Smartphones, watches and a thousand home appliances. More day-to-day objects are connected every day. But the Internet of Things also runs on four wheels. Tomorrow’s cars will not be flying cars, as science fiction movies have told us, but their future lies in the Internet.
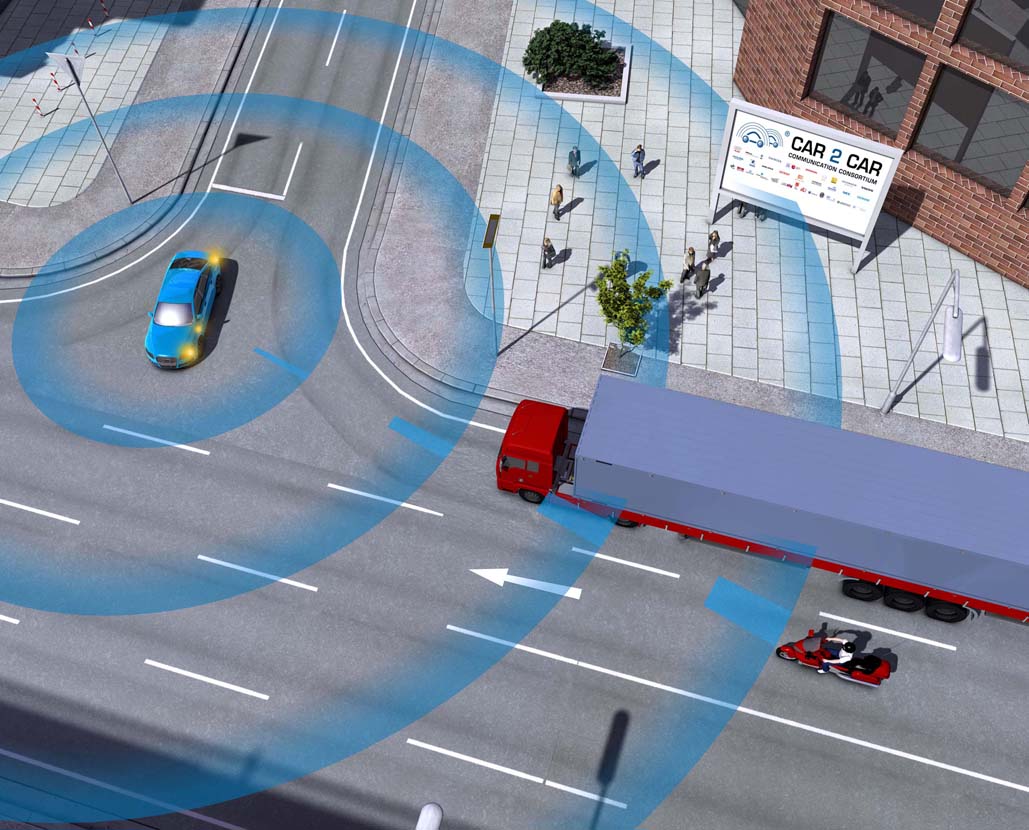
Cars will connect to one another to share information and they will also be connected to infrastructures to obtain data of interest in real time.
If the next revolution in automobiles will come from Car-to-Car (C2C) and Car-to-Infrastructure (C2I) connections, automakers will need an army of cyber-security experts to safeguard the cars of the future. If they can connect to one another, they will also be vulnerable to cyber-attacks.
