
You’d rather not heft a one-liter mug to get your favorite beverage. What about security updates for your device?
The post Oktoberfest: Updates in a Mass or through a straw? appeared first on Avira Blog.
Antivirus Vendors

You’d rather not heft a one-liter mug to get your favorite beverage. What about security updates for your device?
The post Oktoberfest: Updates in a Mass or through a straw? appeared first on Avira Blog.

Ransomware returns to its earlier hands-on approach.
The post Locky takes the wheel again appeared first on Avira Blog.
This season finale had me sitting in front of the TV saying “what?” a couple of times – a sign that this was another great episode!
![]()
ESET’s latest research analyzes a piece of malware active since 2012, but which has targeted one specific country – Libya.
The post Book of Eli: African targeted attacks appeared first on WeLiveSecurity.
![]()
There have been thousands of top secret documents leaked, confidential information pertaining to individuals has been stolen, cyber espionage between powerful governments has occurred, and attacks have been performed by personnel with privileged access. These are all examples that confirm that propagandistic pursuit and economic gain drive cybercriminals, and they target those who are willing to pay for the retrieval of their valuable information, such as institutions in the public sector.
PandaLabs, Panda Security’s anti-malware laboratory, presents the “Privacy in Public Administration” whitepaper; detailing numerous cyber-attacks on countries that could almost have come from a science fiction story.
The technological revolution in the public sector, the digitalization and storage of information, and the boom in online services to simplify administration for the public have led to an exponential growth in the generation, storage and processing of confidential data; data which must be treated with the utmost care. Consequently, the public sector now faces a new series of demands in risk prevention, security and legal compliance.
During the past decade, crimes including cyber-terrorism, cyber-espionage and hacktivism have been on the rise, threatening the privacy of Public Administrations, businesses and nations:
 2010: Bradley Manning, a US soldier, copied 700,000 confidential documents and used WikiLeaks to publish the data. In total almost half a million records from the Iraq and Afghanistan conflicts, and more than 250,000 secret U.S. diplomatic cables.
2010: Bradley Manning, a US soldier, copied 700,000 confidential documents and used WikiLeaks to publish the data. In total almost half a million records from the Iraq and Afghanistan conflicts, and more than 250,000 secret U.S. diplomatic cables.
2013: Ed ward Snowden, a former employee of the CIA and NSA, published top secret documents through the Guardian and the Washington Post concerning various NSA programs, including the mass surveillance programs PRISM and xkeyscore.
ward Snowden, a former employee of the CIA and NSA, published top secret documents through the Guardian and the Washington Post concerning various NSA programs, including the mass surveillance programs PRISM and xkeyscore.
2016: A total of 19,252 emails (including attachments) from 8,034 servers of the US Democratic National Committee sent between January 2015 and May 2016 were revealed on WikiLeaks this July. The security company contracted by the Democratic National Committee has claimed that the hack was the work of at least two different groups of hackers linked to a Russian government agency in an action designed to favor Republican candidate Donald Trump.
Now, three months before the US elections, the FBI has confirmed the hacking of at least two electoral databases by foreign hackers who have extracted voter information from at least one of them. There is an ongoing investigation and IPs have been traced back once again to Russian hacking forums. Coincidence?
The emergence of new players from different backgrounds and with varying motivations combined with their ability to act in any security dimension, hinders the identification of aggressors and decreases the ability of countries to adequately respond. Current legislation is not adapted to the new cyber-crime dynamic or to new technological or data management demands.
To prevent new attacks on public agencies, a common regulatory and legislative framework is needed, with responsibilities shared between states. One such example is the new regulatory framework passed in the EU in 2016.
For public institutions, success in ensuring cyber-security lies with meeting certain requirements:
To this effect, the implementation of advanced technologies such as Adaptive Defense 360, as a complement to traditional antivirus solutions or perimeter security, enables compliance with guidelines and the technical requirements outlined above, since Adaptive Defense offers guaranteed security against threats and advanced targeted attacks on companies.
| International Edition | |||
| Edición América Latina | Edición México | ||
| Edição Portugal | Ausgabe Schweiz | ||
| UK Edition | US Edition |
The post Panda Security Protects Privacy in Public Administration appeared first on Panda Security Mediacenter.
With these top tips, you should have no trouble in keeping yourself protected against all sorts of phishing attacks.
The post 5 simple ways you can protect yourself from phishing attacks appeared first on WeLiveSecurity.
![]()
Kaspersky Lab announced today that its experts investigated how cybercriminals could exploit new biometric ATM authentication technologies planned by banks.

