Wi-Fi and encryption
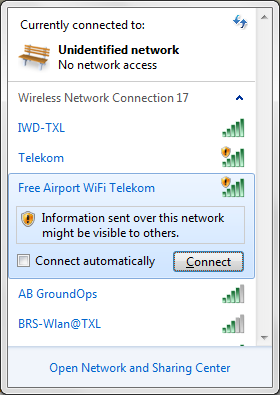
Data transmitted over a wireless network can be either unencrypted or encrypted. While both options are available to users, the use of open, unprotected Wi-Fi networks has become increasingly popular across the globe. In the case of open wireless networks, the transmitted data are unencrypted and might be visible to others, as is shown in the screenshot below. To resolve this issue, many wireless networks use password protection. However, the method and strength of these passwords matter: if a weak encryption method, such as WEP, is used, an attacker can simply crack the password and decrypt the device’s communication. Hence, the use of a strong encryption such as WPA/WPA2 is suggested. The length of a password is another important factor to its strength — a strongly encrypted communication with a short key length can still be cracked by hackers within a short amount of time. Because of this, a key length of longer than 8 characters is strongly recommended.
(Figure 1: List of available wireless networks featuring both encrypted and unencrypted options.)
Introduction
In February, we sent several volunteers to 9 cities: Chicago, New York, San Francisco, Berlin, Barcelona, London, Taipei, Hong Kong and Seoul. Our goal was to gather as much information about the use of wireless networks in these cities as possible.
Each volunteer was equipped with a laptop and a WiFi adapter with ability to be switched into monitor mode. This feature allowed us to listen to all wireless communication — even that which wasn’t targeted to our device. This way, we could listen to the data transmitted between the access point and devices receiving it.
(Figure 2: Laptop and Wi-Fi adapter hidden in the bag. )
Each volunteer walked around a city with an adapter tucked away in his or her bag that constantly listened in on nearby wireless communication.
For this experiment, we developed our own application called Trafi Canal, which was based on the free tool Microsoft Network Monitor. This application logged interesting wireless communication data and stored it for later statistical analysis.
(Figure 3: Avast’s traffic analyzing application, Trafi Canal)
This application monitored the wireless traffic at 2.4 GHz frequency and logged the identifiers of hotspots, identifier addresses of devices connected to the hotspots, sources and targets of the communication, and GPS coordinates.
Destinations
The German capital was one of the destinations in our experiment that yielded impressive results. Our volunteer spent one full day walking around the city collecting data.
(Figure 4: Monitoring in front of German Bundestag, Berlin. The Wi-Fi adapter can be seen on the left of the laptop.)
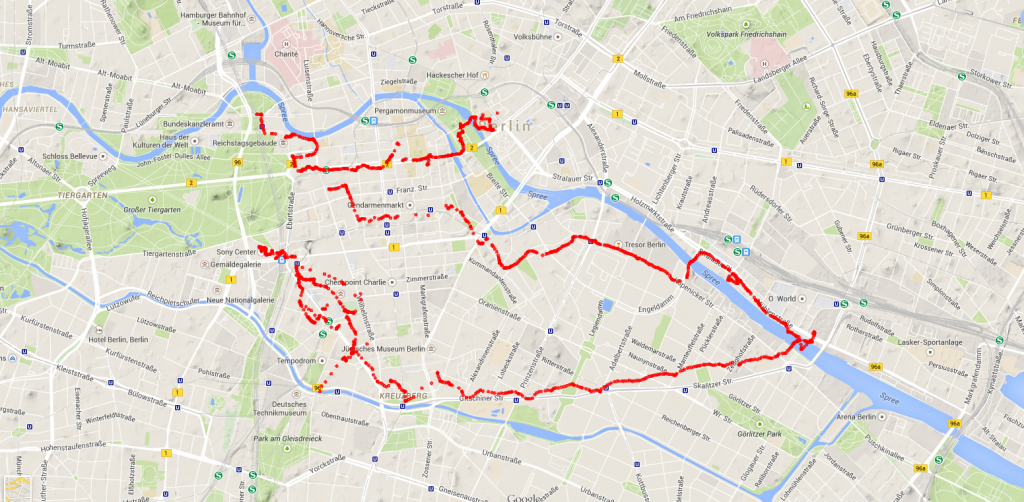
Throughout the day, the Trafi Canal app collected GPS coordinates of our volunteer’s movements. The map below shows the extensive route he took around Berlin’s city center.
(Figure 5: Walking coordinates in Berlin)
Throughout the day, our volunteer encountered more than 8,500 hotspots and came into contact with more than 23,000 devices. If you think our data collected in Berlin is large, imagine the total number of hotspots and devices we encountered throughout all of the 9 metropolitan areas that we visited!
Statistics
After collecting the data in each of the cities, we wrote a script to automatically analyze and process the acquired data. We focused on the most popular channels that hotspots use: encryption types, mostly typical SSIDs, and analysis of communication.
