Category Archives: Antivirus Vendors
Antivirus Vendors
VPN for beginners
Virtual private networks use a public network, usually the internet, to connect remote users together. Here, we take a closer looks at VPNS and help you choose the right one for your needs.Â
The post VPN for beginners appeared first on We Live Security.
![]()
Scareware: How to tell if a threat isn’t real
Scareware is a strategy that Cybercriminals use to trick users into buying and downloading unnecessary and potentially dangerous software. Listen to our top tips to identify whether a threat is real or not.
The post Scareware: How to tell if a threat isn’t real appeared first on We Live Security.
![]()
Bank security – Barclays to offer vein-scanner to big accounts
Barclays Bank is to allow remote log-ons using a hi-tech vein-scanning biometric bank security system for large corporate accounts, according to Engineering and Technology magazine. The bank security system, using Hitachi’s VeinHD scanner, will be available to corporate customers from next year.
The bank security scanner uses infrared light to capture an image of the veins of the customer’s index finger, and compares this against a pattern stored on a smart card (similar to the cards used to store details for Chip and PIN transactions).
Biometric finger vein scanning technology for authenticating online banking transactions will be available to Barclays’ corporate customers from next year, according to Reuters.
Bank security: Scanner ‘requires live finger’
The Telegraph reports that the technology will be available to Barclays Corporate Banking clients from next year, and says that the bank emphasized that the biometric scanner was one of the most secure on the market.
The paper says that a bank spokesperson said that the finger to be scanned, “must be attached to a live human body in order for the veins in the finger to be authenticated”.
Engineering and Technology points out that a finger vein pattern is nearly impossible to fake, unlike other common biometric identifiers, where fakes are produced with relative ease.
Hackers have “fooled†the scanners in both Samsung’s Galaxy S5 and iPhone 5S with fake fingerprints made from latex.
‘About the highest security you can get’
“If it had any known issues we would never ask our clients to go down that path. The security in finger vein scanning is about the highest you can get and that’s why we feel so confident in it,â€said Ashok Vaswani, chief executive of Barclays personal and corporate banking.
“Biometrics is the way to go in the future. We have no doubt about that, we are committed to it,” Ashwani.told Reuters in an interview. He said that fraudsters were constantly seeking new technologies to steal from the bank.
“You can’t let these guys create a breach in the dam. You’ve got to constantly stay ahead of the game.â€
Barclays said it expected strong take-up for the technology from its 30,000 corporate clients.
Reuters describes the scanner as “looking like a mini Star Wars stormtroooper helmetâ€, and that the pattern is matched with one stored on a smart card, signaling the bank to send an encrypted authorization code to the PC.
TechCrunch points out that vein recognition technology is already used to secure high-value banking transactions in countries such as Japan, but only as a secondary “layer†of security where other methods of authentication are also used.
At 15 payment machines dotted around the Swedish city of Lund, people can buy items using a similar vein scanner, and without a debit or credit card.
Engineering graduate Frederik Leifland says, “I got the idea when I was in line at the supermarket and I saw how complex a process paying is. It takes a lot of time, so I thought there must be an easier and quicker way to pay and that was the start of Quixter.â€
In a new interview with science website Humans Invent, Leifland explains how he hopes that his start-up may lead to payments without any authentication device. The pattern of veins in a human hand is unique – Leifland’s system uses infrared scans to identify the unique pattern in a finger.
BioMetrics sales site FindBiometrics says that the technology is relatively new, and currently used in high security institutions, saying, “Vein recognition is a fairly recent technological advance in the field of biometrics. It is used in hospitals, law enforcement, military facilities and other applications that require very high levels of security.â€
The post Bank security – Barclays to offer vein-scanner to big accounts appeared first on We Live Security.
![]()
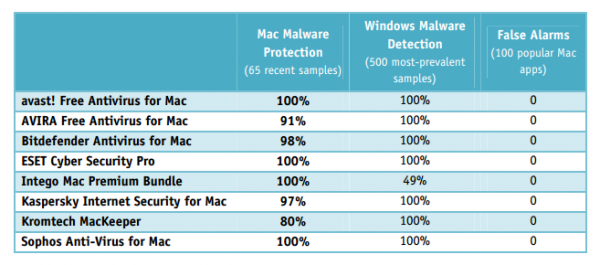
Avast! Free Antivirus for Mac outperformed competitor products in the independent tests!
Compared to Windows users, Mac users have been relatively unaffected by malware attacks. Cybercrooks, however, are just as aware as antivirus vendors are about Mac vulnerabilities. With the growing number of Mac users, cybercrooks see more potential for malicious activities, especially as Mac users tend to have a false sense of security and not usesecurity software. You only have to read this blog to learn that cybercrooks are adapting Windows malware to target their Mac counterparts.
