- Panda Security’s new consumer product line is now available. New solutions are lighter, safer and easier to use than ever before, and are based on the new XMT Smart Engineering architecture, a new engine for a new technological era
- Â Panda Global Protection 2015, Panda Internet Security 2015, Panda Antivirus Pro 2015, Panda Mobile Security and Panda Gold Protection leverage the power of cloud computing to combat maware threats
Madrid, August 13, 2014
Panda Security, The Cloud Security Company, today announced the launch of its new line of consumer solutions. Panda Global Protection 2015, Panda Internet Security 2015, Panda Antivirus Pro 2015, Panda Mobile Security 2.0 and Panda Gold Protection are the five products included in the security company’s 2015 consumer line which this year boasts the new XMT Smart Engineering engine as its main new feature.
The results of the latest comparative tests conducted by independent laboratories such as AV-Comparatives, AV-TEST and Virus Bulletin, where Panda Security achieved the best scores in detection, protection and resource use, showcase the excellent capabilities of the new XMT engine. With XMT, different technologies interact with each other to achieve new levels of efficiency and greater detection and disinfection power to eradicate all threats.
“In a context in which 160,000 new malware samples are created every day, as reported by PandaLabs’ Q2 report, we are very much aware that we have to provide users with the best protection. And the best thing is that the engine with which we’re achieving the highest detection ratios in the industry’s leading tests is the basis of all our endpoint protection products,†said Ãlvaro Elorriaga, Global Retail Director at Panda Security. “Our aim is to continue integrating technologies in the platform to stay in pole position when it comes to detection, and provide our users with maximum protection and minimum impact on their systemsâ€.
Minimum impact on performance
Designed to provide complete protection with minimal performance impact, Panda Security’s new 2015 Consumer solutions harness the power of cloud computing to combat the myriad security threats users face today: viruses, hackers, online fraud, identity theft and all other known and unknown threats.

“The new 2015 Consumer line is based on four pillars that have allowed us to further improve our security solutions, adjusting them to our customers’ needs: protection, lightness, flexibility and stabilityâ€, explained Hervé Lambert, Retail Product Marketing Manager at Panda Security. Â
Cross-Platform Protection
In addition to the new XMT engine, one of the most noteworthy features of Panda Security’s new 2015 solutions is the cross-platform protection provided by Panda Global Protection 2015 for Mac environments and even mobile devices. Furthermore, advanced users will find an additional layer of protection with Data Shield, a new module to protect user data against malware such as ransomware that tries to access sensitive information with malicious purposes (theft, deletion and encryption).
Additionally, the 2015 versions of Panda Internet Security and Panda Antivirus Pro include improved protection capabilities against viruses, hackers and Wi-Fi intrusions thanks to a Wi-Fi monitor that provides full visibility into all the devices connected to the wireless network. Along with these features, Panda Internet Security 2015 helps protect users’ children, identity and data with parental control, application control and online backup functionalities. “Despite Panda Antivirus Pro is the most basic solution in the entire line –it protects Windows environments only–, the truth is that it is much more than a simple antivirus. Besides providing fast and intuitive protection, it also includes other features such as a firewall, virtual keyboard, rescue kit and multimedia optionsâ€, explained Hervé Lambert.
New Panda Mobile Security Now Available on Google Play
Additionally, the new Panda Mobile Security 2.0 is now available on Google Play. This solution, designed to protect Android devices, includes features such as geolocation and anti-theft to remotely locate, lock and wipe lost or stolen devices. The new version is much more intuitive and user-friendly than before thanks to a brand new look and feel.
Panda Gold Protection

Panda Security’s 2015 Consumer product line also includes Panda Gold Protection, a complete solution designed to protect users’ data regardless of the device they are using: PC, Mac, and Android smartphones, tablets and Smart TVs. Panda Gold Protection is the only product in the entire 2015 line that features Panda Cloud Drive, an online backup and sync service with 20 GB of free space that allows users to store files securely in the cloud and access them from any computer, mobile device or Web browser at any time.
Users who want to take a free trial of Panda Security’s new 2015 solutions can go to http://www.pandasecurity.com/homeusers/
Also, users who want to buy Panda Security’s products can do so online on the company’s website or at the usual points of sale (retailers, dealers, shopping malls, etc).
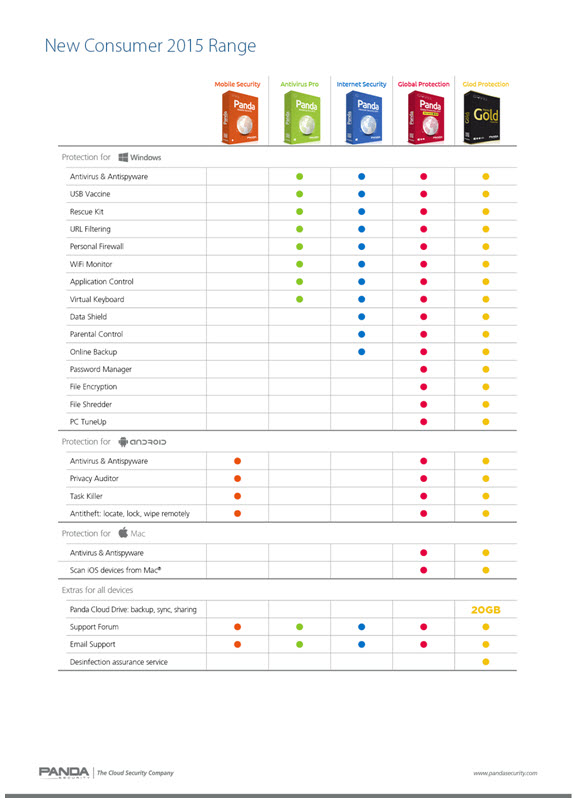
Main features of Panda Security’s 2015 Consumer solutions
About Panda Security
Founded in 1990, Panda Security is the world’s leading provider of cloud-based security solutions, with products available in more than 14 languages and millions of users located in 195 countries around the world. Panda Security was the first IT security company to harness the power of cloud computing with its Collective Intelligence technology. This innovative security model can automatically analyze and classify thousands of new malware samples every day, guaranteeing corporate customers and home users the most effective protection against Internet threats with minimum impact on system performance. Panda Security has 80 offices throughout the globe with US headquarters in Florida and European headquarters in Spain
Panda Security collaborates with The Stella Project, a program aimed at promoting the incorporation into the community and workplace of people with Down syndrome and other intellectual disabilities, as part of its Corporate Social Responsibility policy.
For more information, please visit www.pandasecurity.com/
Â
The post Panda Security launches new 2015 Consumer Line with XMT Smart Engineering Engine #Panda2015 appeared first on MediaCenter Panda Security.
![]()