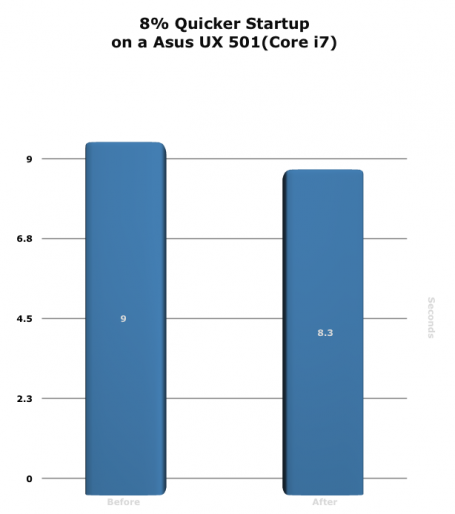
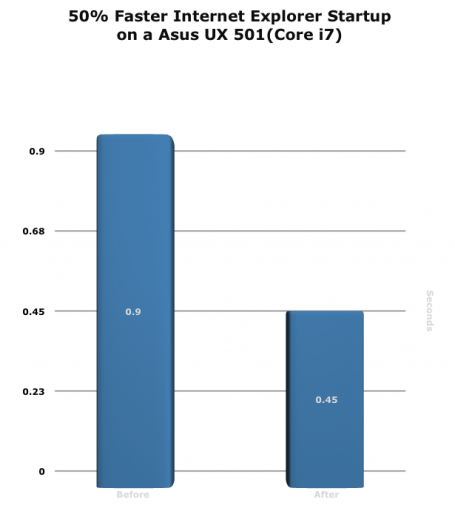
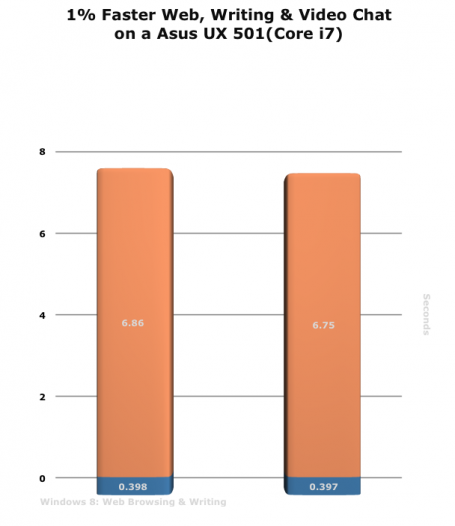
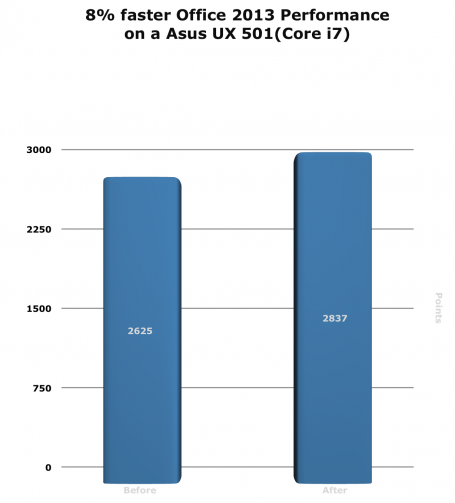
It’s no secret that personal data and private information left lying about, either in physical or digital form, can be used by thieves to steal your identity. The problem is that securely destroying old documents, especially if you have boxes and boxes of them, can be time-consuming and frustrating.
And if you don’t destroy your data securely the consequences of being a victim to identity theft can range from outright theft of money, to unexplained debts, leaving you feeling like somebody else has taken over your life.
But thanks to a growing movement called #ShredFest originally from New York, things might get a little easier. It’s a subsidised program designed to provide secure document destruction free-of-charge. You might already have something similar in your local area, sometimes run by local banks and communities once or twice a year – or perhaps this is your opportunity to make-it-happen!
The statistics on Identity theft are nothing short of shocking. In the United States the Federal Trade Commission reports that in 2014 it received 332,646 complaints making ID theft the number one reported crime for the 15th year in a row.
Stolen identities used in the United States in 2014 were used mostly for Government and benefits related fraud (30%) followed by Credit Card fraud (26%), Phone/Utilities fraud (16%) and Bank fraud (10%).
With the ability for criminals to collude easily on a global scale, it’s not inconceivable that we will see ID theft attempts in the future combine information obtained from the litany of online data breaches (for example, Ashley Madison), along with tidbits obtained through “dumpster diving” right at your own back door.
Fortunately, with a few simple precautions and some dedication to properly destroying the remnants of your online correspondence, and other important paperwork (that you’re no longer required to keep by law), you should be able to reduce the risk of ID theft happening to you.
Destroying Physical Documents
Got boxes of documents that you should be securely destroying? Despite #ShredFest only being available in a small number of locations at the moment, a quick search online reveals many companies that provide shredding services for a small fee.
But weighed up against the risk of ID theft against you at any time, it may well be worth it at any cost; and think of how a quick trip to your local shredding depot with a car-load of documents is not only going to put your mind at ease – but all that storage space you’ll get back at home!
Another alternative is to purchase your own document shredder – something that I have owned for many years and highly recommend – however, those boxes of tax paperwork may still be inescapable, so an annual trip to #ShredFest is likely still needed.
If you do purchase your own shredder, however, consider one that has a “cross-cut” feature (that cuts the paper into smaller pieces) which is considered a little more secure, and also there are models that can shred old CD-ROMS and DVDs which can come in handy.
Shredding Computer Files
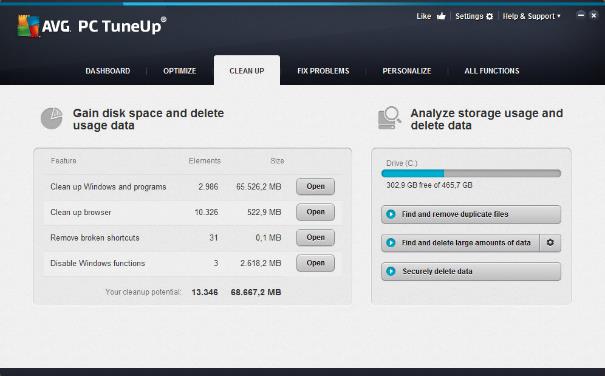
Did you know that selecting a file and pressing delete, or simply moving the file to the trash (even after you empty it) isn’t enough to securely remove it? It’s important to understand how to securely delete digital files on all your devices – not just your PCs, but also Mobile devices.
We’ve covered in the past how easy it is to use features like AVG’s File Shredder which can overwrite your private and personal files multiple times to ensure they cannot be recovered again.
Also if you’re recycling your old PC’s or Mobile devices, including disposing of them permanently, ensure you have taken all reasonable steps to correctly erase the data on them – this sometimes isn’t as easy as a simple factory-reset, particularly with older Android mobile devices.
Lastly, if you have an online email account (such as Gmail, Yahoo or Outlook.com) you’re likely holding on to years worth of old email that could prove to be extremely valuable to an ID thief. As I suggest in these tips about securing your online email account, make sure you purge all your old and unwanted email too.
Until next time, stay safe out there.
![]()
![]()