Unlimited backups of all your photos. For free. Now that’s hard bait to refuse, especially considering how photo-happy we’ve all become since our smartphones have replaced our pocket cameras. But this offer is just the tip of the iceberg in Google’s new app. After all, if you’re going to be uploading thousands upon thousands of photos, you’d expect sorting them would be a pain.
Google’s answer to that seems to be: Don’t. Instead, trust us to deliver the right photos when you use our in-app search bar.
Searching Photos
Google’s new Photos app leverages the search giant’s recent investments in machine learning to “read” your photos and figure out what they’re about without any need for you tag, label or date them.
Looking for photos of that holiday in London? Type “London”, and even without geo-location data enabled, Google’s algorithms will “read” the photos for any landscape it can recognize as coming from Old Foggy.
Type in “dog”, and it will do the same, pulling any photos of dogs it can find in your collection. If you’ve ever tagged a photo of your pet with its name, it will learn that too, and show you photos of “Rex” alone if you ever search for it.
None of this is happening with your input: Google’s engines have just learned to look at your photos, and understand what they’re looking at.
Facial recognition
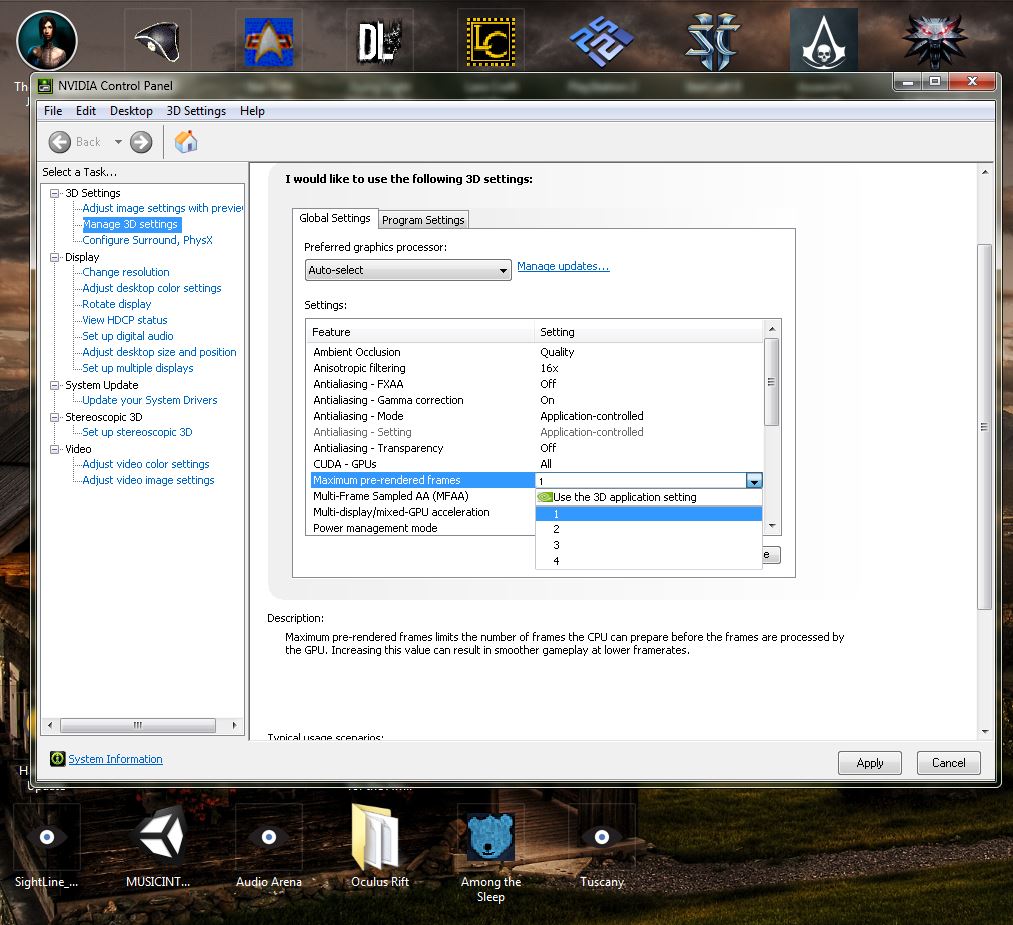
Another feature you can choose to activate or deactivate, is the system’s ability to sort through faces. When you hit the search bar, you’ll be presented with a series of faces it has pulled out. Tap on one, and most if not all of the photos you have of that person will be presented. If your photo collections go back far enough, the system will sometimes be able to recognize the person as far back as childhood.
While not 100% accurate, it’s damn impressive, very useful, and whole lot of creepy.
Dealing with the Privacy Devil
The story of Faust is a quite apt description: in exchange for incredible powers, Dr. Faust sold his soul to the devil. You can bet that Google is not offering this much free backup storage and amazing machine analysis out of the goodness of its heart.
Just as Gmail made a breakthrough in the email market by offering enormous amounts of free storage in exchange for data-mining your communications to sell against ads, you can put down some good money on Photos going the same way.
While Google has affirmed that they will never sell your photos to third parties or publish them without your consent, that’s most likely not how they intend to use your collections. Instead, they will use them to get to know you better.
However the system manages it, it is somehow labeling your photos so that when you search for a term, it can deliver results against it. It will also be doing it for terms you may never search for.
Happen to be wearing Adidas shoes in a photo? In the future, you can expect Google Photos to make note of that, and the next time you are near a shoe store, don’t be surprised to receive discounted offers from Adidas.
Again, it’s unlikely that Adidas will ever see your photos. It will instead ask Google to target all the relevant users on its behalf.
In many ways, this is nothing new: it’s exactly the way any of Google’s other services work, whether that be Gmail, Google Now, or even the main Google search engine. Indeed it is how nearly all major web companies operate.
But it is taking that data-mining to a new, uncomfortably close-to-home level.
![]()
![]()