The phenomenon that is Minecraft began life back in 2009 as a sandbox construction game and has grown into one of the most popular games in history with hundreds of millions of players all over the world interacting via computers, consoles and mobile devices – there is even a dedicated version for the Raspberry Pi where programmers are encouraged to modify the game code for educational purposes.
Video game merchandise based around the Minecraft world tops the UK charts for sales in 2014 and over 2 million Minecraft books were sold in the UK last year.
The fan-base have created extraordinary objects and landscapes including a 1:25 scale Ordnance Survey map of the UK, a working 16-bit computer and a plan for a life size model of the British Museum is underway.
There are YouTube channels dedicated solely to Minecraft and top vloggers such as Stampy (@stampylongnose) who dedicate their lives making Minecraft adventures to show their millions of followers – with nearly 4 billion Minecraft videos viewed on YouTube every month.
The beginning of a single-player game of Minecraft is ensuring your character ‘Steve’ survives after being dropped alone into a digital world with empty pockets. ‘Steve’ must mine the resources needed to build a home and craft tools to protect him against the monsters which come out in the dark.

This process parallels the need to protect a new computer or mobile device before it is exposed to cyberthreats – the very first thing you should do is gather security resources and craft them into protective walls and tools against the ‘monsters’ from the dark side of the Internet.
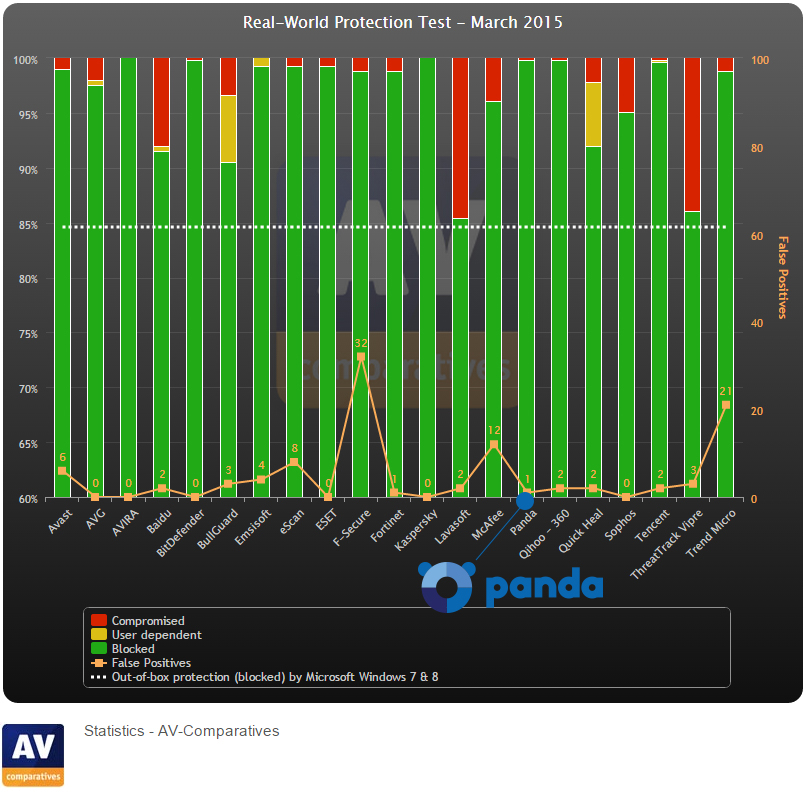
Minecraft users are well aware of these threats as recently an unpatched vulnerability, first reported to Mojang in July 2013, was published allowing Minecraft servers to be crashed
Back in January 2015 nearly two thousand Minecraft users had their login credentials leaked online with the hackers stating they had many more. How the hackers obtained the credentials is unknown with possibilities ranging from blunt force (zombie mob) guessing of credentials, targeted phishing attacks (skeletons), or even a security breach (Ender Dragon) at Mojang itself – something which the Microsoft owned software developer has since denied.
Other monsters and environmental dangers within Minecraft are also analogous to the various types of cyberthreats including:
- Pervasive Creepers are the explosive old-skool malware simply out to cause destruction.
- Pools of lava and rock falls can appear at any time while mining just as a drive-by vulnerability of a compromised website can infect your device while browsing.
- Falling into a pool of lava will not only kill you, but also cause the loss of all the precious objects and clothing being carried – ensure you back up your important files to provide extra security against destructive malware and ransomware.
- Dual threats come from Spider Jockeys similar to a vulnerability allowing malware to silently infiltrate the computer – the vulnerability must be patched and the malware cleaned to ensure enemy is vanquished.
