We normally make fun of this, or just totally ignore it. We know that it probably is a scam. So, if we don’t believe those ads, why do we believe in some apps? Apps that advertise things like:
- Get free stuff in our shop through your favorite social network with the ‘Just click and win’!
- Fix your computer; increase your RAM and hard disk space all in one click with ‘Ultra Optimizer Plus’!
- Install this app on your phone to get ‘Sexy videos on your phone for free

 ‘!
‘!
- Buy the NEW SUPER SHINY (not official) Video ‘Not-Fake Player’!
Nowadays Social Networks appear to be the best places to find victims for scams. Who hasn’t seen offers like “Like and share to win an iPhone”, “See the leaked video of the last Pop Star”, “New Facebook features!” and so on Facebook? These are – of course – usually tricks to make you fall for a scam.
facecrooks has a huge list of Facebook related scam. Below are just two of the countless examples:
Free iPhones: Like the Facebook page and share the picture. It is easy to win a phone right? Wrong. There is no iPhone and you will be spammed from this page (pages can be sold as advertising spaces) because you gave them a like.
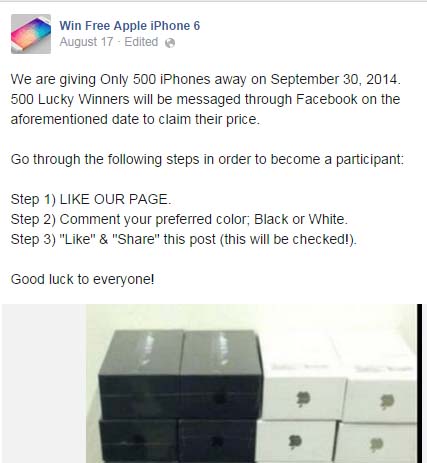 Picture from facecrooks.com
Picture from facecrooks.com
Profile viewer: Don’t you want to know if the girl from school or the boy from work is seeing your pictures? So better ask them because these kinds of plugins/features/apps don’t work. Normally behind these links you will find some PUA or Adware ready to be downloaded and installed on your computer.
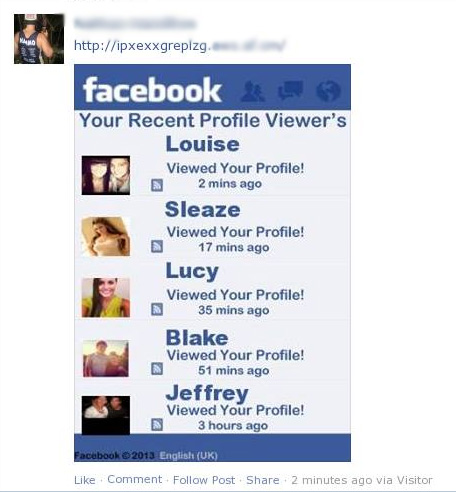 Picture from facecrooks.com
Picture from facecrooks.com
Then there are applications that can improve the performance of your computer. We offer you Avira System Speedup. This program can defragment your hard drive or delete useless folders and registry entries. It works perfectly well and WILL speed up your PC – to some degree. But there is just no application that will perform wonders on your PC. If it is 8 years old and slow, it will just never feel like a newer machine with more RAM and a better CPU despite your efforts and you paying €50 to improve it with a random program that promises you just that. Those scam apps, apart from not fixing your computer, also create errors or problems that didn’t exist before, in order to make you pay even more money for fixes you would not have needed in the first place.
