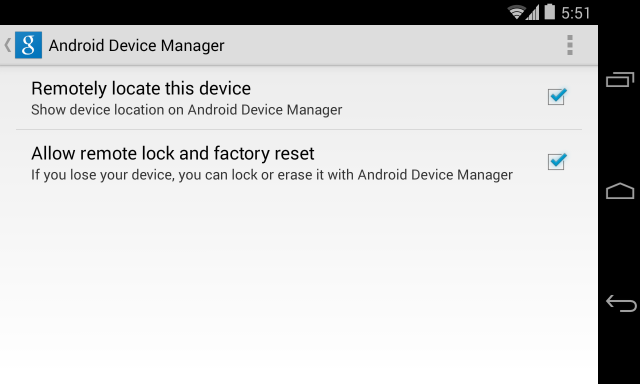
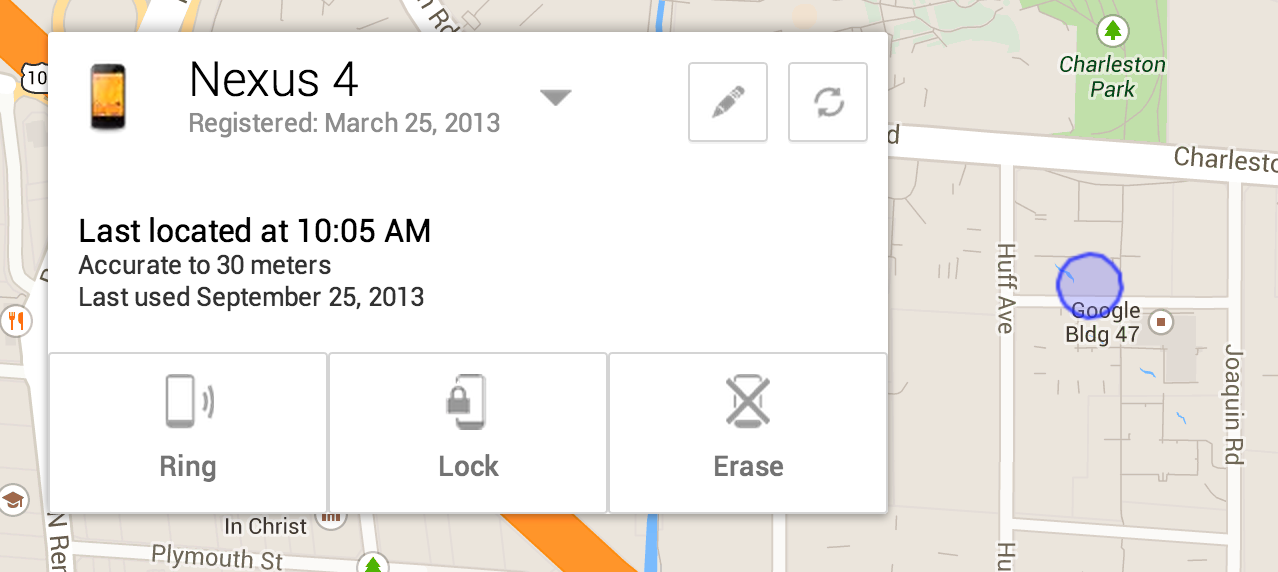
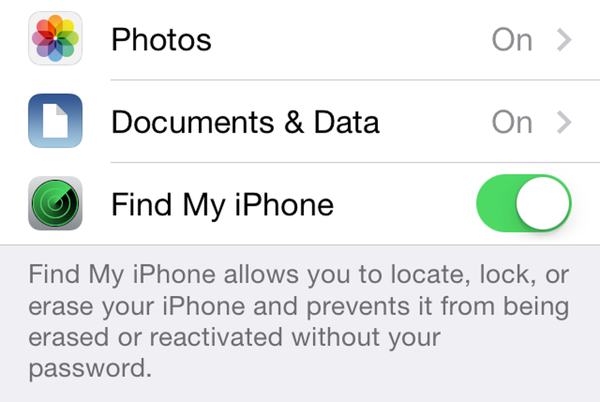
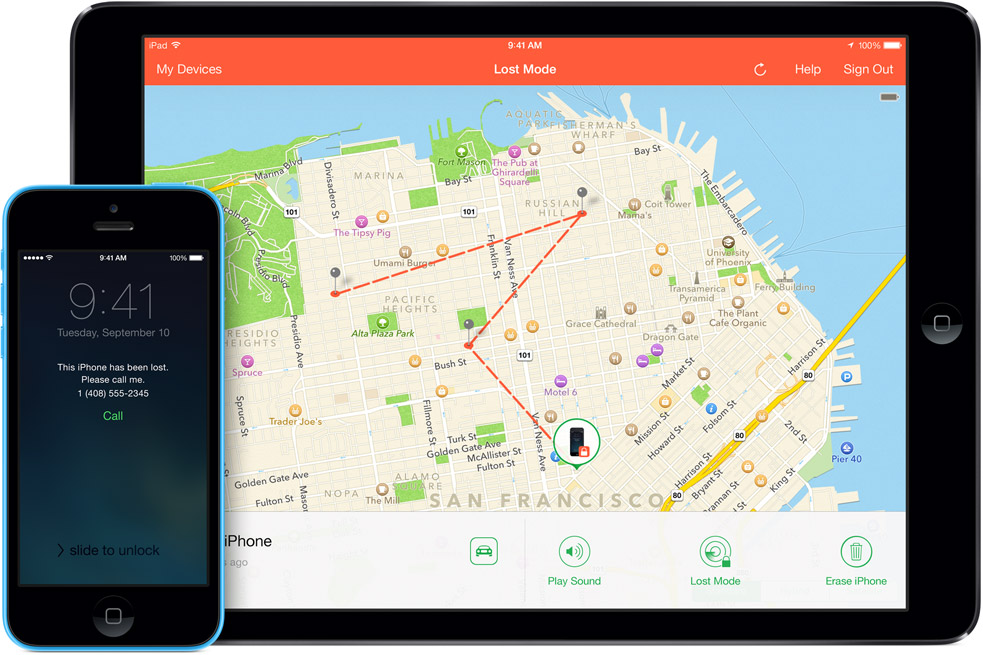
iPhone and iPad users who turn on Avast SecureLine VPN while on unsecured Wi-Fi are protected from iScam.
