8 empowered woman in the computing world to celebrate International Women’s Day
Often seen as a male-dominated industry, women have played an important part in driving developments in the computer industry. As we celebrate International Women’s Day, these eight women have blazed a trail in IT, setting an example to us all.
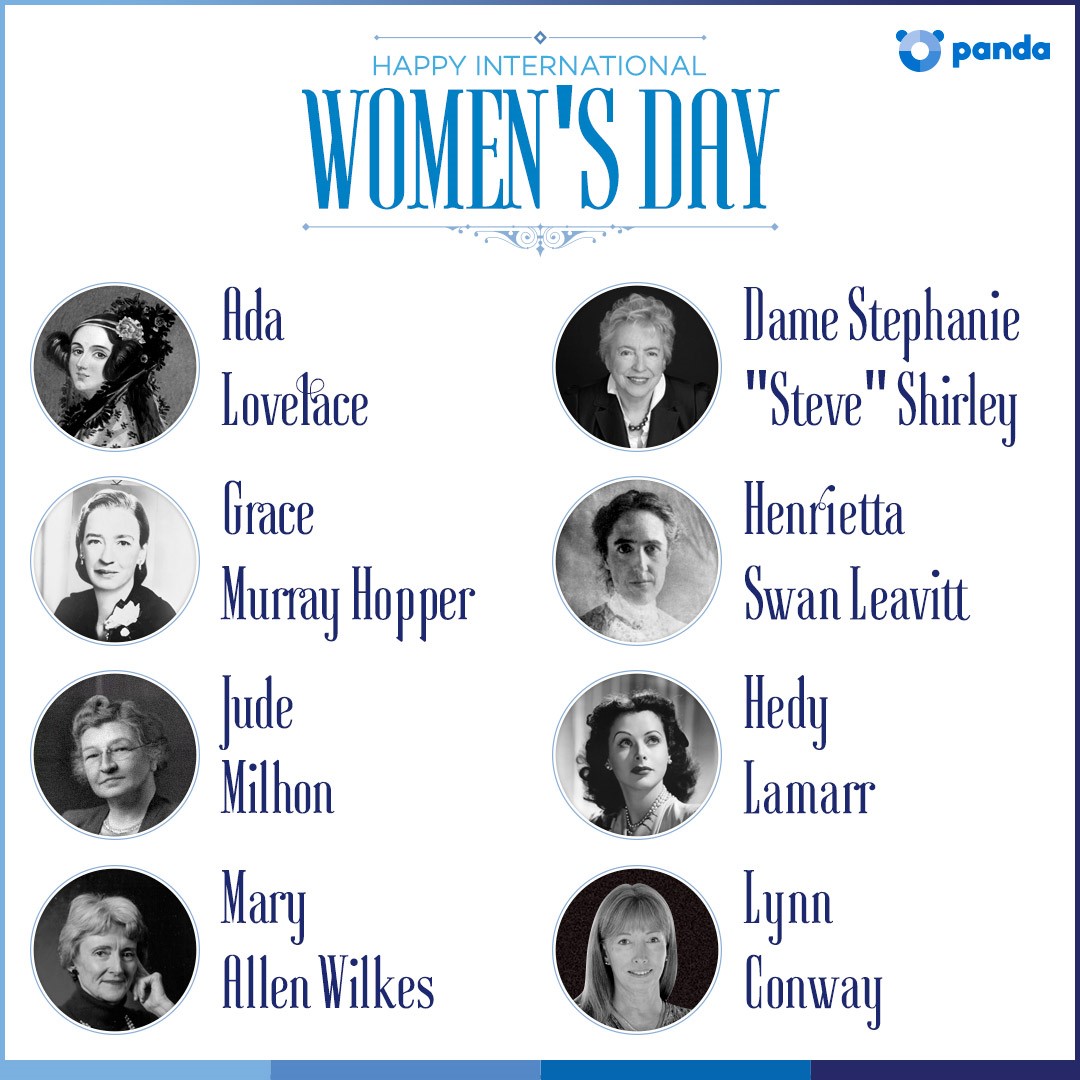 Ada Lovelace
Ada Lovelace
Despite being the daughter of the well-known bohemian hell-raiser George Byron, Ada Lovelace’s own life was incredibly successful, albeit slightly less “colourful”. Encouraged to study maths and logic by her mother, Ada’s studies soon brought her into contact with Charles Babbage, ‘the father of computers’.
As part of her work with Babbage, Ada created what is believed to be the first ever computer program – an algorithm to be run by Babbage’s legendary Analytical Engine.
Grace Murray Hopper
As well as being a Rear Admiral in the United States Navy, Grace was one of the first programmers of the Harvard Mark I computer. Her work led to the creation of the first compiler – a tool used to change computer code into a fully-functioning application.
Grace was also instrumental in creating COBOL, one of the first programming languages, and one that is still in use today.
Henrietta Swan Leavitt
During study for a graduate degree, Henrietta began working at the Harvard College Observatory. Her job – as a human computer was to help grade photographs taken through the observatory’s telescope, and to perform complex mathematical calculations.
Henrietta’s work paved the way for the techniques used by astronomers today to calculate the distance between Earth and distant galaxies.
Hedy Lamarr
Best known as a Hollywood actress, Hedy Lamarr was also an accomplished inventor in between roles. During World War II, Hedy helped to create a jam-proof radio guidance system to be used with torpedoes.
Although this signal-hopping technology was deployed by the US Navy until the 1960s (where it proved to be particularly effective), it is still in use today. The same basic principles are also used in modern WiFi and Bluetooth radio technologies – like those that make your smartphone and tablet work wirelessly.
Dame Stephanie “Steve” Shirley
After leaving school, Stephanie went to work for the Post Office Research Station where she helped build computers from scratch. She also learned to program machine code – the very low level language used by computer parts to work properly.
In 1962, Stephanie founded Freelance Programmers, a software company with the intention of helping women get into IT – just 1% of her programmers were male. The team worked on a broad range of projects, including the black box recorder for the supersonic jetliner, Concorde.
Jude Milhon
Having taught herself to program computers, Jude’s first job was in the IT department of a US food manufacturer. She also helped to create the Berkley Software Distribution (BSD) operating system which is still in use today.
Jude was also a committed social activist and hacker, going by the name of “St Jude”. Coining the term “cypherpunks”, St Jude helped to promote the idea of using cryptography to protect personal information as a route to social and political change.
Mary Allen Wilkes
Despite majoring in philosophy and theology, Mary became a computer programmer at the Massachusetts University of Technology. Initially she was programming IBM systems as part of a speech recognition project.
Later Mary was moved to a team working on LINC, widely believed to be the world’s first “personal computer”. As far back as 1964, Mary was using the LINC computer at home to refine the system’s design.
Lynn Conway
After a very successful period at university, Lynn was recruited by IBM to work on a project designing an advanced supercomputer. Known as the Advanced Computing Systems (ACS) project, the resulting computer is believed to have been an example of the first superscalar design.
Later Lynn worked for major organisations including DARPA and Xerox, and MIT as an associate professor.
Examples to us all
Although these women may serve as examples to women considering a career in IT, their experiences and achievements are actually a lesson for all young people – regardless of gender.
The post International Women’s Day: 8 empowered woman in the computing world appeared first on Panda Security Mediacenter.
![]()