We should never underestimate Mac security. Avast! Free Antivirus for Mac offers free protection against the latest malware designed to attack Mac operating systems. As all other Avast security products, the Mac version participates in frequent, independent tests. Recently avast! Free Antivirus for Mac was not only certified by AV-TEST but it also received 100% in the latest Mac Security Test & Review conducted by AV-Comparatives in July-August.
We are proud to share the results with you!
More about AVAST’s performance in both tests.
AV-TEST GmbH is a leading worldwide operating service provider for IT security testing services. The latest test was focused on Mac OS X security products and took place in July and August 2014. Eighteen AV products participated, and the tested platform was MacOSX 10.9.4. The results can be found here.
The new version 9 of avast! Free Antivirus for Mac has easily outperformed competitor products. The security software offered high malware detection rates, does not decrease Mac performance and did not cause false positives in our tests. ~ Andreas Marx, CEO of AV-TEST
Below is a short summary of AVAST’s performance!
Q:Â Which product was tested?
A: avast! Free Antivirus for Mac
Q: Which version was tested?
A:Â ’9.0 (41877)
Q: How did avast perform in the detection on-demand test?
A: Â avast! Free Antivirus for Mac received a scored of nearly 97.5%
Q: How did avast perform in the on-access detection test?
A:  avast! Free Antivirus for Mac scored 100%
Q: How many false positives were recorded in the on-demand and on-access tests?
A: None; avast  didn’t make any mistakes and recognized all malware correctly!
AV-Comparatives is an independent not-for-profit organization offering systematic security tests of antivirus products for PC and Mac, as well as mobile security solutions. The test conducted in July and August 2014 reviewed the performance of eight security software for OS X 10.9 Mavericks.
We found Avast’s phishing and malware alerts to be very good. The pop-up messages make it clear that the threat has been blocked and provide useful information for advanced users, such as the URL or file path (…) avast! Free Antivirus for Mac identified 100% of samples in both Mac malware and Windows malware tests and has a largely very straightforward program interface, albeit with the odd quirk.  ~ AV-Comparatives said in its report
Below, find the overview of avast’s performance versus its competitors
Last but not least, a picture is worth a thousand words, and we believe your Mac is worth it! Download it here.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter, Google+ andInstagram. Business owners – check out our business products.
Hackers in Hollywood, and Beyond
Many celebrities got an unpleasant shock this past weekend. You may have heard that up to 100 celebrities – film stars, etc. – had nude photos hacked and leaked on renegade Web site 4chan.org. Many of the photos were apparently genuine.
Now that the FBI is investigating how these photos were hacked and posted, it’s an unfortunate reminder of the difficulties of maintaining our privacy in this digital age.
I won’t name the celebrities involved, but it’s safe to say it’s a huge invasion of privacy. Some experts are theorizing that the hacker or hackers exploited weaknesses in Apple’s iCloud platform. Apple is now investigating, according to reports and released this statement. Here’s an excerpt: “After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet. None of the cases we have investigated has resulted from any breach in any of Apple’s systems including iCloud or Find my iPhone. We are continuing to work with law enforcement to help identify the criminals involved.â€
As a major player in the data security business, we think that this is just a reminder to everyone that when data goes digital, there are security risks involved. It’s a hard lesson.
As British actress Emma Watson (who was not targeted in the hacking) wrote on Twitter: “Even worse than seeing women’s privacy violated on social media is reading the accompanying comments that show such a lack of empathy.â€
Protecting yourself
How to protect yourself, even when you’re not a celebrity? Here are some tips, which we’ve stressed before but can’t stress enough:
- Create difficult passwords. Besides the speculation that iCloud was the victim, it has been suggested the hacker or hackers exploited each of the 100+ accounts’ passwords. As I’ve mentioned before, don’t use your birthday, and create multiple passwords for multiple accounts!
- Consider switching off automatic Cloud photo sharing and backups/Photo Stream. This is a convenience tradeoff. To turn off automatic iCloud sharing, go into your Settings, then iCloud, then scroll down to photos and slide the option to Off.
- Use encryption. Here I will proudly put in a plug for our own mobile phone encryption software, which protects your data against intrusion by encrypting your documents. This is a must for anyone storing private personal or important business intelligence on their phones.
- Think about using a USB drive. If you want to share personal information or photos with a specific person, just use a USB.
As celebrities, Apple, and the FBI come to grips with this specific hacking instance, it’s important to realize everyone’s information is at stake these days – celebrity or not –
And an excellent reminder that we need to actively protect ours.
