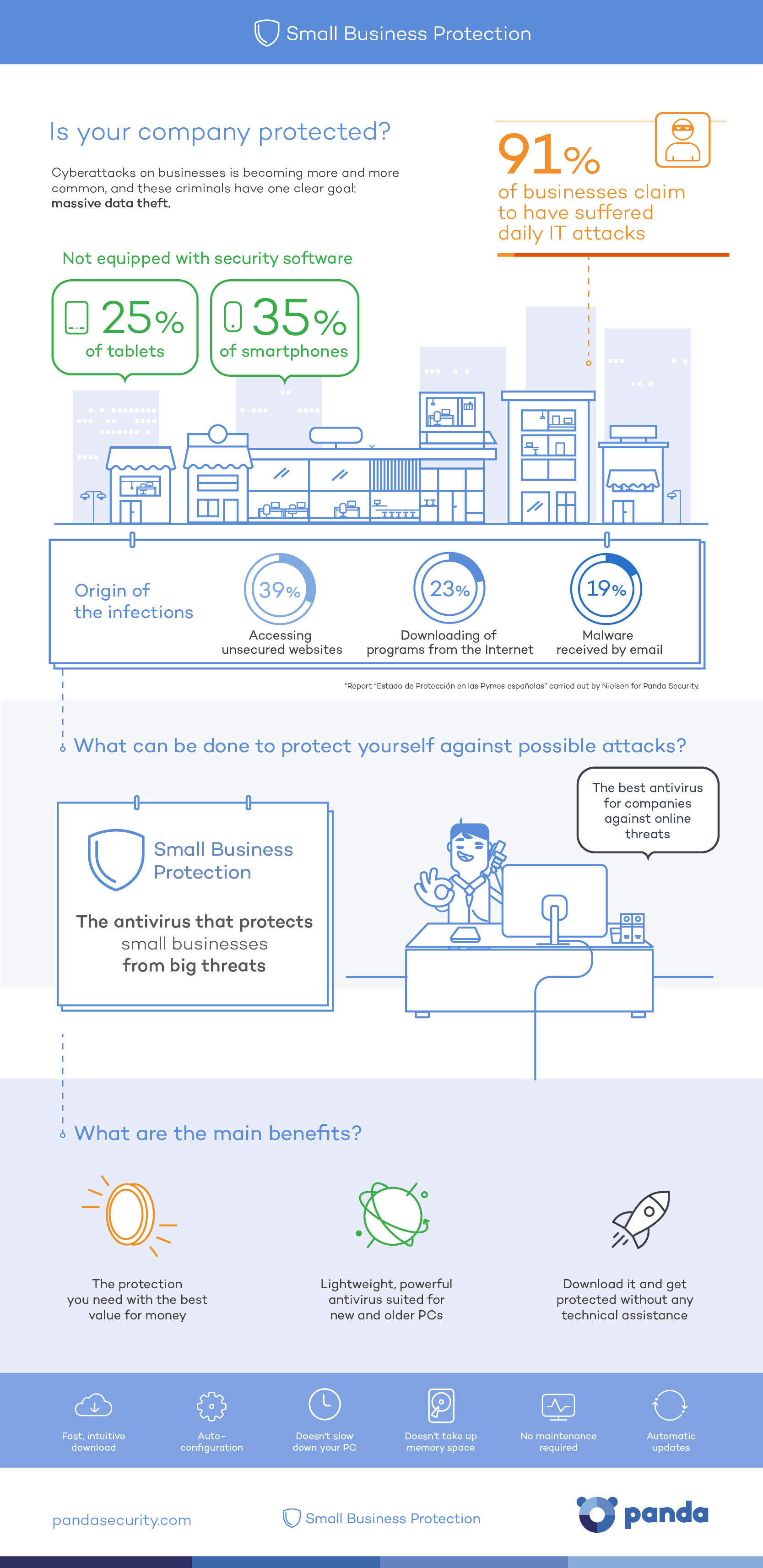
When the start of a New Year rolls around it is common for us to make new promises and resolutions to better ourselves during the coming months, be it hitting the gym more frequently, quitting smoking, or just keeping in touch with friends and family. Unfortunately, despite our best efforts, over time we slowly lose focus and put those goals off until next time.
However, there are some promises that we should keep, and one of them is to be more cautious when it comes to the security of our mobile devices. Seeing as we now use smartphones daily to complete a myriad of tasks, it’s essential to follow some simple steps to keep our beloved Android devices – the most popular operating system worldwide – free from danger.
