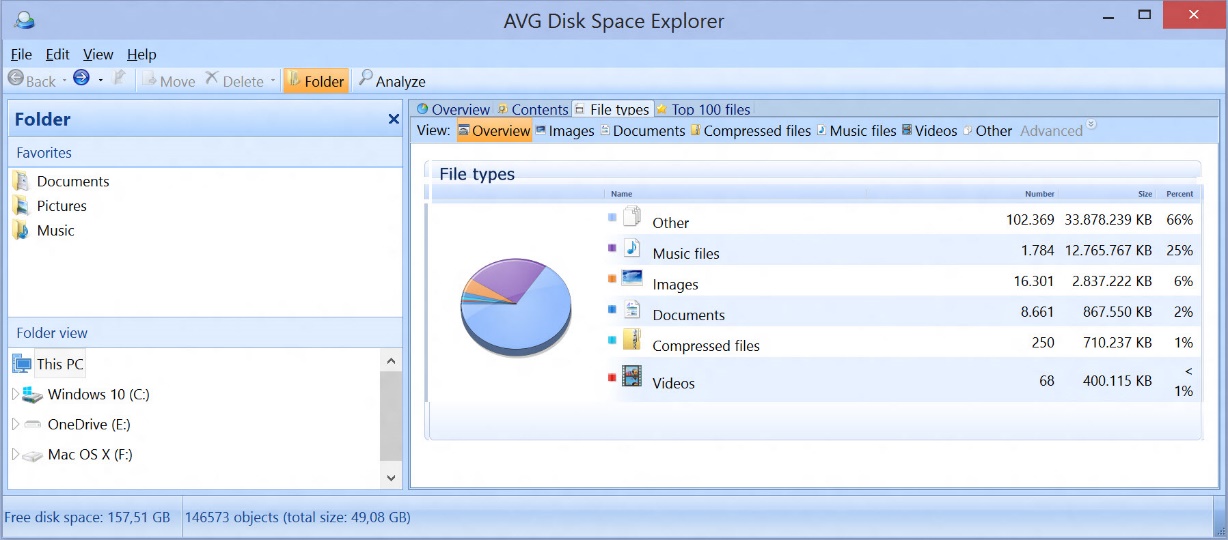
In AVG’s latest “App Performance Report” for Q4, we’re looking again at the anonymous data from over one million AVG users, compare it to our first report, and reveal what apps are the most resource-hungry on their phones.
When looking at one million of our users, we found many interesting trends that might just surprise you:
Spotify is now the No 2 resource consuming app overall:
Out of our total user base, 638,716 users had the music streaming service Spotify installed: what they perhaps didn’t know is that Spotify is now the second most resource-consuming app in the store (up from rank 5 in Q3).
If you’re low on battery, space or data, keep that streaming to a minimum!
The changing gaming landscape
In our previous report, uber-popular FarmVille and Puzzle & Dragons topped the charts for the most resource-hungry games for Android. However, they were nowhere to be found in our Q4 roundup. A closer look shows Puzzle & Dragons and FarmVille suffered from a 50% and 43% decline respectively in installed user base in Q4 when compared to the beginning of the year (Q1/Q2).
New games such as Boom Beach and Deer Hunter 2014, however, appeared out of nowhere and secured the top spots in both usage and resource usage (not surprisingly, they’re games after all!).

[SUBLINE] Massive decline for Farmville and a rise of Deer Hunter 2014.
