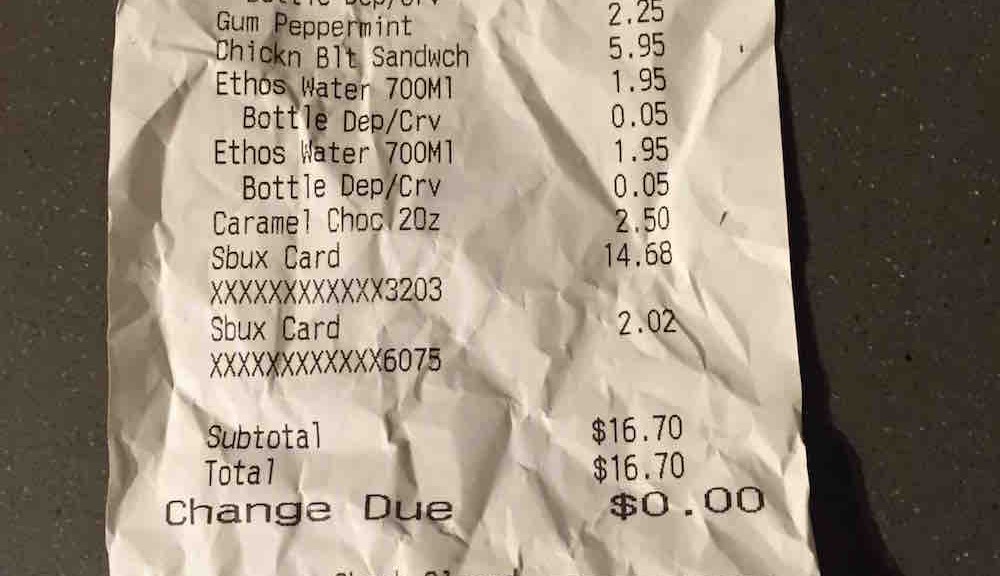Have you added up your spending on Starbucks coffee lately? If like me you grab a coffee five days a week at $3.65 then you have an annual bill of just under $1000. When I saw that a hacker had found a way to get unlimited free coffee it caught my interest, especially see that there have been a number of Starbucks related issues over the last 12 months.
Egor Homakov’s hack is more a logic mistake or bug than a hack, you can read his blog on how he did it in detail here. He started by purchasing three gift cards with a value of $5, the type anyone can purchase over the register.
Registering the cards online at starbucks.com then allows you to move money between cards and top them up as necessary. Homakov then started sending requests to move the cash between the cards using 2 different browsers at the same time. Doing this, he managed to break the logic and transfer the same $5 from card A to card B twice confusing the Starbucks system and gaining $5 in the process, thus making himself an extra $5.
This was possible thanks to what is known as a Race Condition in the way the transaction is processed. It takes place in two steps, the request and the acknowledgement.
In theory, this exploit could be run indefinitely to generate an unlimited amount of funds on a gift card.
Homakov did not do this though, after gaining the extra cash he tested the cards in a store purchasing coffee and a sandwich at a total of $16.70, proving he had more than he started with but limiting the loss to Starbucks to just $1.70.

Image courtesy of sakurity.com
As a responsible security expert he contacted Starbucks through their support system on March 23 and did not receive a response until April 29, and the bug has now been closed.
There seems to be a pattern of hacks and bugs at Starbucks, just a few weeks ago there was another issue with gift cards and the transfer of funds linked to bank account, see the analysis here. And last year there was an issue that passwords on the Starbucks app for iOS were being held in clear text, this one had a similar experience with Starbucks taking time to answer the disclosure from the expert, see the article here.
Starbucks mentioned the word ‘fraud’ when talking with Homakov rather than understanding that a responsible expert may have just saved them millions of pounds and saying thank you.
Personally I think he should be rewarded with at least a years free coffee, at $1000 it would seem a small price to pay.
You can follow me on Twitter @TonyatAVG
![]()
![]()