Category Archives: Antivirus Vendors
Antivirus Vendors
Counter surveillance tech – can gadgets spy-proof your life?
Over the past few years, counter surveillance gadgets which might have been the preserve of secretive government departments a decade ago have suddenly hit mainstream shops – from Mission Impossible-stlye self-destructing drives to some rather eerie counter-surveillance masks.
The post Counter surveillance tech – can gadgets spy-proof your life? appeared first on We Live Security.
![]()
The 3 most common questions about Clickjacking
This procedure is called Clickjacking and it is one of the most used techniques by hackers trying to gain access over your accounts or obtain private data.
How does clickjacking work?
It all starts with a user receiving an e-mail that mimics perfectly the messages usually sent by a company he is a client of. This e-mail would have to include a fake link for the user to reset the password used on the real company website when he would actually be providing the hackers access to his account. Knowing both the e-mail address and the associated password, they can now extract all the personal information they need and take over the specific account.
Practically, once the customer clicks on the button in the e-mail, he will end up on the hacker’s website. There, the latter will attempt to make an http/https call to the real company’s API’s/forms to reset the user’s password/e-mail address and take over his account.
When does clickjacking this work?
In order for clickjacking to work, the user had to be previously logged in the account that he owns on the real company website. Also, if no CSRF protection is activated on the company’s end and official website/API accepts calls from other domains with no filtering, chances are that the operation becomes successful.
Clickjacking can also work locally (on your machine) when you manually create an iFrame and inject the company’s forms. This however doesn’t impact the end user/ customer because it only takes place on the hacker’s computer.
How can I be sure that I am not a victim of clickjacking?
We recommend all companies to implement the 2 following methods to keep safe from this kind of attacks:
- Do not accept requests from other websites (domains). If possible, use the x-frame-options header and set it to SAMEORIGIN so that other domains cannot access the methods/ API on your company’s end (this header should not be accessible / usable in all browsers).
- Implement CSRF token validation making sure that for each form display page there is an uniquely assigned CSRF token to the customer. The CSRF token can only be obtained by logging in as the real customer.
The post The 3 most common questions about Clickjacking appeared first on Avira Blog.
Top 5 Scariest Zombie Botnets
An army of the undead, wreaking havoc on the Internet – it’s a nightmare scenario that has played out many times as the population of humans online has exploded. Some zombie plagues have been particularly troubling, and we will take a look at the worst of the worst.
The post Top 5 Scariest Zombie Botnets appeared first on We Live Security.
![]()
Shopping safely with Amazon
Online shopping can be risky even if you use world renowned websites such as Amazon. Take a look at our top tips for how to shop safely with the online store.
The post Shopping safely with Amazon appeared first on We Live Security.
![]()
How to speed up your computer
A slow computer can be both frustrating and time consuming, so we’ve provided a few basic tips to help give your computer its speed back.
The post How to speed up your computer appeared first on We Live Security.
![]()
Yahoo, Match and AOL hit by ransomware
Cybercriminals taking advantage of a ‘malvertising’ attack on big name sites including Yahoo!, Match.com and AOL were making in the region of $25,000 per day, according to Forbes.
The post Yahoo, Match and AOL hit by ransomware appeared first on We Live Security.
![]()
How to boost security on your Facebook account with two-step verification

No doubt you’ve heard about two-step verification used on various social networks.
Having this option enabled lets you increase security on your account and helps prevent unauthorized and potentially malicious access.
In the case of Facebook, the process is simple, and all you need is your cell phone handy to confirm access from a new device. In Facebook, a new device is one that you haven’t used previously to connect to the platform.
This way, what you have to do is approve logins to prevent others from accessing your account.
Here we explain step-by-step how to enable login approvals.
How to boost security on your Facebook account with two-step verification
In your Facebook account, go to Settings.
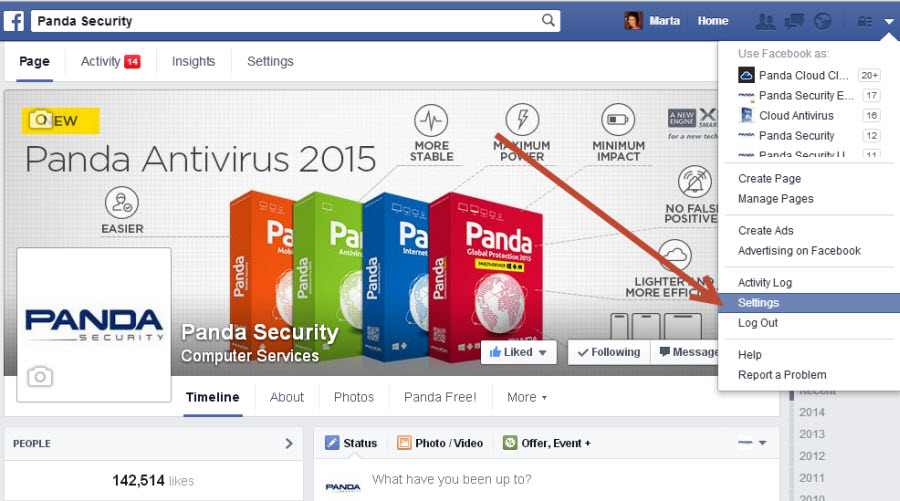
Go into Account Settings and select Security. There you will see “Login Approvals”.
