Kaspersky Lab today announced that the company was named partner of the month for August 2016 by Citrix Ready, a program that helps customers identify third-party solutions that are recommended to enhance virtualization, networking and cloud computing solutions from Citrix.
Category Archives: Antivirus Vendors
Antivirus Vendors
Advanced Reporting Tool, an Intelligent Control Platform
A platform that can detect a company’s internal threats? Many organizations and companies could have avoided major scandals if they acted in time: there’s the case of Snowden and the stolen NSA files, Bradley Manning and the US diplomatic cables, and Hervé Falciani and top-secret information from the HSBC private bank. These are all clear examples that, with cybersecurity, you can’t just cross your fingers and think “this won’t happen to me”. Any business could be threatened by an insider.
That’s why Panda Security has introduced the latest version of its Advanced Reporting Tool. This efficient and easy-to-use tool satisfies business needs; it is capable of maximizing Big Data performance to control the corporate resources.
Threats in the Workplace
PandaLabs detects 200,000 samples of new malware daily. It is imperative for businesses to control all security issues, especially those that stem from the misuse and abuse of corporate resources, leading to attacks, threats, vulnerabilities, or data leaks.
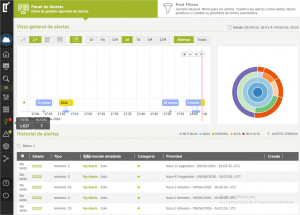
While Adaptive Defense collects all information on processes running on the endpoint, the Advanced Reporting Tool automatically stores and correlates this information. The platform automatically generates security intelligence that allow users to identify strange behaviors or problems.
The Advanced Reporting Tool enables the IT administrator to:
- Focus on relevant information, increasing efficiency in the IT department by finding security risks or misappropriation in the corporate infrastructure.
- Pinpoint problems by extracting behavior patterns from resources and users, identifying its impact on the business.
- Alert in real-time about all events that could be a potential data breach.
- Generate configurable reports showing the status of key security indicators and how they are evolving.
What does the latest version offer?
 In addition to the existing Big Data Cloud Service and its real-time alerts, the latest version includes predefined and adaptable analysis with three different action areas:
In addition to the existing Big Data Cloud Service and its real-time alerts, the latest version includes predefined and adaptable analysis with three different action areas:
- Information about IT security incidents: generates security intelligence then processes and associates those events as intrusion attempts.
- Controls network applications and resources: detects user patterns of IT resources.
- Controls access to business data: shows any access to confidential information and its online traffic.
Feedback from SIEM system
For organizations already using a SIEM, the Advanced Reporting Tool compliments it providing a SIEMFeeder which feeds your SIEM relevant data and associates it with the information you already have. The SIEMFeeder gathers information from all endpoints that are protected by Adaptive Defense.
The feedback provided by the SIEMFeeder enables you to detect insiders before they become the biggest threat to your business. The SIEMFeeder creates behavioral logics and locates all anomalies existing in your technological system.
The post Advanced Reporting Tool, an Intelligent Control Platform appeared first on Panda Security Mediacenter.
Avast and AVG combine to better protect your business
We are now one company . . . whether you use an AVG or an Avast product, we will continue to offer and support both AVG and Avast branded products.
In July, we announced that we signed an agreement to acquire AVG. We have now acquired a majority stake in the company, completing the initial tender offer for all of the outstanding ordinary shares of AVG Technologies. That means we will operate as a single company as of Monday, October 3, 2016 and can officially welcome AVG business users to Avast! I have been leading Avast’s SMB business since 2015, and will drive the integration of the two company’s business divisions. With an existing SMB business and reseller base that was many times larger than Avast, we will be integrating Avast’s program into the AVG business program.
The acquisition will overnight vault Avast into a leadership position in the SMB security market. Our gain will also be your gain. By combining the strengths of Avast and AVG under one company, you can now look forward to a stronger threat detection network powered by the largest install base (by far) of any competitor. The new Avast now protects more than 400 million mobile and PC users worldwide, each of which acts as a sensor. Whenever one of these sensors encounters a new threat, the threat is sent to our Threat Labs for analysis and a detection is created to protect the rest of our network. This means your business is already being better protected from the latest threats.