Berlin:
Although there are 14 channels in 2.4 GHz, not all of them are commonly used for communication. To avoid interferences in Wi-Fi networks, channels 1, 6 or 11 are recommended; however, not everyone follows that recommendation. To give you a better idea of the channels’ usage, here’s how it looks with Wi-Fi channels in the center of Berlin:
| Channel 1 | 16% |
| Channel 2 | 9% |
| Channel 6 | 11% |
| Channel 11 | 13% |
| Channel 13 | 8% |
In addition to hotspots’ channel usage, it’s also interesting to note that while slightly less than one half of hotspots (48%) are encrypted with strong WPA encryption, 3% use weak WEP encryption, and the remaining 26% have no encryption at all. In Berlin, we encountered a total of 8,731 hotspots, 42% of which had devices connected to them. We observed 5% of users communicating — 11% used unencrypted HTTP communication and another 21% encrypted HTTPS communication.
Each hotspot has a unique identifier (BSSID) and a name (SSID). As you might already know, Wi-Fi hotspot names are not unique and are often repeated (e.g. “Free Wi-Fi”). However, not all hotspots broadcast their names (SSID). In Berlin, in 11% of hotspots’ SSIDs are not broadcasted whatsoever.
Most typical hotspot names we encountered.
| KD WLAN Hotspot+ | 2.40% |
| HolidayInnExpress | 1.48% |
| Telekom | 1.07% |
| eduroam | 0.72% |
| dlink | 0.71% |
| FRITZ!Box 6360 Cable | 0.70% |
| FRITZ!Box 7362 SL | 0.65% |
| HU-VPN | 0.62% |
| HU-VoIP | 0.61% |
| HotelNET | 0.58% |
The 5 most visited domains in Berlin are Google, Amazon, Facebook, Akamai and Yahoo:
| .1e100.net (Google) | 45% |
| .amazonaws.com | 13% |
| .facebook.com | 13% |
| .akamaitechnologies.com | 9% |
| .yahoo.com | 7% |
The most popular device manufacturers of connected users were:
| Apple | 31% |
| Intel Corporate | 8% |
| TP-LINK TECHNOLOGIES CO.,LTD. | 5% |
| Samsung Electronics Co.,Ltd | 5% |
| LG Electronics | 3% |
| Sony Mobile Communications AB | 3% |
Additional results
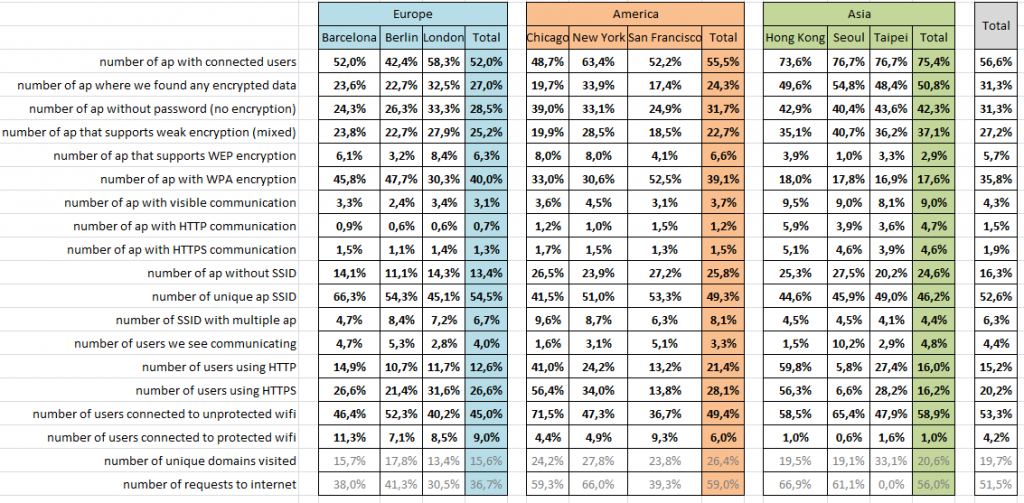
The process of collecting data was similar in all the cities we visited. For the brevity of this report, we will summarize the rest of our findings in the following table:
Summary
- While users in Asia were most likely to join open networks, Europeans and Americans were slightly less so.
- A significant portion of mobile users browse primarily on unsecured HTTP sites.
- Nearly one half of the Web traffic in Asia takes place on unprotected HTTP sites, compared with one third in the U.S. and roughly one quarter in Europe.
- San Francisco and Berlin had the lowest percentage of weakly encrypted hotspots, compared to more than half of hotspots in London and New York and nearly three quarters in Asia.
Conclusion
The data transferred via unencrypted HTTP traffic are transmitted in plain text and may be visible to potential hackers. If a user uses SSL, we cannot read the data which are being transmitted, but we can still determine the domain the user is accessing. For example, we could see that that a user is visiting an email provider, but we cannot decrypt the actual data he or she transmits on the provider.
If user uses a VPN, an attacker is only capable of viewing the encrypted traffic from his or her computer to the VPN server The attacker doesn’t know which websites the user visits nor the content he or she transmits. Due to the fact that the installation and configuration of a virtual private network can be difficult for the average user, Avast offers an easy-to-use VPN solution called Avast SecureLine VPN.
Acknowledgements
The Wi-Fi hack experiment was conducted by the following people:
Antonín Hýža, Jaromír Hořejší, Jerry Khan, Chun Lin Tu, Alex Grimaldo