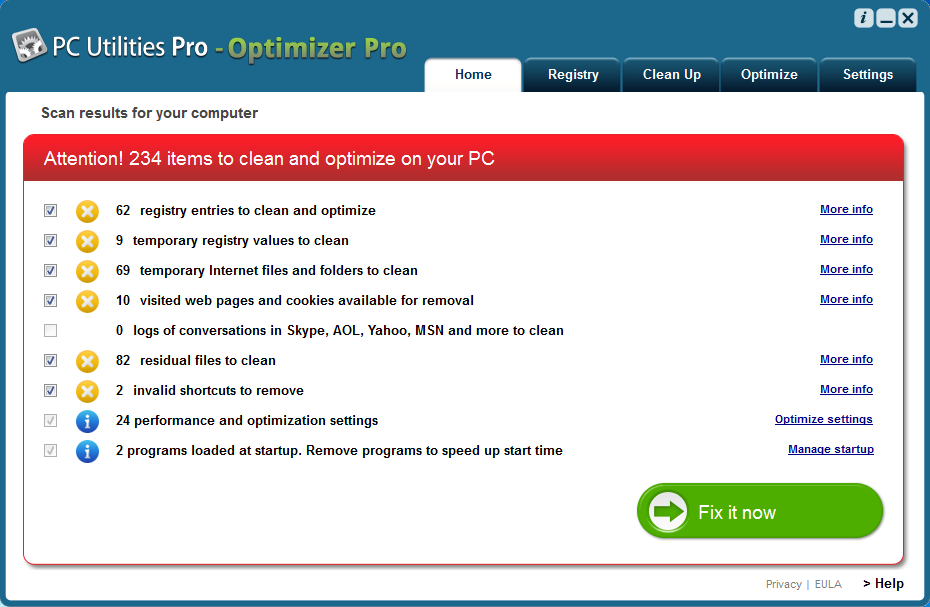
Optimizer Pro (another real world example) could be classified as scareware as well; it tells us that the computer needs to fix things that, in fact, are working correctly. It uses our fear to get us to pay for the product.
Scam is not getting old. It is also very present on our smartphones. Do you want an app that does things for free where others take money? It is possible, but be careful. With these applications you will usually be walking on thin ice.
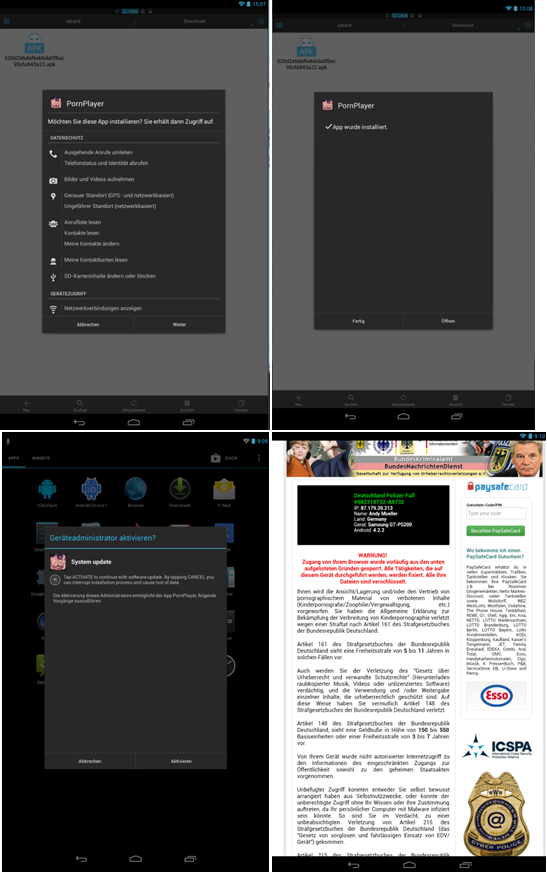
Porn app for Android for example is an app that allows users to watch porn videos for free. Just accept the conditions, give them permissions and run the app as soon as you can! Ooops! Did you think ransomware was only affecting your PC? Now you also have your phone blocked.
When you want to get an application, try to download it from the original source if possible. Also check different sites first, since lots of applications are actually for free.
Even on a well-known and trusted site like Amazon it is easy to find scam regarding original software. VLC is a popular video player which can be downloaded for free – but believe it or not, there are actually people trying to sell it to you to make some quick bucks.
