Cybercrooks take advantage of the busy holiday season to launch scam campaigns.
Be aware that cybercrooks send “special” offers via fake email campaigns during the holiday season.
The holiday season is a time for decorations, cheerful music, shopping, spending time with loved ones, and unfortunately, for cybercriminals hoping you will fall for phishing scams.
“Cybercriminals use the same tactics they always do, but target people more during the holiday season with “special” offers via fake email campaigns. These fake email campaigns can trick people into downloading malware and/or can trick people into giving attackers their personal information”– Jan Sirmer, senior malware analyst at Avast.
We decided to take a look at a few recent examples of malicious emails, more specifically their email subject lines and the email addresses they were sent from. Our goal was to see how cybercriminals are taking advantage of the holiday season.
Here’s what you should look out for:
-
The Fake Holiday Offer
Whether it be membership offers or special shopping deals, be cautious of the offers you receive around the holidays by email. Some of them might be too good to be true and are fake or some may come from trustworthy businesses whose email accounts have been hacked. Here is an example:
‘CHRISTMAS OFFERS.docx’ From: “Nicole*” <[email protected]*
This could be a tempting offer, especially if your upcoming New Year’s resolution is to lose weight. The original email address belongs to an actual business owner, lending credence to the scam. Unfortunately, cybercriminals understand this and misuse business email addresses, such as this, to send out phishing emails to customers, because they know customers trust the business and there is a better chance they will fall for the scam.
-
The Fake Shipment Updates
Cybercriminals are also aware how important it is to receive online orders on time, so they spoof package delivery services, using emails with subject lines such as: ‘Your latest DHL invoice: MSE7396821′ from [email protected] and ‘Reminder: Shipment status change for package # 82274150′ from: “USPS 2015″ [email protected] are being sent.
It is always important to pay attention to the email address the email is being sent from, not just the name attached to the email address. You can also check if the email is real by visiting the shipping site directly from your browser to track your order. If the package or invoice number do not appear in the system, then you know the email is a scam and should delete it.
-
The “Congratulations you won a gift card!” … Not!
Money can get tight around the holidays, so you may be tempted by scams that offer gift cards or cash. Here are some of the scam emails we have seen offering cash for the holidays:
‘Cash Out for the Holidays’ from “U.S. Bank Consumer Finance Wholesale Mortgage” [email protected]
Incoming email ‘Apple Store Gift Card’ From “Apple AppStore” [email protected]
It is safe to say that washbowlsnm531 probably isn’t an Apple employee…
And here are two classic spam emails we have all probably seen before:
‘You WON best buy gift card 500$’ from Best Buy [email protected]
‘AMAZON e-giftcard 100$’ from “Amazone.it” [email protected]
-
The holiday e-card! – from your favorite Cyber Criminal
To move away from the shipping and offer scams for a moment, criminals are also taking advantage of people’s excitement over holiday e-cards. We discovered multiple emails claiming to contain a Hallmark e-card from various “Hallmark” email addresses, but we took a closer look and found that most e-card and online gifting services send out greetings from the sender’s email address, not from the company’s email addresses. Hallmark has been targeted by fraudulent emails, like the ones below, so often in the past that they have a dedicated a support page to address the problem.
Scam Holiday e-cards:
‘You’ve received A Hallmark E-Card!’ from [email protected]
‘You have received A Hallmark E-Card!’ from [email protected]
If you receive an email from Hallmark or another online greeting company or gifting service’s claiming you have received an e-card or gift, do not open it or open any attachments or links. Again, these emails should be sent to you with your friend’s email address and if you are not sure, contact the service directly to confirm the email is safe.