![]()
![]()
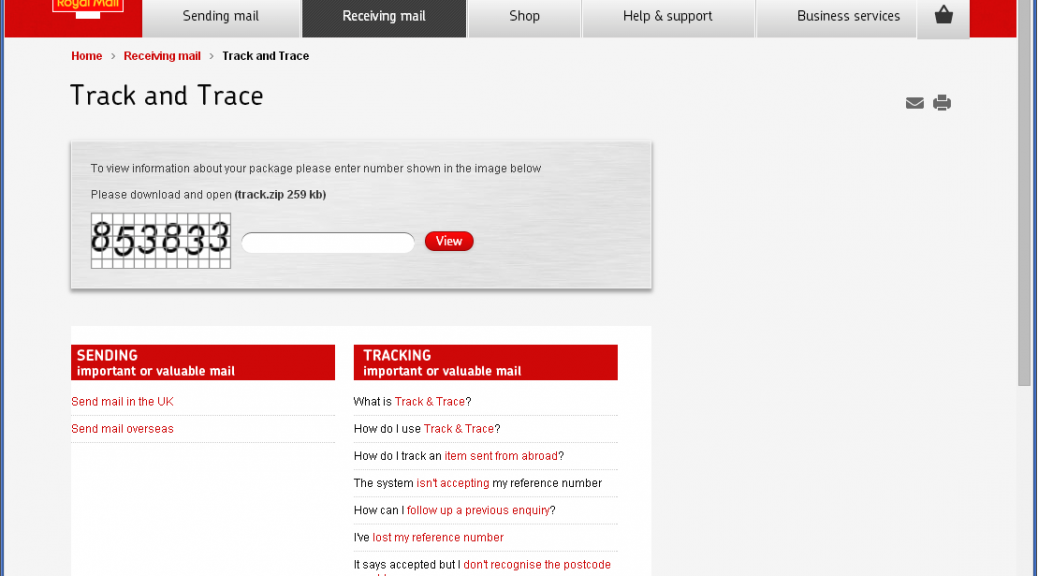
TorrentLocker now targets UK with Royal Mail phishing
Three weeks ago, iSIGHT Partners discovered a new Ransomware encrypting victims’ documents. They dubbed this new threat TorrentLocker. TorrentLocker propagates via spam messages containing a link to a phishing page where the user is asked to download and execute “package tracking informationâ€. In August, only Australians were targeted with fake Australian Post package-tracking page.
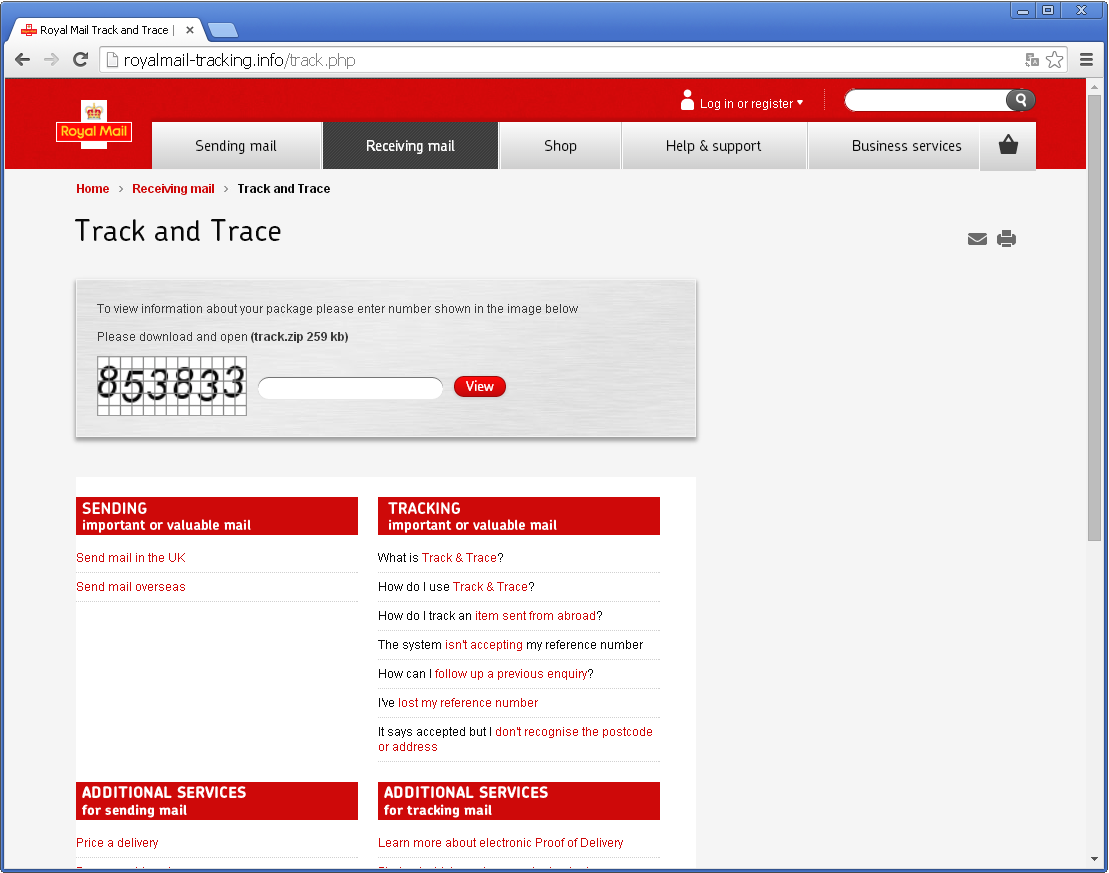
While tracking this new threat, ESET researchers found the malicious gang is targeting new victims. Internet users from the United Kingdom should be aware that fake Royal Mail package-tracking pages are online and distributing TorrentLocker.