Avast will continue to offer and support both the AVG and Avast branded products for the foreseeable future (more details about this can be found here). We want our customers to be reassured that whether you use an AVG product or an Avast product, we will continue to have experts support you. We are nothing without our customers and partners like you, who helped us get to where we are today.
We are thrilled about what the future will bring and are looking forward to finding new ways to add value for you, our customers. We are looking forward to the innovative products this acquisition will produce and the momentum it will create in the market.
Forward-Looking Statements
This press release contains forward-looking information that involves substantial risks and uncertainties that could cause actual results to differ materially from those expressed or implied by such statements. All statements other than statements of historical fact are, or may be deemed to be, forward-looking statements within the meaning of the federal securities laws, and involve a number of risks and uncertainties. In some cases, forward-looking statements can be identified by the use of forward-looking terms such as “anticipate,” “estimate,” “believe,” “continue,” “could,” “intend,” “may,” “plan,” “potential,” “predict,” “should,” “will,” “expect,” “are confident that,” “objective,” “projection,” “forecast,” “goal,” “guidance,” “outlook,” “effort,” “target,” “would” or the negative of these terms or other comparable terms. There are a number of important factors that could cause actual events to differ materially from those suggested or indicated by such forward-looking statements and you should not place undue reliance on any such forward-looking statements. These factors include risks and uncertainties related to, among other things: general economic conditions and conditions affecting the industries in which Avast and AVG operate; the uncertainty of regulatory approvals; the parties’ ability to satisfy the conditions to the contemplated tender offer, AVG’s delisting from the New York Stock Exchange and suspension of AVG‘s reporting obligations under the Exchange Act and to consummate the transactions and their plans described in this press release; and AVG’s performance and maintenance of important business relationships. Additional information regarding the factors that may cause actual results to differ materially from these forward-looking statements is available in AVG’s filings with the U.S. Securities and Exchange Commission, including AVG’s Annual Report on Form 20-F for the year ended December 31, 2015. These forward-looking statements speak only as of the date of this release and neither Avast nor AVG assumes any obligation to update or revise any forward-looking statement, whether as a result of new information, future events and developments or otherwise, except as required by law.
Additional Information and Where to Find It
This press release does not constitute an offer to purchase or a solicitation of an offer to sell any securities of AVG. The solicitation and offer to purchase ordinary shares of AVG is being made pursuant to a tender offer statement on Schedule TO, including an Offer to Purchase, a related letter of transmittal and certain other tender offer documents, filed by Avast with the SEC on July 29, 2016 (as subsequently amended, the “Tender Offer Statement”). AVG filed a solicitation/recommendation statement on Schedule 14D-9 with respect to the tender offer with the SEC on July 29, 2016 (as subsequently amended, the “Solicitation/Recommendation Statement”). AVG shareholders are urged to read the Tender Offer Statement and Solicitation/Recommendation Statement, as they may be amended from time to time, as well as any other relevant documents filed with the SEC, carefully and in their entirety because they will contain important information that AVG shareholders should consider before making any decision regarding tendering their securities. The Tender Offer Statement and the Solicitation/Recommendation Statement are available for free at the SEC’s website at www.sec.gov. Copies of the documents filed with the SEC by AVG will be available free of charge on AVG’s website at investors.avg.com.
![]()
![]()
The New Avast Brand
![]()
Your IoT toy vs. my freedom

Insecure IoT devices come with a whopper of a price tag.
The post Your IoT toy vs. my freedom appeared first on Avira Blog.
Organizations ‘need to deliver social engineering training’
More focus on how to spot social engineering attacks is needed in organizations, according to expert Jenny Radcliffe.
The post Organizations ‘need to deliver social engineering training’ appeared first on WeLiveSecurity.
