After searching in Google for what appears to be ages, finally you find a web page that seems reliable, you start reading and realize that it contains all the information you were looking for! But your happiness is shattered when, suddenly, the host asks you to verify you are not a robot! A robot?! To prove you are a human being you enter your email address and register to the web page.
You rarely stop to think that your email will be captured in the platform’s database and that from now on, it will probably collapse your inbox with spam or fill your email up with malware. The solution to this problem is not to sing up to these web pages with your personal email account, but use instead a disposable one.
There are many programs out there that offer creating disposable email accounts, accounts that last a short period of time and whose spam won’t bother you. Some of the platforms that allow you creating temporal emails accounts are: Maildrop, Yopmail, Air mail, Guerrilla mail, Now my mail, Hide my ass, Mailinator o Email Temporal Gratis.
Most of them don’t require much registration information, others allow you to forward messages, and in some cases, you are able to select the account’s expiration date.
Mailinator, for example, is one of the longest-standing free disposable email services, which denies access to emails with attachments, and by doing so it prevents malware from entering the account. You just have to choose an available name and you may enter your temporary inbox. But we must warn you, these are shared accounts, so there might be more people using it.
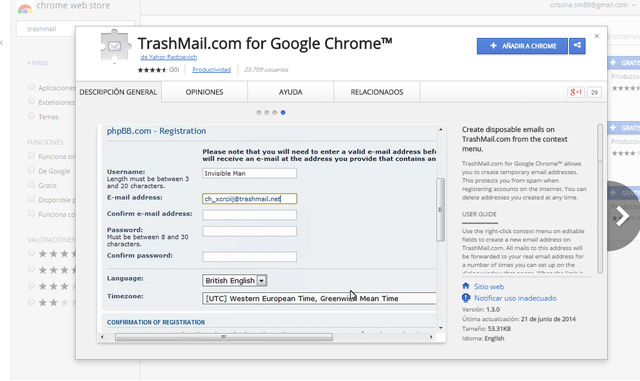
Another option is installing a browser extension to create disposable email accounts without accessing a web page. There is an extension available for both Firefox and Chrome, it is called Trashmail. You can create a new account in Trashmail by clicking on “Register a new account” and filling out all the information required, even the email address to which it will redirect your messages.
The next step is selecting your preferences on the General tab: you can choose the message’s lifetime and notify your regular email when the temporal email has expired.
You can also create an alias of your own email address. For example, in Gmail you can receive the messages sent to [email protected] and the email will arrive to [email protected].
Once you are inside the platform you register yourself with the first address, the alias, so the platform’s database only registers your alias email and won’t fill up your inbox. You can also choose which messages go directly to the trash, which are forwarded to other email accounts or which simply stay on your inbox, just by setting some filters. But you must take into account you will be sharing your real email address.
So, now you know, the next time a website asks you for your email address don’t jump in and write your personal or business one. Be cautious and use a disposable email address. You have everything to gain: it is easy, free and safe.
The post Disposable email address: easy, free and safe appeared first on MediaCenter Panda Security.