It’s a common belief (and myth) that Apple products are invincible against malware. This false line of thinking has recently again been refuted, as iPhone and iPad users have been encountering a ransomware threat that freezes their Internet browsers, rendering their devices unusable. The ploy, commonly known as iScam, urges victims to call a number and pay $80 as a ransom to fix their device. When users visit an infected page while browsing using the Safari application, a message is displayed saying that the device’s iOS has crashed “due to a third party application” in their phone. The users are then directed to contact customer support to fix the issue.
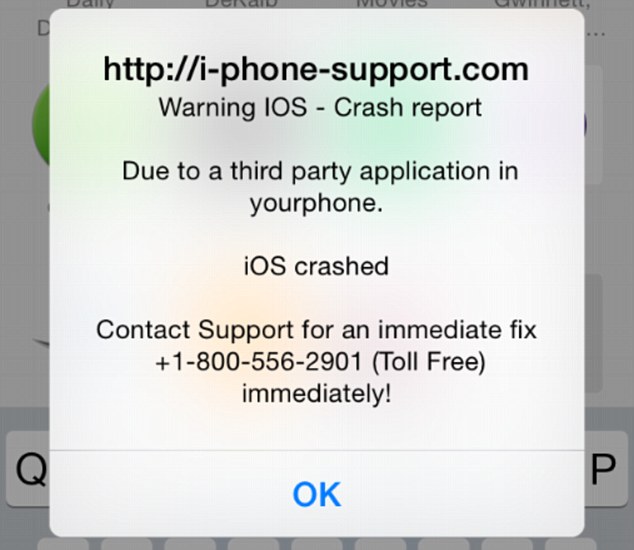
iScam displays a “crash report” to affected users. (Photo via Daily Mail)
In the midst of this vexing threat, Avast’s suite of security applications identifies URLs which contain malicious content. When discovered, these addresses are flagged for malware and then stored in our blacklist database.
While scanning for malicious URLs, we discovered that many of the servers related to iScam are located in the United States. While iScam has affected users located in both the U.S. and U.K., the origins of the threat have remained fairly nebulous up until this point. Here are a few examples of where we’ve discovered malicious servers in the U.S.:
- Scottsdale, Arizona (system-logs.info)
- Concord, North Carolina (pcassists.info)
- Kirkland, Washington (Adbirdie.com)
- Chicago, Illinois (pcsafe.us)
- Los Angeles, California (clevervc.com)
Every cloud has a silver lining – in this case, you can celebrate the fact that you’re protected from iScam using Avast SecureLine VPN. Not only does Avast SecureLine VPN protect you while browsing on unprotected Wi-Fi networks, but it also scans websites to check for malicious content and keep you from becoming affected by them. Once Avast SecureLine VPN is installed onto your iPhone or iPad, it automatically notifies you of the risks of connecting to unsecured Wi-Fi and you have the option of connecting to the secure VPN. Once turned on, Avast SecureLine VPN creates a private ‘tunnel’ for your data to travel through, and all your activities done over the Internet – inbound and outbound through the tunnel — are encrypted. If a website is infected with iScam, Avast SecureLine VPN blocks it, so users will not encounter the scam. For your best protection, Avast SecureLine VPN is available to download in iTunes.
How to clean your system if you’ve been infected by iScam
- Turn on Anti-phishing. This can be done by visiting Settings > Safari and turn on ‘Fraudulent Website Warning’. When turned on, Safari’s Anti-phishing feature will notify you if you visit a suspected phishing site.
- Block cookies. For iOS 8 users, tap Settings > Safari > Block Cookies and choose Always Allow, Allow from websites I visit, Allow from Current Websites Only, or Always Block. In iOS 7 or earlier, choose Never, From third parties and advertisers, or Always.
- Allow JavaScript. Tap Settings > Safari > Advanced and turn JavaScript on.
- Clear your history and cookies from Safari. In iOS 8, tap Settings > Safari > Clear History and Website Data. In iOS 7 or earlier, tap Clear History and tap Clear Cookies and Data. To clear other stored information from Safari, tap Settings > Safari > Advanced > Website Data > Remove All Website Data.
Check out Apple’s support forum for additional tips on how to keep your device safe while using Safari.