We all know the ‘Allow cookies?’ message. This option now appears in practically all websites. In fact, nowadays more people associate the term ‘cookies’ with its Internet use rather than with its edible origin.
Cookies are small data packets which Web pages load on to browsers for a whole range of reasons. Every time you return to the same URL, the computer sends back this little package of information to the server, which detects that you have returned to the page.
When you access your email account or Facebook profile, it is cookies that allow your user name and password to be saved, so the next time you won’t have to enter them again.
But apart from storing strings of digits and letters, webmasters can use these tools for monitoring the activity of Internet users.
These virtual spies collect information about your Internet habits: the pages you visit frequently and the topics that interest you. The problem is that they usually share this information with data analysis firms or those that design targeted marketing campaigns.
If, say, an ad for a food product appears on your screen after you visit a restaurant page, don’t be too surprised. Thanks to cookies, advertising can be tailored to consumers’ preferences.
Even though cookies are safe and won’t usually infect your computer with malware, it is not always clear in whose hands the collected data ends up or where it is stored.
A team of researchers from Queen Mary University, London, has managed to shed some light on this in one of its studies. They have basically been spying on the spies. They analyzed where the data of Internet users from around the world ended up in order to draw up a data circulation map.
The experts have focused on who is running cookies on user’s browsers. External companies (such as those marketing and data analysis firms mentioned above) send these data packets from a domain different to the site so they can be detected when they do this. With this methodology they were able to analyze the 500 most popular pages in 28 countries.
The results have shown that this practice extends across the world. You can also see in the image the areas of the planet where Internet user privacy is most compromised.
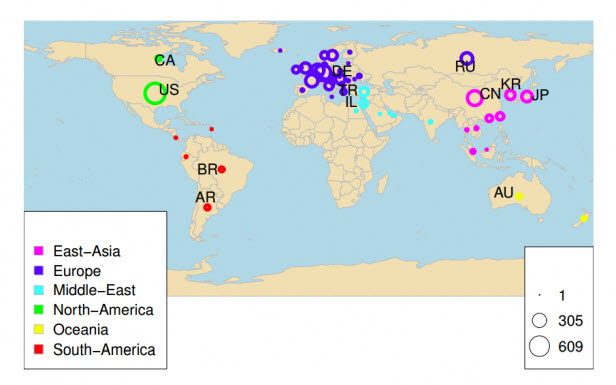
While in Europe, South America and Oceania the amount of local companies accessing user data is quite similar, the number is greater in Turkey and Israel. The origin of the snoopers is also interesting: most come from Russia or Germany. Those based in the USA often end up on browsers in the Middle East.
Scientists believe that this distribution reflects Internet privacy legislation in different countries. In most European countries, where there are laws regulating third-party access to user data, there aren’t so many ‘spies’ as in China or Turkey, where such rules are scarce. But spies are everywhere, so experts continue to call for tougher measures to combat the trafficking of personal information.
The post How cookies work? appeared first on MediaCenter Panda Security.