How to protect yourself from the Grinches of the cyberworld
Jan Sirmer, senior malware analyst at Avast, shares some tips on how you can protect yourself from the various phishing scams going around during the holiday season:
“It is vital you have antivirus installed on all of your devices (laptops, android phones). Antivirus software, like Avast, will detect and block phishing attacks before they can affect you. You should also make sure all of the software on your devices are up-to-date. Attackers often exploit vulnerabilities, which can be found in outdated software. Finally, you should always be cautious when opening links or attachments in emails. If anything seems off, double check to make sure the email actually came from a trusted source – better to be safe than sorry!
*Name and email address have been changed to protect the business that was hacked
Follow Avast on Facebook, Twitter, YouTube, and Google+ where we keep you updated on cybersecurity news every day.
![]()




 If you want to choose a shopping app based on the amount of unnecessary permissions it collects then Walgreens is the app for you!
If you want to choose a shopping app based on the amount of unnecessary permissions it collects then Walgreens is the app for you!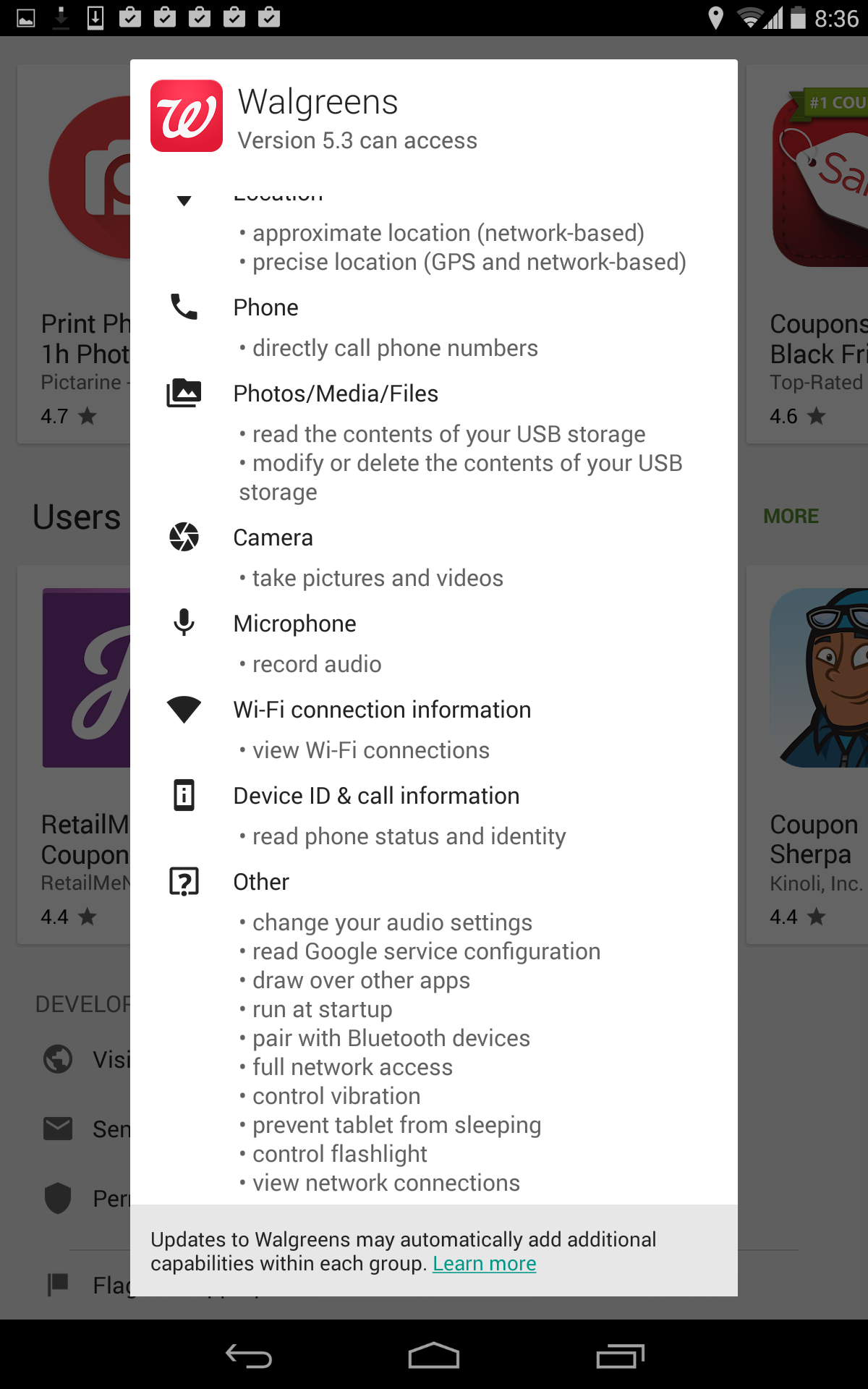








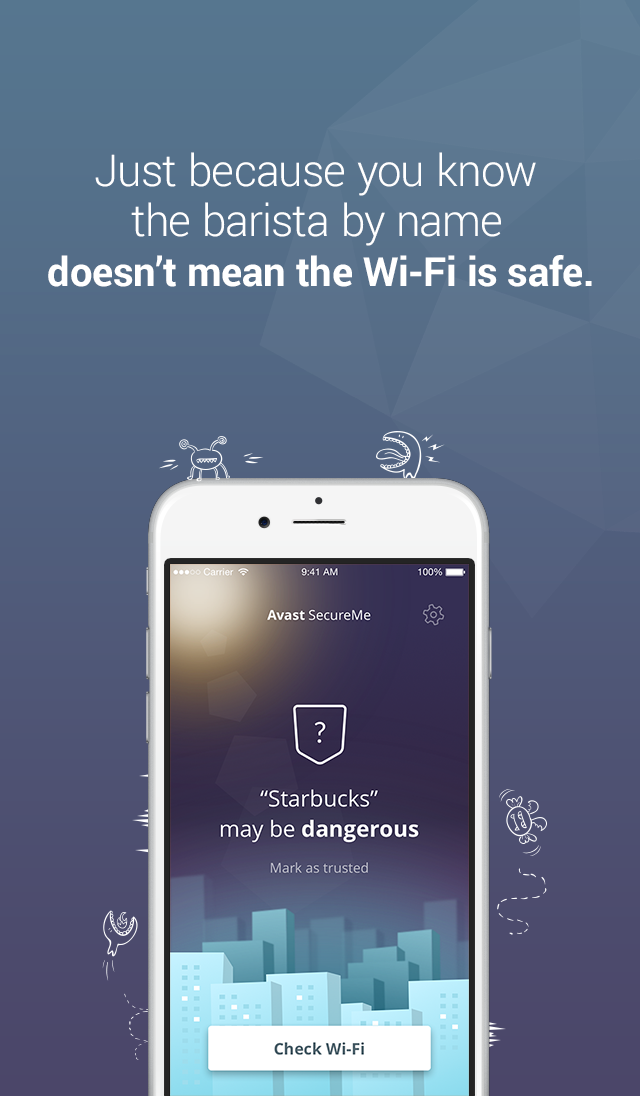
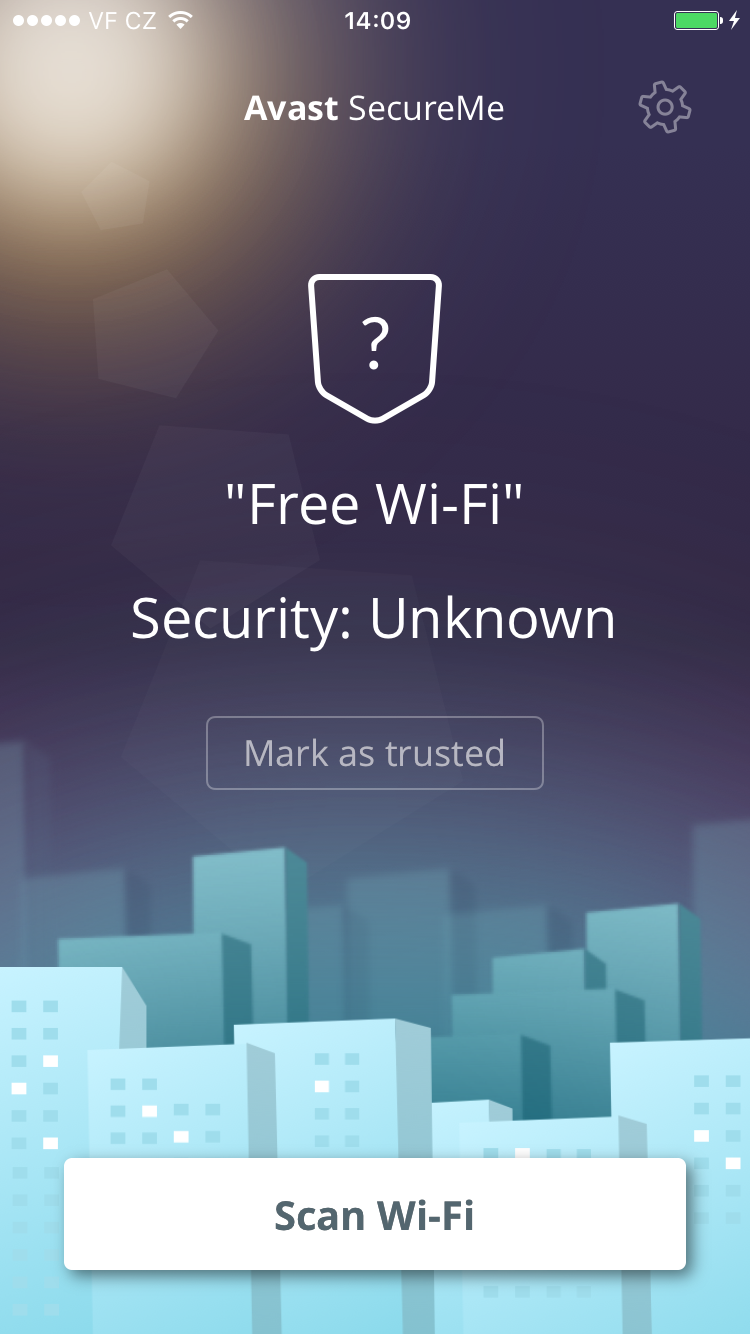
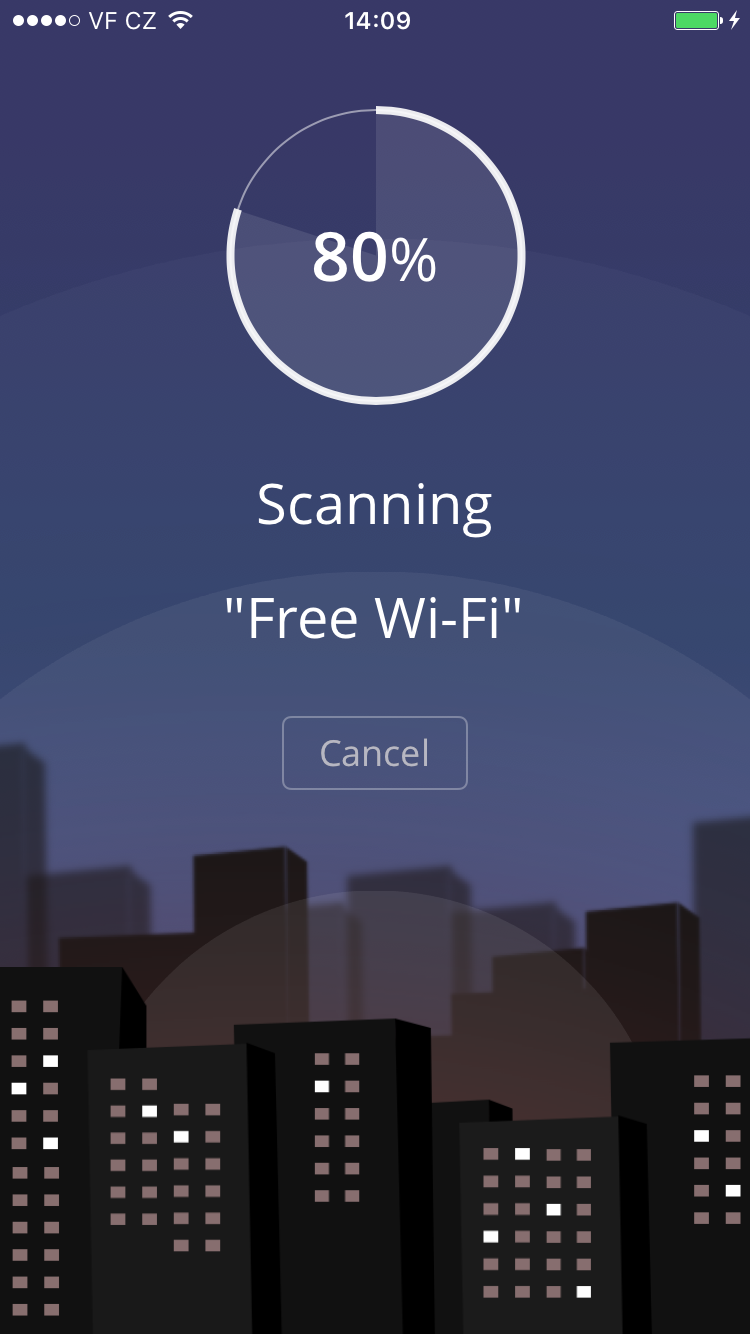
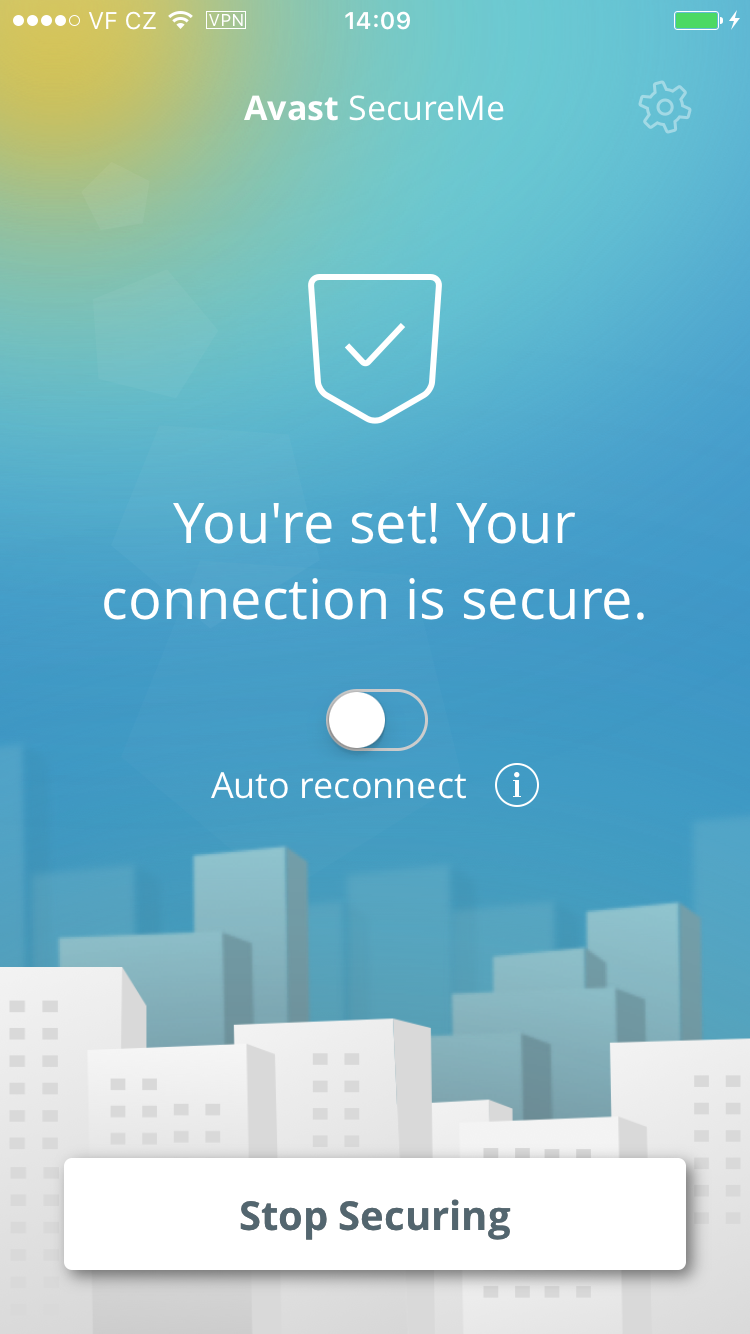



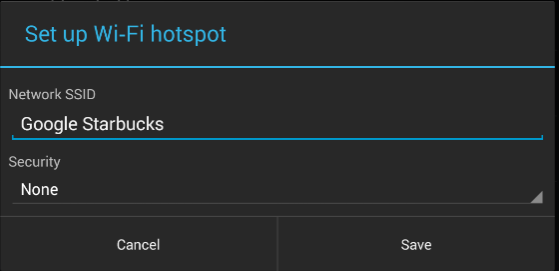