Samsung’s New Updates
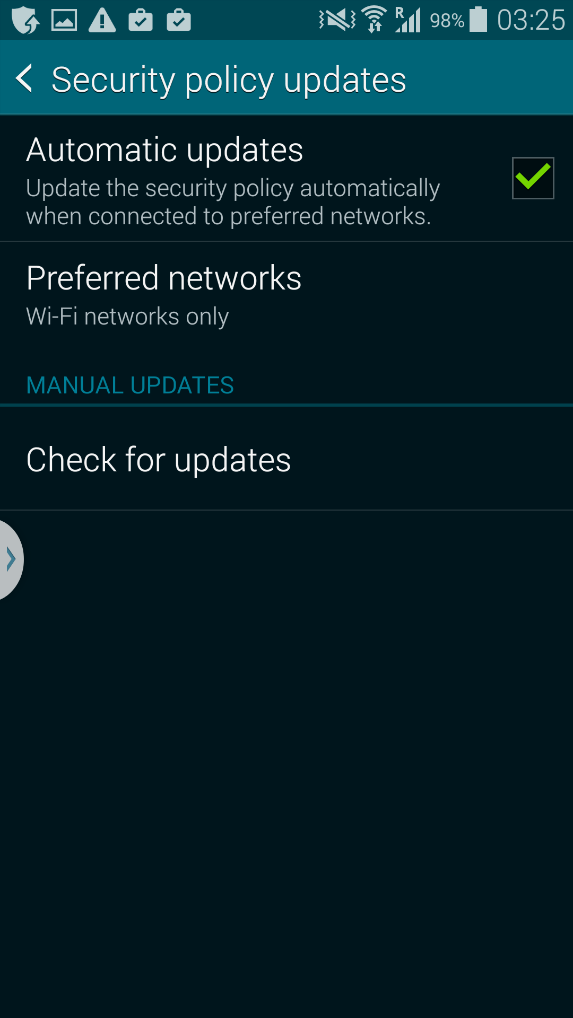
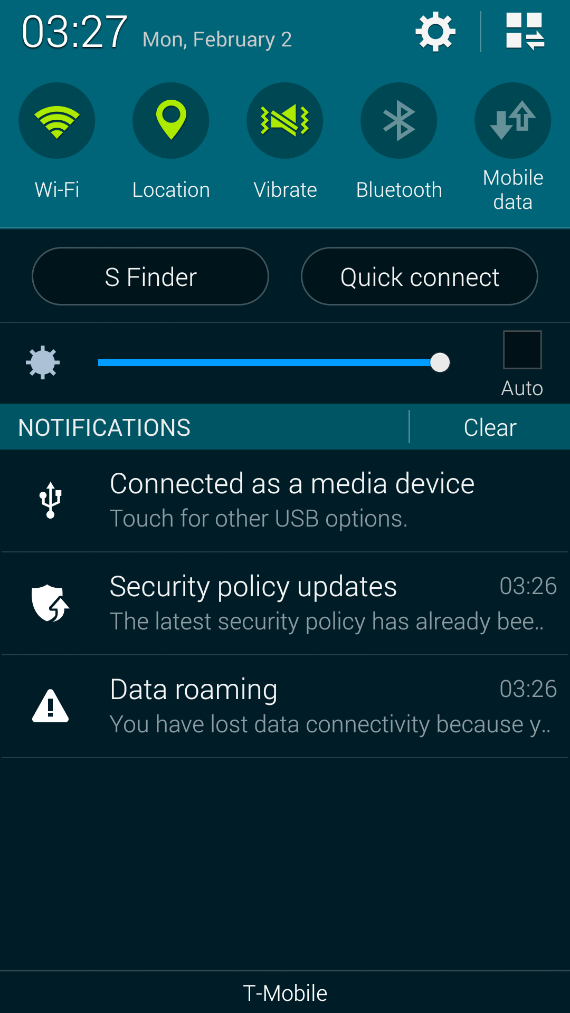
After the rollout of Android 4.4.2 (October 2014), we noticed a new entry in our top battery drainers that run immediately at start up. Samsung’s Security Policy Update service, officially named Samsung KNOX™, automatically checks for security updates and downloads these automatically. While Knox is a great addition to having a full-featured antivirus product installed, a number of users and even journalists have publicly complained about not just the amount of notifications shown but also a 30-40% drop in battery life.
As mentioned in this ZDNet article, this feature cannot be turned off as mentioned by the Samsung Technical Support: “To ensure that your device always has the latest security to protect you and your data, Samsung will occasionally send security updates to the device as needed. I’m sorry to inform you that there is no option to disable these updates”.
While we can’t stress enough that security on mobile device is critical, handset makers need to ensure their product does not reduce battery life or impact overall performance drastically.
Self(ie) awareness

Taking selfies was “the” cool thing to do in 2014: selfie sticks, selfie apps, selfie phones all flooded the market. Unfortunately, some of these apps can be quite draining on a device’s battery. A new app called Candy Camera – Selfie Selfies crept up to number 7 in the top battery hungry apps that run in the background. We suggest avoid apps like these as they only should drain battery when you’re actively running them!
Maps & Navigation
Did we spend more time navigating and looking at maps? With more time off over the festive period, both Waze (Social GPS Maps & Traffic) and also Google Maps climbed into the Top Usage Chart:
Less gaming, more talking
Another seasonal effect: compared to Q2 and Q3 of 2014, we spend much more time on social networks and communicating through messenger apps instead of gaming. While we still spend most 49% of our time gaming on our Android devices compared to 62% in the previous quarter, social and communication apps rose to 11% and 10.3% of our total usage (compared to 6% and 3% respectively before)
Again, find a full list and all the data in our app report here.
So what are you supposed to do if you’ve got one or even many of our resource drainers installed? Find out in our top tips in the next blog!