The scheme is the same: you type a captcha then click to download a zip file containing the executable payload. It is interesting to note that the fake Royal Mail page will only show if the visitor is from the UK. Filtering seems to be based on the IP address of the request. If the request does not come from a UK IP address, the victim will be redirected to google.com. Three new domains are hosting the fake Royal Mail page:
- royalmail-tracking.info
- royalmail-tracking.biz
- royalmail-tracking.org
![]() royalmail-tracking.info registration information
royalmail-tracking.info registration information
As you can see, registration date for these domains is September 2nd so this campaign started very recently.
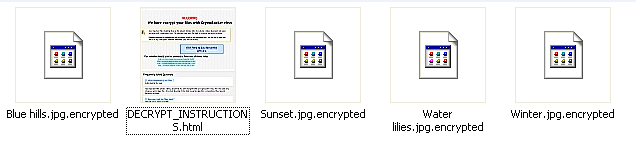 Encrypted files in users’ pictures
Encrypted files in users’ pictures
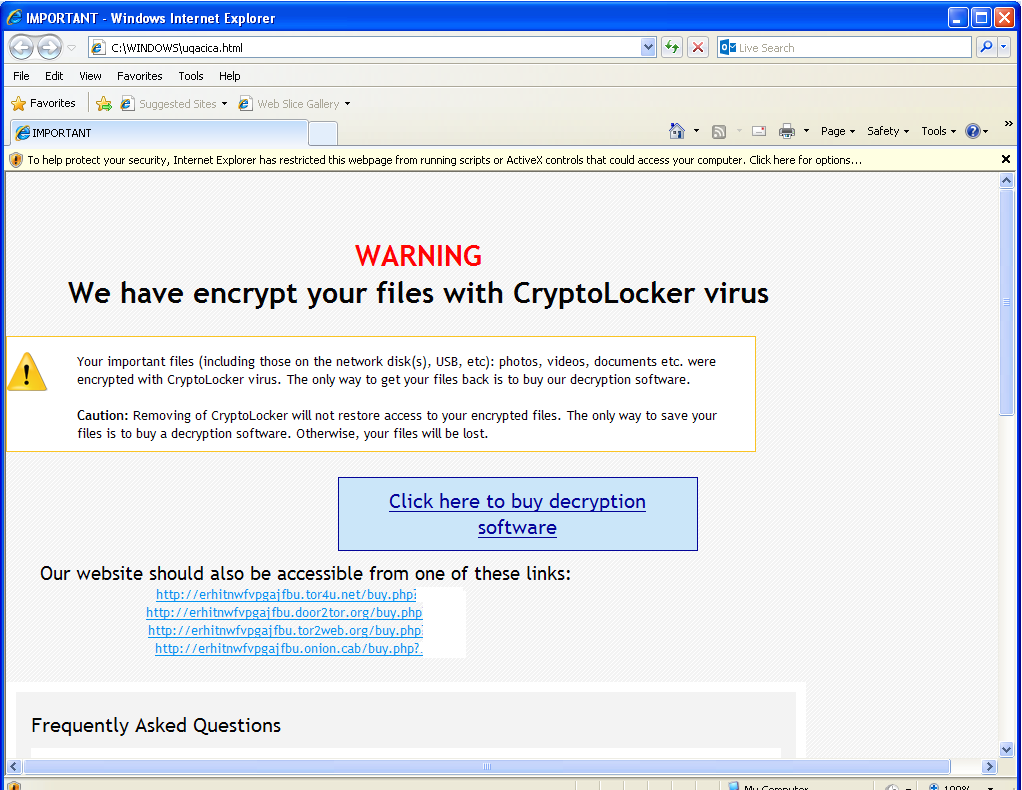 Warning is shown upon execution of the malware
Warning is shown upon execution of the malware
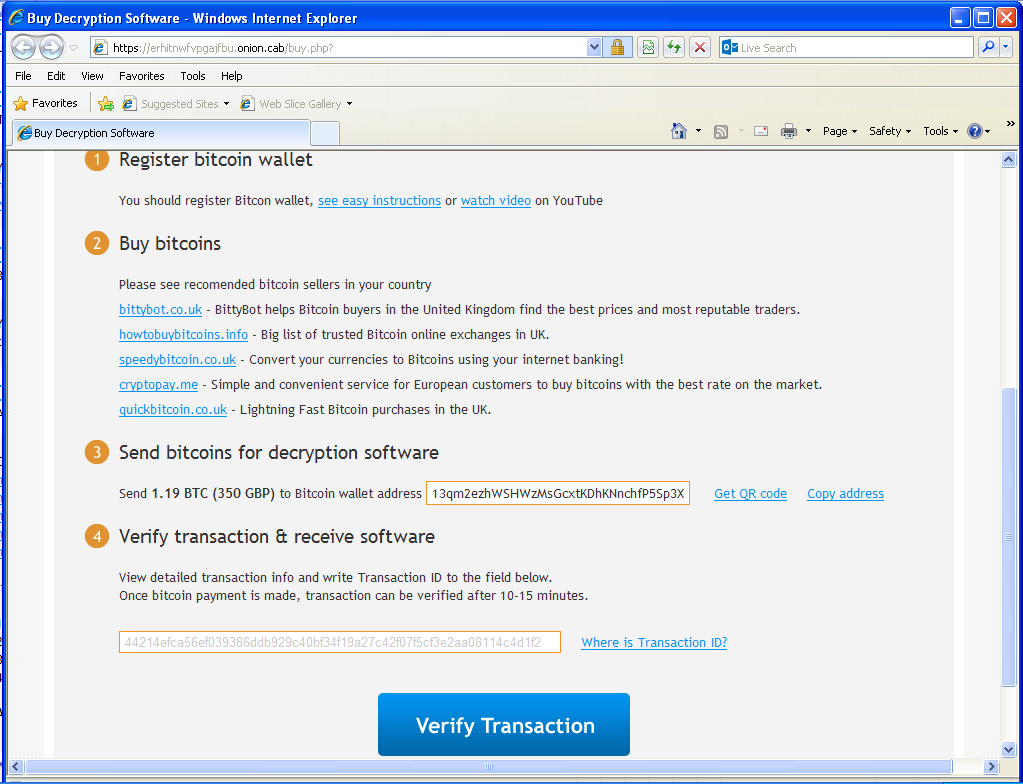