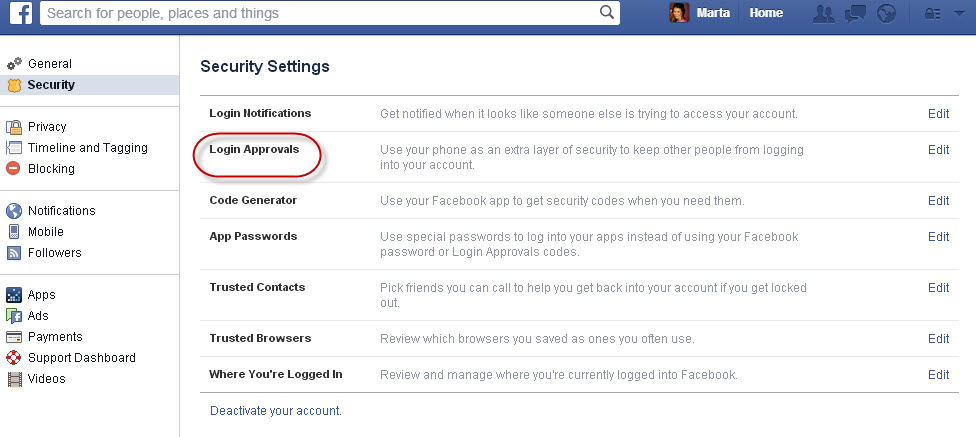
From there click “Require a security code to access my account from unknown browsers”.
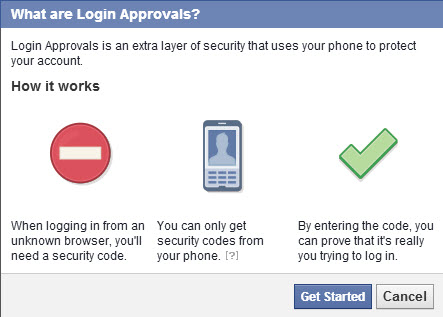
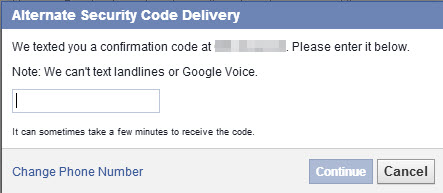
When you enter the code that they send to your phone, you will have to enter your Facebook account password.
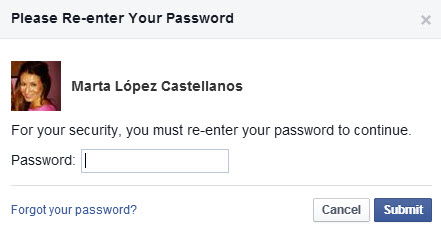
Now you have enabled login approvals.
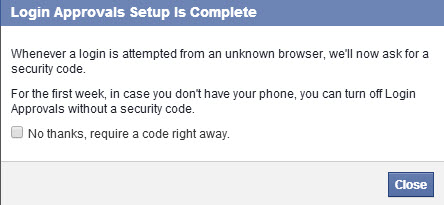
Facebook also gives you the option to print security codes in case at some time you don’t have your phone handy. It’s easy, right?
The post How to boost security on your Facebook account with two-step verification appeared first on MediaCenter Panda Security.
Spam in September: Financial Phishing Accounts for Highest Percent of Detections
Avira HR Team @Top Employers Job Fair
Software engineering: from everyday challenges to real world solutions
The second day of event, our colleague Radu Calin (Web Backend Software Engineer) gave a presentation about Distributed computing during the workshop we organized. We were happy to learn that this session raised unexpected interest among the candidates attending the fair: more than 120 people had registered for what we designed as a workshop with 40 participants.
Radu talked about how we managed to build a product that makes life easier for millions of users worldwide, all the while solving some of the most difficult problems of the cloud era. He went more in-depth, showing the attendees how the Avira team managed to create a scalable distributed system with pure fun and passionate engineering. Towards the end, he did not forget to give some details about what makes “life at Avira†so special and the audience was really impressed.
All in all, the event was a great success for our HR team:Â 2 days, over 500 applicants, almost 1400 flyers taken home by the candidates, 1 workshop with 58 participants, and over 5000 participants to attend the fair in search of their next Top Employers.
If you missed the event but you also want to†join the battleâ€, you can also check the current job opportunities and apply directly on our career page. A virtual job fair is also organized to follow up with Top Employers attendees, check it out here.
The post Avira HR Team @Top Employers Job Fair appeared first on Avira Blog.