![]()
Kaspersky Lab Report Reveals the Online Habits of Consumers Over 55 Years Old
86 percent of consumers 55 years old and over don’t believe they are a target for cybercriminals
Hackmud – or how I learned to be a hacker (not really)

I’m a hacker.
The post Hackmud – or how I learned to be a hacker (not really) appeared first on Avira Blog.
Got something to hide? Don’t pixelate it.
![]() Many businesses share documents that are pixelated in order to protect private information, whether they be bank account numbers, photographs or other private information. Although pixelation used to be a simple and sufficient way to hide confidential information, now computers are smart enough to read these distorted images—even when your eye cannot. Pixelated documents are no longer safe!
Many businesses share documents that are pixelated in order to protect private information, whether they be bank account numbers, photographs or other private information. Although pixelation used to be a simple and sufficient way to hide confidential information, now computers are smart enough to read these distorted images—even when your eye cannot. Pixelated documents are no longer safe!
Researchers from the University of Texas and Cornell Tech have developed software based on artificial intelligence that is capable of reading standard content-masking techniques (like blurring or pixelation) in order to read what was originally covered up.
One of the authors, Vitaly Shmatikov, warned that, aside from the complex technical developments, “the techniques we’re using in this paper are very standard in image recognition, which is a disturbing thought.”
But these researchers aren’t the only ones developing this type of software. More powerful object and facial recognition techniques already exist for those who want to use them. This means cybercriminals may already have the tools to unveil private information you thought was hidden.
To carry out their research, the team fed neural networks images with faces, words and objects. The more times the neural networks “see” these images, the easier they can recognize them. After successfully memorizing the photos, the neural networks were able to successful defeat three privacy protection technologies including YouTube blurring technology, pixelation and Privacy Preserving Photo Sharing (P3).
In conclusion, pixelating or blurring information is no longer the best way to share confidential documents. After this research, the software was able to recognize 80% of the distorted images.
According to Lawrence Saul, a machine learning researcher at the University of California, San Diego, “For the purposes of defeating privacy, you don’t really need to show that 99.9 percent of the time you can reconstruct. If 40 or 50 percent of the time you can guess the face or figure out what the text is then that’s enough to render that privacy method as something that should be obsolete.”
To keep you corporate information safe, the best you can do is avoid sharing it (if you can) and above all, protect it with the appropriate protection for your company.
The post Got something to hide? Don’t pixelate it. appeared first on Panda Security Mediacenter.
A Fresh Start for Google’s Pixel: Tips for Your New Android Phone
As the anticipated release of the Google Pixel nears, it may be time to check those old storage habits to ensure your new Android phone performs at its maximum capacity.
We’re all waiting with bated breath for Google to release the new Pixel phone tomorrow—it’s rumored to have twelve megapixels in the rear camera and Full HD display to view your photos.
While Android enthusiasts are bubbling with excitement about the new features, better images typically also mean heavier files. And you can bet that one platform agnostic behavior will remain: extraordinary laziness in clearing out bad and/or duplicate photos.
AVG Technologies recently collected data from 1.5 million users of AVG Cleaner for Android—which creates more space, speed, and battery life for your phone or tablet—and found that the app helped users quickly delete 26 million bad photos and 30 million similar photos. The bad photo overload phenomenon is global, and life is too short to spend even a minute manually scrolling through thousands of pictures to identify and remove the trash.
AVG Cleaner is free, and you can install as soon as you get your shiny new Pixel to make sure your old habits don’t mar your new phone. And it isn’t just a one-time solution: Cleaner can also quickly remove hidden clutter, unused apps, call history, your largest files, and more to free up space for the apps, photos, and music you love most. Just turn on Auto Clean Reminders and AVG Cleaner will automatically find the clutter for you and let you clean it with a simple reminder in the notification panel of your phone or tablet. It’s that easy.
Regardless of how you keep your phone running, it’s always fun to start with a clean slate. We can’t wait to see what other features Google unveils at tomorrow’s event!
![]()
![]()