Once installed, victims’ documents are encrypted and they are being asked for a ransom of 350 GBP if paid within 72 hours or 700 GPB otherwise. Payment is done via Bitcoin transaction (1.19 BTC or 2.38 BTC). To hide their infrastructure, the web server is hosted on a .onion host on the Tor network.
To make it is easy for victims to access the web page, TorrentLocker is giving links to Tor2Web nodes so they don’t have to install additional software to reach the .onion website. Interestingly, door2tor.org, the domain name of one of the suggested Tor2Web node, was registered only 2 weeks ago. Perhaps its purpose is only to allow TorrrentLocker’s victims to contact the server selling the decryption software.
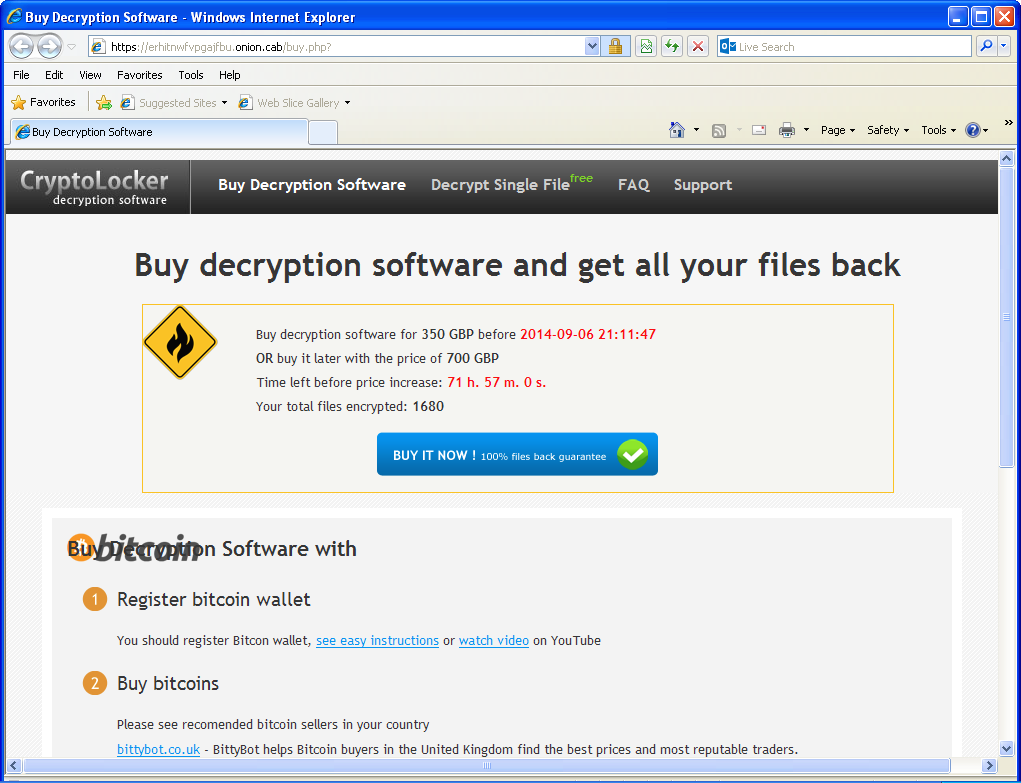 “Decryption software” sold on the Tor network
“Decryption software” sold on the Tor network
This threat caries the TorrentLocker name because it use the “Bit Torrent Application†Windows registry key to store its settings. It is unrelated to the BitTorrent protocol.
