
Ransomware is evolving and becoming increasingly sophisticated, posing a greater threat to companies and private users alike. This malicious software has shown that it can propagate by using the viral mechanisms of a meme, that it can directly attack corporate servers, or even camouflage itself in false resumes. And now it has made its way to other devices, namely, our smartphones.
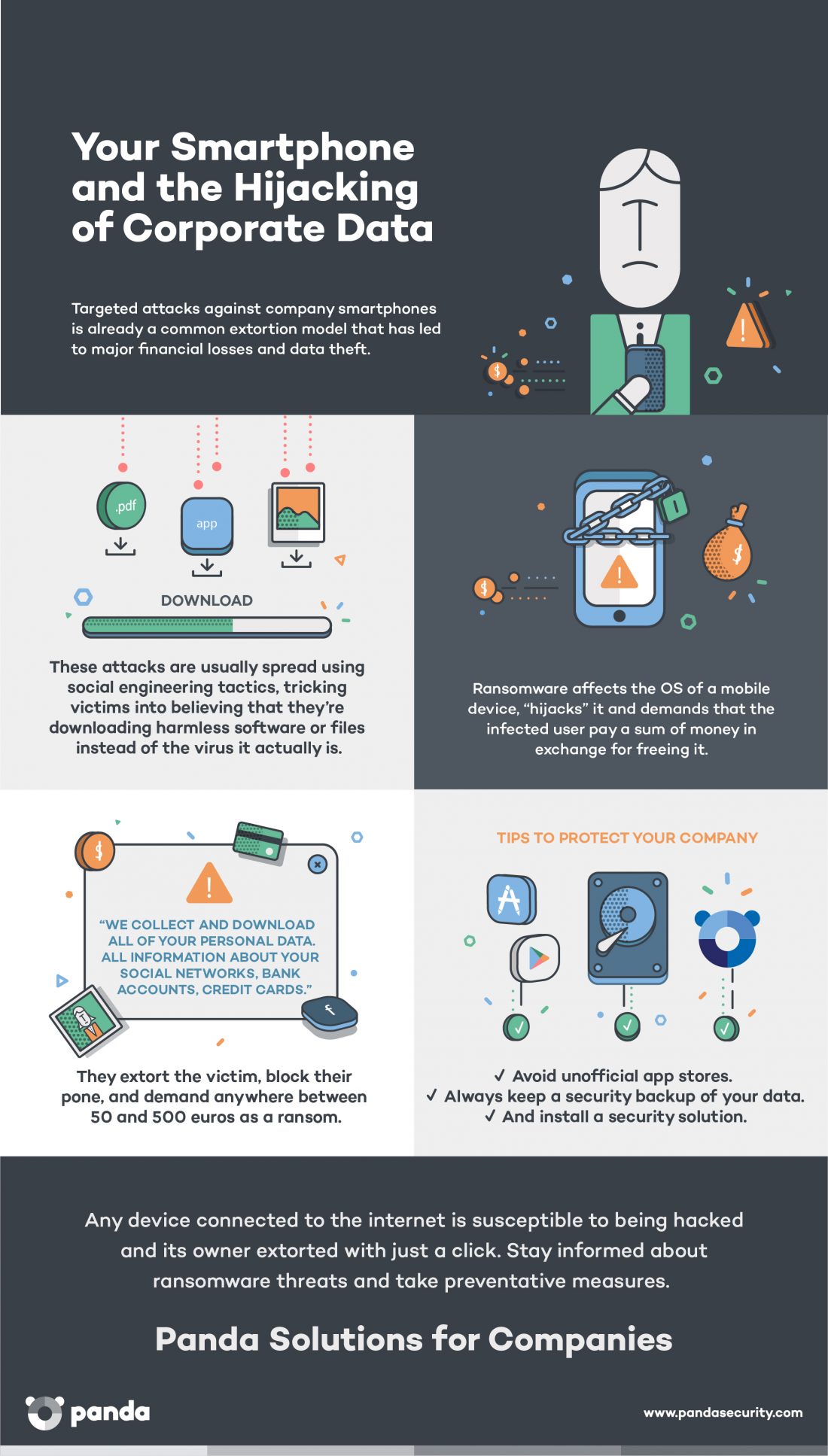 It is now the main threat to mobile devices, until now considered to be relatively virus-free compared with their PC counterparts. Recently, a new ransomware was discovered that goes by the name of Charger, which copies all the data from your agenda, text messages, etc., and seeks admin permissions from the devices owner. If the unwary user accepts the request, the malicious code begins its attack. A message warns the owner that their device has been blocked and their stolen personal data will be sold on the dark web unless they proceed to pay a ransom.
It is now the main threat to mobile devices, until now considered to be relatively virus-free compared with their PC counterparts. Recently, a new ransomware was discovered that goes by the name of Charger, which copies all the data from your agenda, text messages, etc., and seeks admin permissions from the devices owner. If the unwary user accepts the request, the malicious code begins its attack. A message warns the owner that their device has been blocked and their stolen personal data will be sold on the dark web unless they proceed to pay a ransom.
The Most Costly Ransom
Charger’s victims will have to pay 0.2 bitcoins (at about $1000 a bitcoin, it comes out to a round $200) to, supposedly, unblock their device. It may not be the first ransomware to affect smartphones, but never before has this figure been so high.
Also new is its means of spreading. Until now, most cyberattacks targeting mobile phones found their gateway in applications downloaded outside official app stores. With Charger it’s different. Charger attacks Android devices through a power saver app that could be downloaded from Google Play, Android’s official app store.
It is vital for employees to be aware of the dangers of downloading apps from unverified sources. They should also know that it’s not such a great idea to store sensitive corporate data on their computers or mobile devices without taking the proper security precautions. Keeping passwords or confidential documents on an unprotected device could end up giving cybercriminals just what they need to access corporate platforms.
We’ve said it before, and we’ll say it again: new attacks like these come about every day and can take anyone by surprise, be they casual users or security experts. The unpredictable nature of attacks like Charger make an advanced cybersecurity solution indispensable. Perimeter-based security solutions are simply not enough anymore.
The post Charger, the Most Costly Ransomware to Smartphone Users appeared first on Panda Security Mediacenter.






 In addition to the physical iPhones, a new operating system is also added to the new 7. The iOS 10 is presumed to be more robust in terms of cybersecurity (this is great news, especially after discovering various faults in the beta operating system).
In addition to the physical iPhones, a new operating system is also added to the new 7. The iOS 10 is presumed to be more robust in terms of cybersecurity (this is great news, especially after discovering various faults in the beta operating system).


