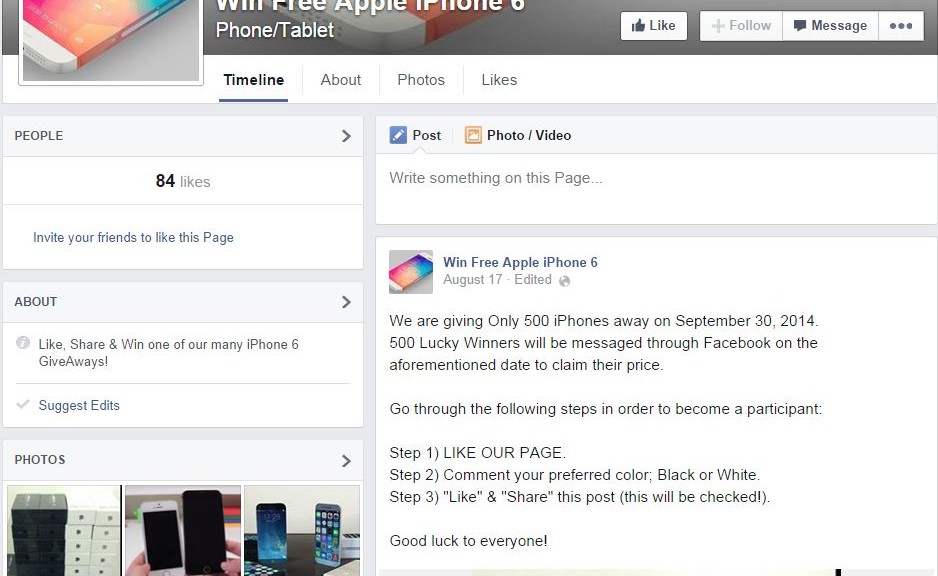
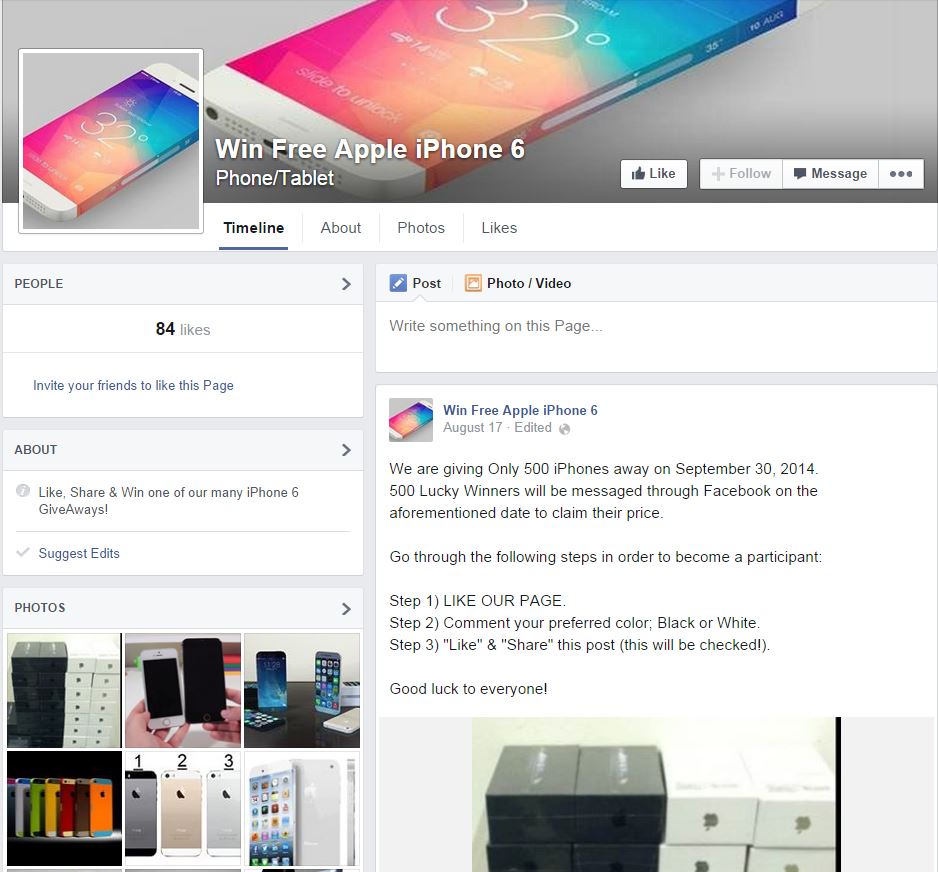
Facebook scams tend to crop up in the run-up to a big Apple launch with around the same regularity as big Apple launches themselves. This week’s iPhone 6 launch is no exception, with Help Net Security noting that a Facebook page ‘offering’ free iPhone 6 units is, as usual, a total fraud.
This time, the scam promises a free iPhone 6 as soon as “three easy steps†are completed, which, as usual, involve a survey, which allows you to download a “participation application.â€
When a victim completes the free iPhone 6 survey, all their friends are spammed with the fake promotion, Hoax Slayer reveals, but the three “easy†steps are anything but.
Each time someone completes a survey, the page claims there is an error, and they are directed to a further survey, according to Help Net. As always, the “free iPhone 6†never materializes.
Free iPhone 6: Nope, it’s a scam
“Some of the available surveys want you to provide your mobile phone number, ostensibly to go in the draw for extra prizes or offers. But, by submitting your number, you will actually be subscribing to a very expensive text messaging ‘service’ that will charge you several dollars every time they send you a message,†Hoax Slayer says.
“Alternatively, you may be asked to provide your name, address, and phone details, again, to supposedly enter you into a prize draw. But, fine print on the page will state that your details will be shared with third-party marketers. Thus, after submitting your details, you will likely be inundated with annoying phone calls, emails, and junk mail.â€
“Meanwhile, the scammer who created the fake promotion will earn a commission. But, no matter how many surveys you complete, you will still not get to download your ‘application’.â€
The site cautions against clicking on any link this week which offers a free iPhone 6, as this sort of big product launch is a prime target for cybercriminals, and any link is potentially suspect.
Something for free?
Mark James, ESET security specialist, says, “We all like the idea of something for free, that’s the approach these type of scams use. Deep down we know it’s not going to happen, but a lot of people will still click the like button or share that simple post in the hope it’s going to arrive.â€
“We have seen these types of scams for years but they are still as effective today as they were when started, once we like or share the page we do all the marketing and advertising for the scammers thus providing a very valuable and potential dangerous page to initiate future scams or attacks.â€
“I still encourage people to use the “front door†policy, i.e treat it like your front door: ‘When was the last time someone banged on your front door to offer you an iPhone 5 or 6 just for filling out a survey or a £10/£50 supermarket voucher for free?’ It just does not happen.â€
The post Free iPhone 6 Facebook scam does the rounds, right on time appeared first on We Live Security.

![]()