- The largest and most complex Minecraft threat is the Ender Dragon which uses a multitude of attack methods similar to modern Advanced Persistent Threats (APTs) – only a layered security approach, user vigilance and auditing tools (or a very heavily armed ‘Steve’) can mitigate.
Luckily there are numerous security tools that can stop these monstrous problems interfering with the smooth-running of your digital life:
- The Antivirus and firewall are your house and walls stopping the majority of everyday threats.
- Proactive cloud-based detection is your armour protecting you wherever you go against new and unknown threats from all directions.
- Specific security tools are your sword, pick and shovel in the forms of virtual keyboards, application control and USB vaccines.
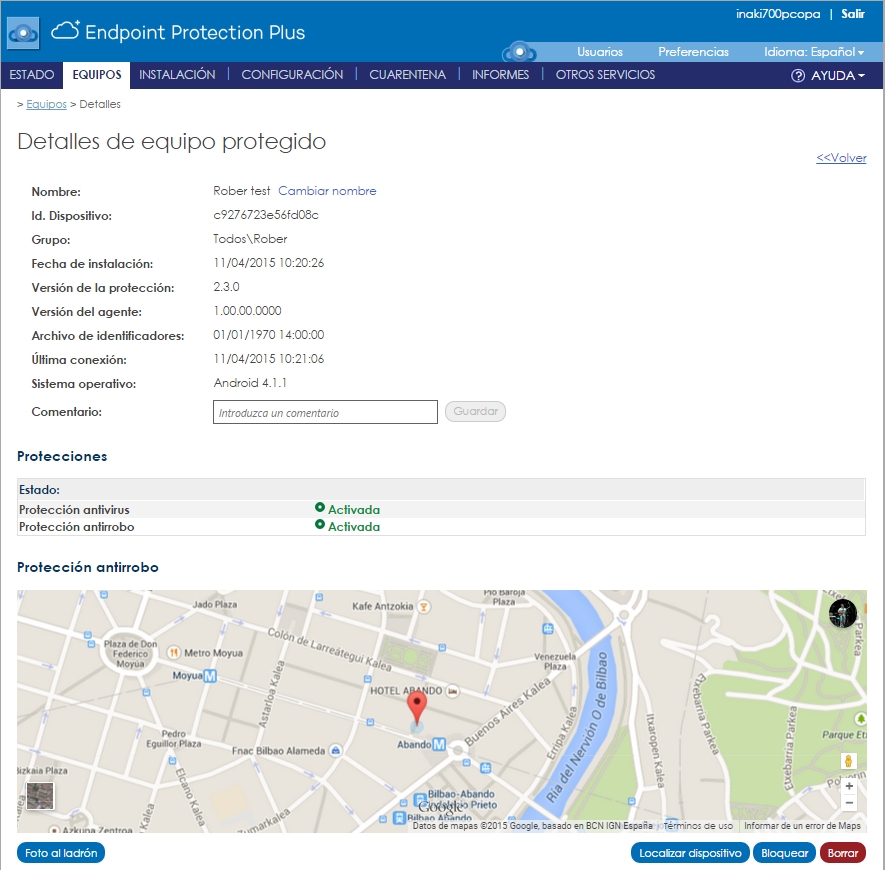
- If you are lost within the labyrinth of caverns then Mobile Device Locators are your map and compass, and antitheft may restore your resources when stolen by monsters.
- A lightweight security solution which protects without impacting on your device performance will allow you to carry all you want – Imagine discovering a huge seam of diamonds without being able to carry an iron pickaxe as your pack is full software bloat.
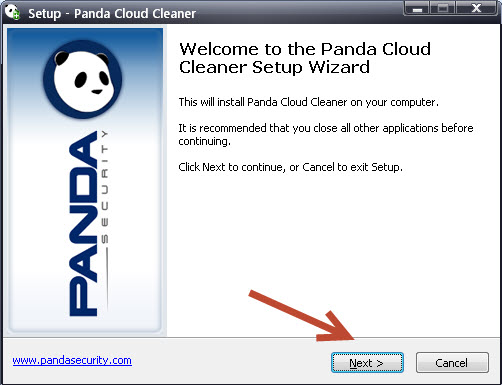
Panda Security offer a variety of free and paid for solutions for consumers and businesses to protect you against the cyberthreats visit Panda Security for details.
Neil Martin – Head of Marketing at the UK & Ireland arm of Panda Security
The post When Minecraft Meets IT Security appeared first on MediaCenter Panda Security.