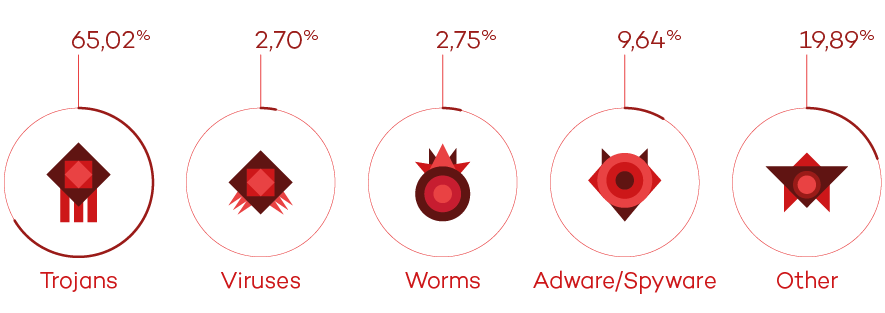
So far, cyber-security does not seem to be a strong point of the intelligent cars currently on the market. For example, a 14-year-old boy managed to gain wireless access to the brain of one of these cars using a $15 (just over €13) circuit board.
He achieved this feat at a hackathon organized a few weeks ago by Delphi, a US company that makes electronic systems for vehicles.
During this hackathon, the participants —the majority of them students— demonstrated that intelligent vehicles are not immune to IT attacks. They also showed that some of these vehicles can be opened (or even started) even though they are locked.
Internet-connected cars
The cars of the future will be a clear target for cyber-criminals, as not only will they be able to cause a large number of accidents by hacking the brain of these vehicles or steal them without needing to break the windows and hotwire them; the vulnerability of these cars will allow them to steal large amounts of data and wreak havoc in cities.
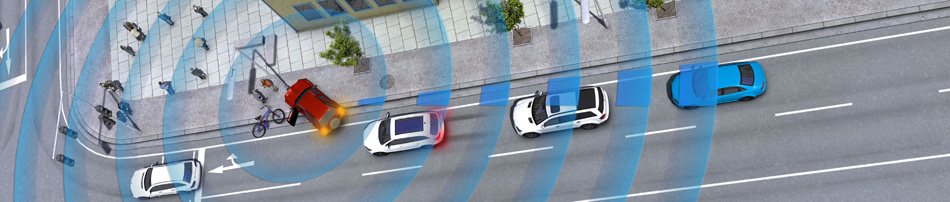
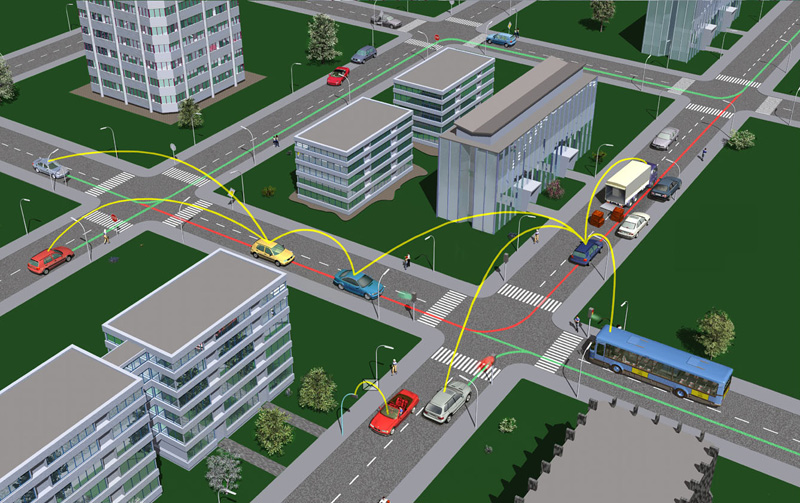
C2C and C2I systems will allow vehicles to constantly share information. Sharp breaking, breakdowns, traffic jams or the duration of traffic lights will be some of the data that could circulate through short-range wireless networks or simply through the car’s Internet connection.
A cyber-attack could turn one of these intelligent cars into the gateway to any information network connected to the vehicles, from the power grid to the system used by the police or the traffic light network in a city.
The solution lies in manufacturers of intelligent cars considering security and developing systems that detect which cars have been hacked in order to isolate them from the rest of the network.
There are many suggestions, such as installing security chips like those used on credits cards, or creating new software or hardware that establishes secure connections.
The post Car to car: Internet-connected cars. Will they be the main cause of accidents in the future? appeared first on MediaCenter Panda Security.