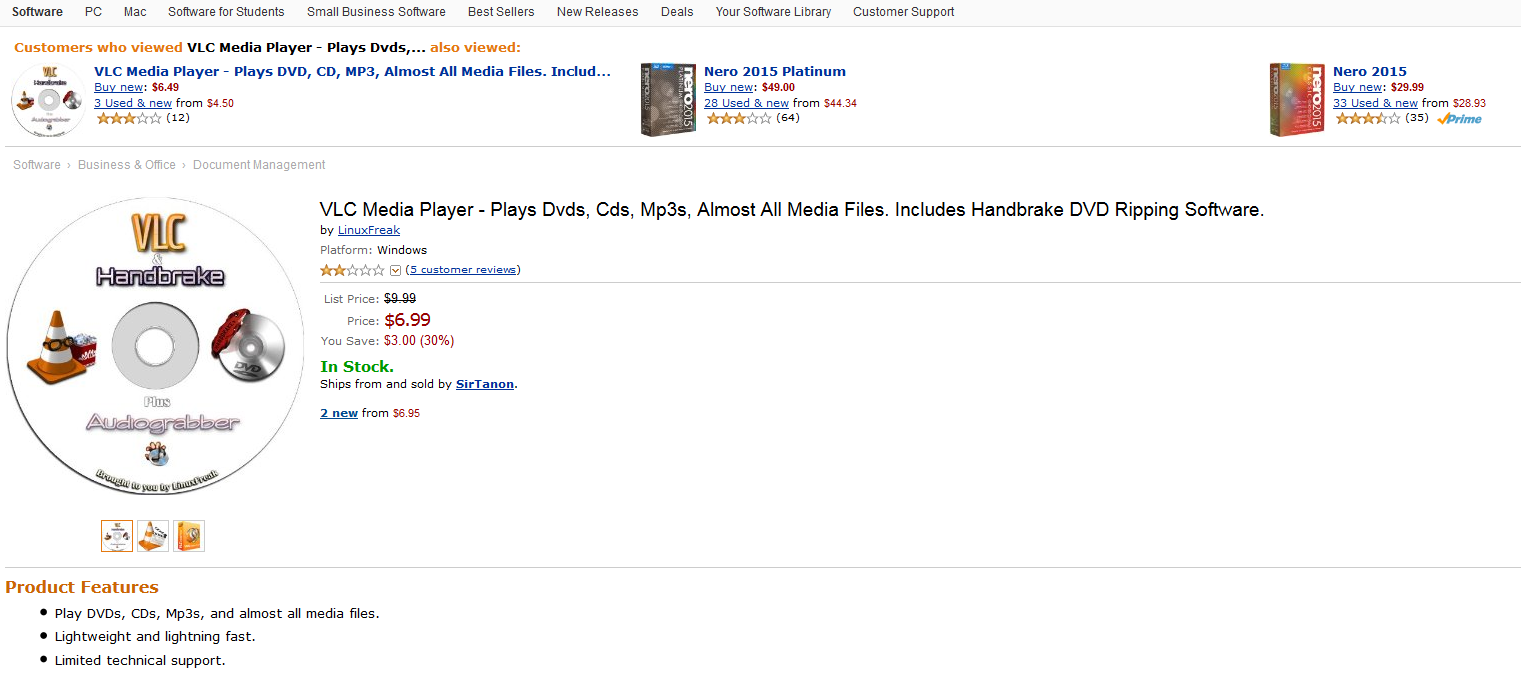
If you don’t trust the source, or if it looks just a tiny bit suspicious, turn around and run as fast as you can. Regarding scam applications: If you are looking for something specific, first check for another users opinions and more information, compare it with other products, and if you are still not sure, just leave it be.
In conclusion, Scamware is a waste of time and money and never does the things you were promised it was going to do. So don’t believe in these false promises of “eternal life potion”, “Ferraris for free” or “1 click super computer”.
Links:
The post Scamware or why you shouldn’t believe in miracles appeared first on Avira Blog.