The Bitcoin trail
As discovered by iSIGHT Partners, the Australian variant they analyzed asked for Bitcoins to be sent to 15aBFwoT5epvRK69Zyq7Z7HMPS7kvBN8Fg. In our case, the Bitcoin address changed to 13qm2ezhWSHWzMsGcxtKDhKNnchfP5Sp3X. If you look at the transactions on both wallets, the Bitcoins are then transferred to 17gH1u6VJwhVD9cWR59jfeinLMzag2GZ43.
Since March 2014, this Bitcoin wallet has transferred over 82 272 BTC. With 1 BTC currently valued at US$480, the total transactions are roughly equal to 40 millions US$. This wallet has been associated with other scams in the past, including wallet stealing and selling fake mining hardware. We do not know if this account is owner by the TorrentLocker gang or it is some kind of exchange service used by different groups.
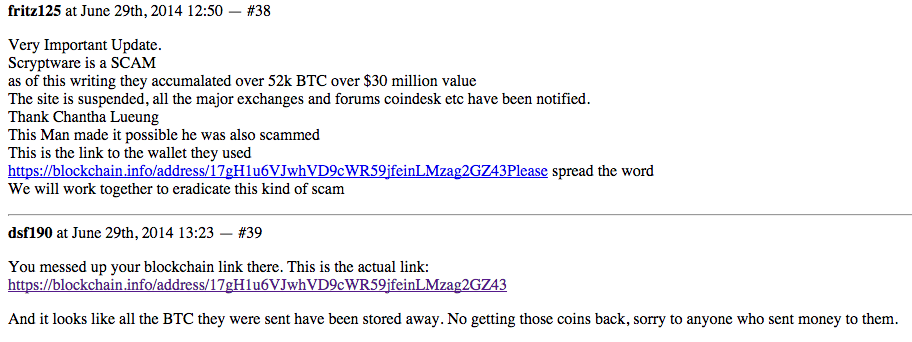 Screenshot of a discussion on Hashtalk (now offline, retrieved from Google Cache)
Screenshot of a discussion on Hashtalk (now offline, retrieved from Google Cache)
ESET products detect this threat as Win32/Filecoder.NCC or Win32/Injector.
SHA-1 hashes
- 491C8276667074B502BD98B98C74E4515A32189B (exe)
- 46A2426D7E062E76D49707B58A5DF28547CBC0F4 (zip)
- 7C62651C5F4CB1C780C8E9C4692F3BF24208A61E (exe)
References
The post TorrentLocker now targets UK with Royal Mail phishing appeared first on We Live Security.
![]()
Now your LinkedIn account can be better protected than ever before
Let’s be honest. LinkedIn doesn’t have the most spotless record when it comes to security and privacy.
In the past, LinkedIn has been hacked (Who can forget when 6.5 million stolen LinkedIn passwords were found on a Russian web server?)
Or maybe you recall hearing about how LinkedIn was scooping up the contents of iOS calendars, including sensitive information such as confidential meeting notes and call-in numbers, and transmitting them unencrypted in plaintext.
Or how about the time that LinkedIn controversially introduced (and then rapidly withdrew) a widget that meddled with the standard iOS Mail app, with the side effect of compromising the entire security of your email inbox, allowing LinkedIn to read every message you sent or received *outside* of the site?
I could go on, but you get the idea – and, anyway, I like to think that companies can learn. And, on this occasion, LinkedIn has done something that should be applauded.
In a blog post published yesterday, LinkedIn explained that it was introducing three new tools which go some way to boosting security, and granting members more control over their data.
First up, you can now check where (if anywhere) else you are currently logged into LinkedIn.
It’s all very well being logged into your LinkedIn account at home, but are you sure you logged off in the office? Alternatively, is it possible that a hacker has stolen your password and is currently messing around with your LinkedIn account on the other side of the world?
Now there’s an easy way to check.
Go to your settings and click on See where you are logged in to view a complete list of the devices that you are signed into the site.
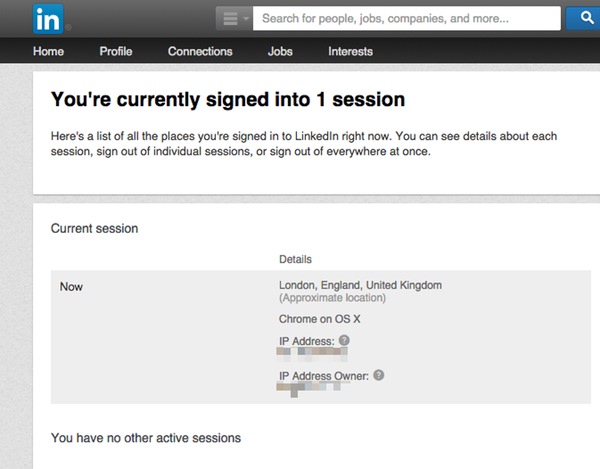
In the above screenshot, you can see that I have nothing to fear. There’s only one computer currently logged into my LinkedIn account, and I feel fairly comfortable that that’s me.
