISHED message and is immediately ready to send encrypted data. This results in faster handshakes and better performance.2
Faster Session Resumptions
The TLS protocol has a provision for session resumption. The general idea is to avoid a full handshake by storing the secret information of previous sessions and reusing those when connecting to a host the next time. This drastically reduces latency and CPU usage. However in modern times the session resumption is usually frowned upon because it can easily compromise Perfect Forward Secrecy (PFS).
Session resumption can be achieved in one of the two following ways:
-
Session ID:
In a full handshake the server sends a Session ID as part of the ServerHello message. On a subsequent connection the client can use this session ID and pass it to the server when connecting. Because both server and client have saved the last session’s “secret state” under the session ID they can simply resume the TLS session where they left off. -
Session Tickets:
The second mechanism to resume a TLS session are Session Tickets. This extension transmits the server’s secret state to the client, encrypted with a key only known to the server. That ticket key is protecting the TLS connection now and in the future and is the weak spot an attacker will target. The client will store its secret information for a TLS session along with the ticket received from the server. By transmitting that ticket back to the server at the beginning of the next TLS connection both parties can resume their previous session, given that the server can still access the secret key that was used to encrypt it.
In both of the above methods session resumption is done by using 1-RTT (one round trip). However TLS 1.3 achieves this by using 0-RTT. When a TLS 1.3 client connects to a server, they agree on a session resumption key. If pre-shared keys (PSK) are used the server provides a Session Ticket which can be encrypted using the PSK if required.
During Session resumption, the client sends the Session Ticket in the ClientHello and then immediately, without waiting for the RTT to complete, sends the encrypted data. The server figures out the PSK from the session ticket and uses it to decrypt the data and resume the connection. The client may also send a key share, so that the server and the client can switch to a fresh bulk encryption key for the rest of the session.

There are two possible problems with the above implementation though:
-
No PFS when using Session Resumption:
Since the PSK is not agreed upon using fresh Diffie Hellman, it does not provide Forward Secrecy against a compromise of the session key. This problem can be solved by rotating the session keys regularly. -
This can easily lead to replay attacks:
Since the 0-RTT data does not have any state information associated with it, an attacker could easily resend the 0-RTT message, and the server will decrypt the associated data and act on the data it received. One way to avoid this is to make sure that the server does not perform any “important action” (like transferring secret information or making a financial transaction) based on the 0-RTT data alone. For such operations servers can impose 1-RTT session resumptions.
DTLS has an additional concern: during re-handshake it is not known whether the peer is alive at all. Data sent along with the handshake message may have ended up in a black hole, going no where.
Part 2 of the blog discusses the various cryptographic changes found in TLS 1.3 and their implications.
-
TLS 1.2 has an extension called “false start”, which can reduce the initial handshake to 1-RTT, it bundles the client application data with its FINISHED message. ↩
-
The roundtrips mentioned are TLS protocol roundtrips, not actual network roundtrips. In reality you have additional roundtrips due to TCP establishment. Most implementations today provide a way to use TCP fast open to reduce that additional round-trip. ↩
Police Arrest Man Potentially Linked to Group Threatening to Wipe Millions Of iPhones
The British authority has reportedly arrested a 20-years-old young man – potentially one of the member of a cyber criminal gang ‘Turkish Crime Family’ who threatened Apple last week to remotely wipe data from millions of iOS devices unless Apple pays a ransom of $75,000.
The UK’s National Crime Agency (NCA) arrested a young man from London on Tuesday on suspicion of “Computer Misuse Act and
![]()
git-1.8.2.3-2.el5
Security fix for CVE-2014-9938
Hacker Who Used Linux Botnet to Send Millions of Spam Emails Pleads Guilty
A Russian man accused of infecting tens of thousands of computer servers worldwide to generate millions in illicit profit has finally entered a guilty plea in the United States and is going to face sentencing in August.
Maxim Senakh, 41, of Velikii Novgorod, Russia, pleaded guilty in a US federal court on Tuesday for his role in the development and maintenance of the infamous Linux botnet
![]()
Charger, the Most Costly Ransomware to Smartphone Users

Ransomware is evolving and becoming increasingly sophisticated, posing a greater threat to companies and private users alike. This malicious software has shown that it can propagate by using the viral mechanisms of a meme, that it can directly attack corporate servers, or even camouflage itself in false resumes. And now it has made its way to other devices, namely, our smartphones.