Unlocking code
By default, your Android device can unlock itself by having a finger placed over the screen. In the event of theft or loss, make sure you have a better barrier of protection to stop others gaining access to the device. You can ensure this by simply setting a PIN or password for your device, once you make sure it’s not too easy to guess. If it seems too much of a hassle to have to introduce a password whenever you want to access your phone, then simply activate Smart Lock, which allows you to leave your Android device unlocked when at work or at home.
Prepare yourself for the worst
If the fateful day in which you lose your phone arrives, you’ll be glad to have been prepared by having Android Device Manager installed. It allows you to know where your phone is, and if it ends up in the hands of someone else, you can remotely block it. You can also remotely delete all information on the device, but before doing that make sure that you have…
Security copies
These are essential if you want to recover all of the information and applications that you had installed in the event of loss or theft, but also if the device breaks or gets infected by malware. Photos, videos, songs, and other files can be backed up to your Google account. For anything else, all you need is…
A good antivirus
It’s the number one security measure and the best barrier that you can put between your mobile and cybercriminals. A complete security solution with quick updates can protect your smartphone from recent and unknown threats. What’s more, as we indicated in the previous point, it will include features that allow you to make security copies and other basic functions that will make your device secure.

Apps from reliable sources
Be sure to only download apps from official stores such as Google Play, Amazon, and the device manufacturer’s website (Samsung, Sony, Motorola, etc.) and keep the option for “unknown origin” deactivated at all times, unless you want to install an app that comes from a secure source. If you do so, remember to deactivate it immediately.
Application verification
Even if you don’t install apps from unknown sources on your smartphone, it’s best to keep the Android application verification activated, which monitors the activity of your device to ensure that any anomaly is detected rapidly. If it comes across anything dangerous, it will recommend that you remove the application immediately.
Keep an eye on permissions
Whenever you install a new app on your device, a list of permissions will appear: access to camera, your list of contacts, Internet, etc. Unfortunately, we usually accept these without taking a good look at what it’s asking us. For example, does your torch really need to consult your GPS to know your location? If something seems unusual, then it’s best to be cautious. Luckily, from Android Marshmallow (6.0) on, a new permissions management system will make it possible to allow or deny each request on a case by case basis.

Encryption
All information on certain Android devices, such as Nexus 6 and 9, is encrypted by default. As for others, from the new version of the Jelly Bean (4.1) operating system on, you can activate it in the security options, making your device that bit more secure.
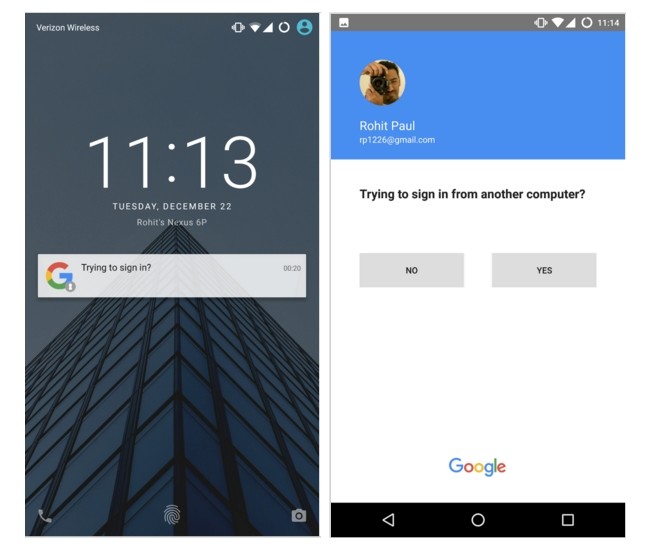
Two-step verification process
Your Google account is the epicenter of activity on your Android device, therefore keeping it safe is essential if you want to keep your mobile device secure, too. If you haven’t already done so, activate the double verification mechanism which will ask for a code every time that someone tries to access your profile from another device.
Be wary of public Wi-Fi networks
All it takes is €70 and 20 minutes for an attacker to steal your information via an insecure public network. Be careful when connecting to Wi-Fi in cafés, restaurants, libraries, or airports, and never use them for carrying out tasks involving your bank. Also, ensure that you can use a VPN to surf them.
The post Everything you need to know to keep your Android safe in 2016 appeared first on MediaCenter Panda Security.