But if there had been additional sessions displayed, I would have been able check what browser and operating system is being used in each case, and the approximate location of the activity. Then, if I chose, logging them out remotely is just a mouse click away.
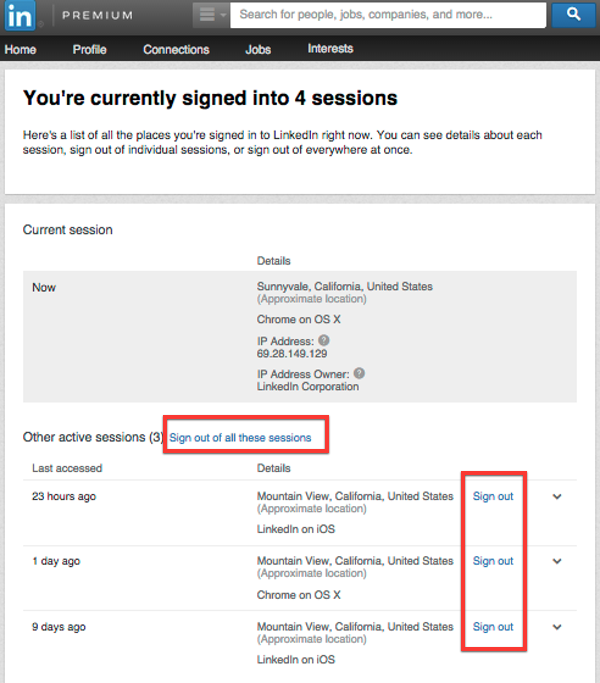
And, of course, if the other sessions were at locations or on devices I didn’t recognise then that might be a good time to consider changing my password and enabling LinkedIn’s two-factor authentication.
Next up, LinkedIn is offering more information to users in its password change email notifications – telling them, for the first time, when and where an account’s password change occurred.
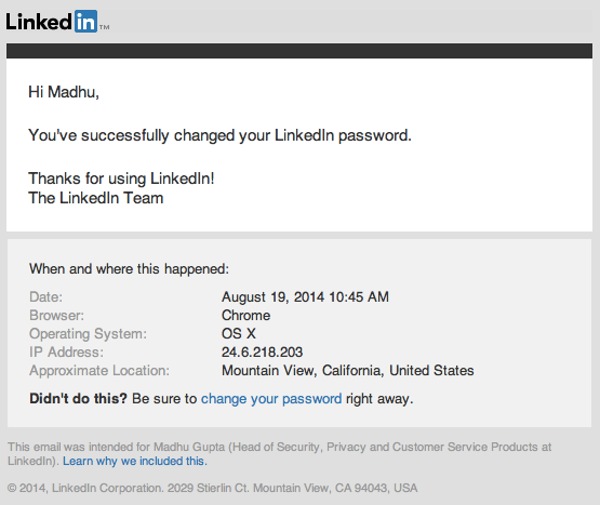
Finally, LinkedIn has taken a leaf out of Facebook and Google’s book and provided a way for users to easily export all of the data that the site stores about you, by requesting your data archive.
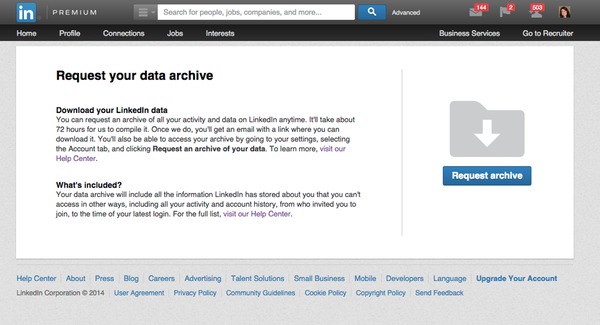
Once requested, it takes LinkedIn approximately 72 hours to collate the data that it holds on you, but never fear because you will be sent an email once the data is available for download.
None of these new features can really be considered rocket science, but it’s good to see LinkedIn introduce them and putting more power into the hands of its millions of users, who would feel pretty dreadful if their account was ever compromised.
It’s essential to keep your LinkedIn account out of the hands of fraudsters and internet criminals, precisely because it is the “business social network”.
In the past hackers have taken over accounts and posted poisoned links, and it’s easy to imagine the fraudulent behaviour that could take place if a worker’s colleagues and industry peers believed that it was John Doe communicating with them rather than a malicious attacker.
Of course, there’s no point to these tools if they aren’t actually used in the way that they’re designed.