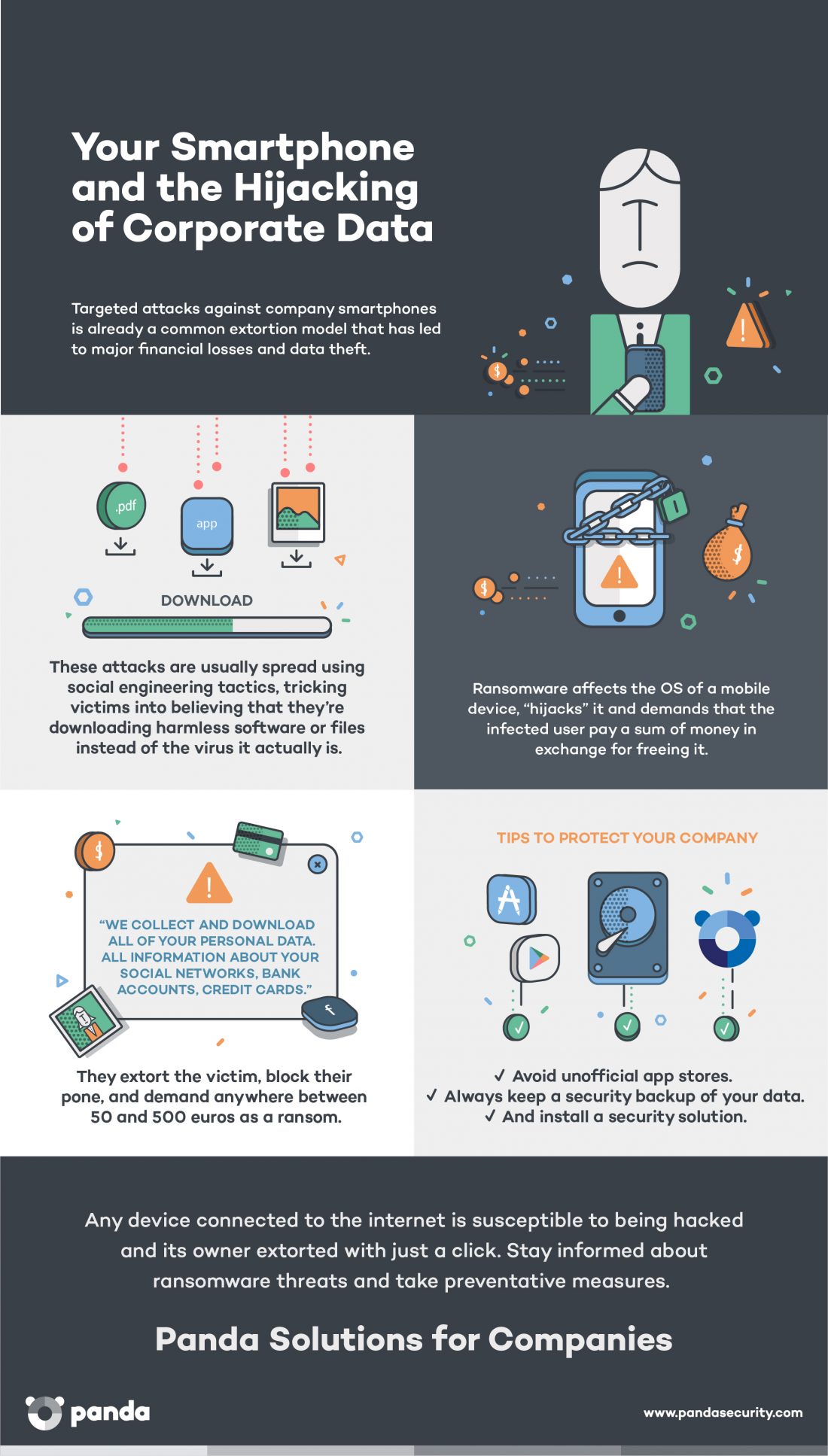 It is now the main threat to mobile devices, until now considered to be relatively virus-free compared with their PC counterparts. Recently, a new ransomware was discovered that goes by the name of Charger, which copies all the data from your agenda, text messages, etc., and seeks admin permissions from the devices owner. If the unwary user accepts the request, the malicious code begins its attack. A message warns the owner that their device has been blocked and their stolen personal data will be sold on the dark web unless they proceed to pay a ransom.
It is now the main threat to mobile devices, until now considered to be relatively virus-free compared with their PC counterparts. Recently, a new ransomware was discovered that goes by the name of Charger, which copies all the data from your agenda, text messages, etc., and seeks admin permissions from the devices owner. If the unwary user accepts the request, the malicious code begins its attack. A message warns the owner that their device has been blocked and their stolen personal data will be sold on the dark web unless they proceed to pay a ransom.
The Most Costly Ransom
Charger’s victims will have to pay 0.2 bitcoins (at about $1000 a bitcoin, it comes out to a round $200) to, supposedly, unblock their device. It may not be the first ransomware to affect smartphones, but never before has this figure been so high.
Also new is its means of spreading. Until now, most cyberattacks targeting mobile phones found their gateway in applications downloaded outside official app stores. With Charger it’s different. Charger attacks Android devices through a power saver app that could be downloaded from Google Play, Android’s official app store.
It is vital for employees to be aware of the dangers of downloading apps from unverified sources. They should also know that it’s not such a great idea to store sensitive corporate data on their computers or mobile devices without taking the proper security precautions. Keeping passwords or confidential documents on an unprotected device could end up giving cybercriminals just what they need to access corporate platforms.
We’ve said it before, and we’ll say it again: new attacks like these come about every day and can take anyone by surprise, be they casual users or security experts. The unpredictable nature of attacks like Charger make an advanced cybersecurity solution indispensable. Perimeter-based security solutions are simply not enough anymore.
The post Charger, the Most Costly Ransomware to Smartphone Users appeared first on Panda Security Mediacenter.