Data Science — from university to industry in the area around the Lake of Constance (Bodensee), Vorarlberg, St. Galler Rheintal, and Liechtenstein. Everyone is welcome to join and to exchange experiences about big data, machine learning, predictive modeling, data visualization, and all related topics on how to extract knowledge from data.
The post Data Science Meetup hosted by Avira (Data Science @Avira) appeared first on Avira Blog.
Ransomware is one of the world’s fastest growing malware categories. In June, we surveyed businesses to understand who had heard of the term ‘ransomware’ and what they understood about it. 381 of our small-to-medium business (SMB) customers in the US and UK responded to our questions and the results proved revealing and concerning.
Here are the key points:
68% of respondents said they had heard of the term ‘ransomware.’
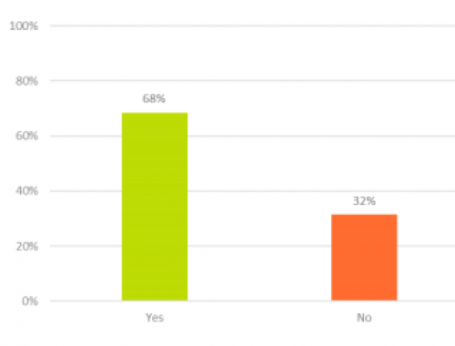
That may look like a good percentage, but this also indicates that even with security industry, media and governments working hard to educate businesses about the risks, nearly 1 in 3 is still not aware of this significant risk.
So what is ransomware and how does it impact businesses?
Ransomware is a generic term for a category of malware that restricts access to a device or the file(s) on a device until a ransom is paid. It’s a method for criminals to make money by infecting the device and has become very effective at causing havoc for a business or organization that is unfortunate enough to become a victim.
It’s not new, which is why the 32% concerns me. The first cases were reported as far back as 2005, which took the form of fake antivirus software claiming you had issues that required payment in order to be fixed.
Over time, ransomware morphed into scareware messages. Scareware messages, designed to trick users into downloading malicious software and often disguised as communications from law enforcement, typically claim that a device has been infected or that the usage history of a device shows illegal activity—or in some cases blatantly locking files until you call and pay the ransom.
The 68% of respondents claiming to know what ransomware is had very different opinions, many of them inaccurate. When asked to explain the term, it turns out that 36% (of the 68%) didn’t actually know what it was.
A major security concern
Since 2013 when Cryptolocker ransomware first surfaced, ransomware has now become a major security issue with organizations being held to ransom – and in some cases paying to get their data unlocked. Numerous incidents have been cited where thousands of dollars have been paid: hospitals, charities, hairdressers have all been held to ransom. One university has suffered 21 attacks in the last year alone!
The true scale of the problem is somewhat hard to define though because, understandably, many businesses and organisations are reluctant to reveal they’ve been held to ransom because of fears about being targeted again, or losing existing or new customers.
People are held to ransom in just a few seconds
Unsuspecting victims are infected through emails impersonating customer support personnel from well-known company brands. Once activated, the malware encrypts files and demands payment, typically a few hundred dollars within a timeframe of 48 or 72 hours.
Last year alone, the FBI received 2,453 complaints about ransomware hold-ups last year, costing the victims more than $24 million dollars! Earlier this year, the UK National Crime Agency claimed ransomware attacks have increased in frequency and complexity, and now include public threats by the perpetrators to publish victim data online, as well as the permanent encryption of valuable data.
4 ways to protect your computers and networks against ransomware
Don’t be the 1 in 3
Taking proactive steps to protect your organization from a ransomware attack is essential to the smooth running of your business—it is your livelihood, after all. Contingency and remediation planning are also crucial to business recovery and continuity, and these plans should be tested regularly.
![]()
![]()
Biometric Skimmers Pose Emerging Threat To ATMs – Dark Reading