Read LinkedIn’s blog, ensure that you’re familiar with these new features and the site’s two-factor authentication facility, and you will be better placed to protect both yourself and your fellow workers.
The post Now your LinkedIn account can be better protected than ever before appeared first on We Live Security.
![]()
IFA 2014: Huawei phablet has ‘iPhone-like’ fingerprint ID
Another major phone brand has added biometric security to a flagship smartphone as Huawei unveiled the ultra-thin Mate P7, complete with a rather unique fingerprint scanner, at Berlin’s IFA 2014 show.
The ultra-slim 6-inch phablet device uses an interesting biometric scanner – just like TouchID on the iPhone 5S, the user simply places a digit on the scanner, according to Tech Radar’s report.
This marks it out from the scanners found on the Samsung Galaxy S5 and HTC One Max, where the user has to swipe a digit over the scanner in a certain direction according to Digital Trends.
IFA 2014: Unique ‘iPhone-like’ scanner
Huawei is the largest telecoms equipment maker in the world. Biometrics has been one of the big tech trends for 2014, with devices as diverse as an iris-scanning smartwatch and earbuds which ‘read’ a wearer’s heartbeat using flashes of light in development, as reported by We Live Security.
Fingerprint scanners – and other biometric scans – have been predicted as “likely to become commonplace†in smartphones by MIT’s Technology Review.
Pocket-Lint says that the Ascend Mate P7 is a high-end handset with a polished metal finish just like the iPhone 5S, and a high-quality forward-facing 5-megapixel camera for “selfies.”
Digital Trends says, “Most importantly though, the Mate 7 has a fingerprint scanner that works exactly like the one on the iPhone 5S. Instead of having to swipe your finger across it like you do with Samsung’s Galaxy S5, you can simply place your digit on the scanner to unlock your phone and perform other tasks. The fingerprint sensor is located on the back of the phone below the camera.â€
No swiping required
The early part of this week has seen companies such as Samsung unveil new gadgets at IFA 2014 – but the show floor proper will open tomorrow, with more biometric gadgets expected. Read the report on We Live Security this week.
Smartphones are increasingly being used both in the home and the workplace as a security measure in their own right, with mobile workers accessing networks via “two factor authentication†software such as ESET Secure Authentication.
Adding fingerprint security to the handsets provides another layer of security for data.
The post IFA 2014: Huawei phablet has ‘iPhone-like’ fingerprint ID appeared first on We Live Security.
![]()
YouTube scam warning after fake “suspension†emails strike users
A YouTube scam where users are threatened with suspension for an unspecified “violation†of the video site’s guidelines has been circulating via email, according to Softpedia’s report.
The phishing YouTube scam is common enough to be causing users to raise questions on Google Groups, according to the site’s report.
The YouTube scam email reads, “We’d like to inform you that due to repeated or severe violations of our community guidelines and your YouTube account will be suspended 3 days from the time of this message.â€
YouTube scam: Trap leads to surveys
This form of scam is more common on Facebook, Softpedia notes. Other We Live Security reports describe such typical Facebook scams. As with Facebook, it’s likely that multiple variants of the scam email are circulating, so the text may vary.
The particular variant seen by Softpedia continues, “After careful review we determined that activity in your account violated our community guidelines, which prohibit spam, scams or commercially deceptive content.
“Please be aware that you are prohibited from accessing, possessing or creating any other YouTube accounts.â€
YouTube scams: What to do
ESET security specialist Mark James says, “The problem with phishing emails is that it’s their job to trick you into thinking they are legit, often using the same graphics or templates from legitimate emails from real companies.â€
“The methods they use include rewards for following links, penalties for not taking action and sometimes topics that offend easily forcing you not to take advice for fear of being judged or even prosecuted.â€
In this case, Softpedia says, the link in the emails directs the users to a series of surveys, some of which ask for the user’s phone number – which can lead to further SMS scams.
James says, “There are many ways to spot these false emails, firstly, most companies will have layers of procedures before sending out emails (especially intent of termination emails) that are proofread and checked over again before being sent, also look to see who its written to, if it is about a service that’s going to be cancelled then it SHOULD be directed to YOU not “Dear customer” or “Dear user”. They want your business and its important for you to feel your important.
“Check the sending email address. Don’t be fooled by the company name if it appears in the address, look to see if it looks right, most organizations want you to remember their details, so a long winded email address from PayPal with “pay” and “pal” in there somewhere won’t be from them, look for unrealistic threats – if it’s going to happen in 24 hours, or some other short time period, chances are it’s fake.â€
“DON’T open any attachments regardless of how enticing they seem, if you need to fill a form out to continue the service you are okay to call the company and ask them to mail the form to you, at that point you can verify if it is legitimate. DON’T follow any links, if the email has a link then check to see not only what it says but move your mouse over it and see WHERE it goes.â€
A detailed We Live Security guide to the latest phishing scams (and how to avoid them) can be found here.
The post YouTube scam warning after fake “suspension†emails strike users appeared first on We Live Security.
![]()