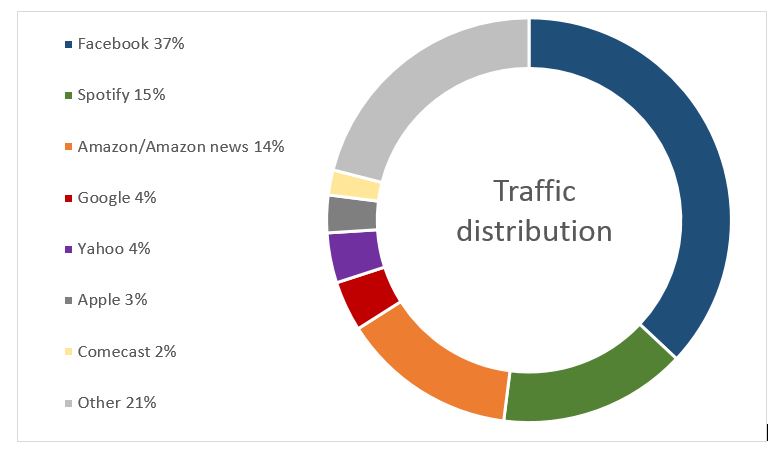
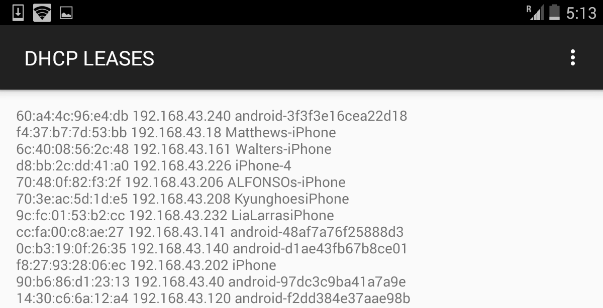 From data we gathered in seven hours, we found that 264 people connected to our fake Wi-Fi networks and generated 512,000 data packets*.
From data we gathered in seven hours, we found that 264 people connected to our fake Wi-Fi networks and generated 512,000 data packets*.