Two researchers took down the four major browsers, Internet Explorer, Firefox, Chrome, and Safari yesterday as Pwn2Own wrapped up in Vancouver.
Tag Archives: Apple
Apple Patches WebKit Vulnerabilities in Safari
Apple released new versions of Safari that patch a number of WebKit vulnerabilities.
OpenSSL: Patch for secret “high severity†vulnerability
And indeed, in order to avoid being again in the news, the OpenSSL Foundation is set to release later this week several patches for OpenSSL, fixing undisclosed security vulnerabilities, including one that has been rated “high” severity.
Matt Caswell of the OpenSSL Project Team announced that OpenSSL versions 1.0.2a, 1.0.1m, 1.0.0r, and 0.9.8zf will be released Thursday.
“These releases will be made available on 19th March,” Caswell wrote. “They will fix a number of security defects. The highest severity defect fixed by these releases is classified as “high” severity.”
OpenSSL has been hit hard and the trust in it and in open source in general has been severely shaken in the last 12 months.
Last year in April, Heartbleed (CVE-2014-0160) was discovered in older versions of OpenSSL, but still highly used, which allowed hackers to read the sensitive contents of users’ encrypted data, such as financial transactions, instant messages and even steal SSL keys from Internet servers or client software that were running the affected versions of OpenSSL.
Two month later, in June the same year, a Man-in-the-Middle (MITM) vulnerability (CVE-2014-0224) was discovered and fixed. However, the vulnerability wasn’t quite as severe as the Heartbleed flaw, but serious enough to decrypt, read or manipulate the encrypted data.
In October last year, POODLE (CVE-2014-3566) (Padding Oracle On Downgraded Legacy Encryption) was discovered in the obsolete Secure Sockets Layer (SSL) v3.0 that could allow an attacker to decrypt contents of encrypted connections to websites. When exploited, it allows an attacker to perform a man-in-the-middle attack in order to decrypt HTTP cookies. The POODLE attack can force a connection to “fallback” to SSL 3.0, where it is then possible to steal cookies, which are meant to store personal data, website preferences or even passwords.
Just weeks ago, the latest vulnerability, FREAK (CVE-2015-0204) (Factoring Attack on RSA-EXPORT Keys) was discovered in the SSL protocol that allowed an attacker to force SSL clients, including OpenSSL, to downgrade to weaken ciphers that can be easily broken. Needless to say that such a weak encryption could potentially allow them to eavesdrop on encrypted networks by conducting man-in-the-middle attacks. This time, pretty much every big software vendor was affected: Apple, with its MacOS, iPhone and iPad, Google with Android and Chrome and last but not least, Microsoft with all versions of Windows.
Due to its widespread use, OpenSSL is considered an important software project and is ranked first under the Linux Foundation’s Core Infrastructure Initiative. Because of its complexity, high usage and lack of in-depth security reviews, companies like Google, Facebook and Cisco are heavily sponsoring this project in order to avoid being again affected by long forgotten bugs.
Well, for OpenSSL seems that this is starting to pay off.
The post OpenSSL: Patch for secret “high severity” vulnerability appeared first on Avira Blog.
Stealthy, Persistent DLL Hijacking Works Against OS X
Researcher Patrick Wardle of Synack is expected this week at CanSecWest to unveil malicious dylib attacks against Apple’s Mac OS X.
Apple fixes FREAK flaw in OS X and iOS
What is FREAK?
By exploiting the Factoring RSA Export Keys vulnerability in SSL (FREAK), an attacker could intercept the network traffic between entities running any implementation of the vulnerable protocol and decrypt the secure communication. In other words, the attacker is able to act as a man-in-the-middle and decrypt the secure traffic between the client and the server.
The well known OpenSSL library, Apple’s Secure Transport, and Microsoft’s Secure Channel (which is impacting all supported versions of Windows) have all been found vulnerable to this type of attack.
 The flaw resides in the fact that the SSL/TLS encryption was forced to use a weaker cipher suite (so called “export grade”) with a 512-bit key that could be broken with today’s technology in a few hours.
The flaw resides in the fact that the SSL/TLS encryption was forced to use a weaker cipher suite (so called “export grade”) with a 512-bit key that could be broken with today’s technology in a few hours.
Apple is describing the affected area as a “Secure Transport vulnerability which allows an attacker with a privileged network position to intercept SSL/TLS connections”.
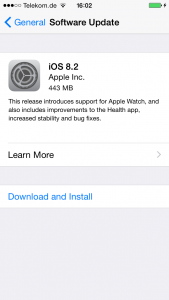
The security update 2015-002 which fixes FREAK is available for OS X Mountain Lion v10.8.5, OS X Mavericks v10.9.5, and OS X Yosemite v10.10.2.
The iOS 8.2 is available for iPhone 4s and later, iPod touch (5th generation) and later, and iPad 2 and later.
What should you do?
Apple’s security update for MacOS also includes mitigation for arbitrary code execution by leveraging flaws in iCloud Keychain recovery, IOAcceleratorFamily and IOSurface and the Kernel (OS X Yosemite).
For the iOS, Apple patched bugs in CoreTelephony, which caused the device to restart and buffer overflows in iCloud Keychain which allow an attacker with a privileged network position to execute arbitrary code.
Even if CVE-2015-1067 also known as FREAK is more theoretical than most vulnerabilities affecting the SSL protocol and its implementations (Heartbleed, Poodle), it is strongly advisable to apply the update.
Usually, the update comes over the wire, so follow the known procedures for each device to apply it:
- iOS: go to Settings ->General -> Software Update
- Go to Updates (or Software Updates for older versions) and click Update All.
The post Apple fixes FREAK flaw in OS X and iOS appeared first on Avira Blog.
How to activate Two Factor Authentication on Apple services
This February Apple announced that they would be making Two Factor Authentication available on iMessage and FaceTime in a bid to help users secure their online identities.
What is Two Factor Authentication?
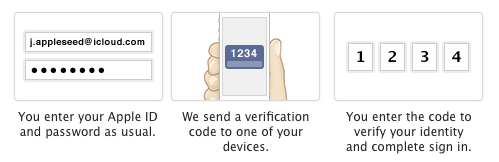
Two Factor Authentication is method of securing your online accounts or services through the addition of another layer of security when you login. This is usually a code which is sent to your mobile device, either in form of a text message or via an app.
Activating Apple’s Two Factor Authentication
Implementing Two Factor Authentication on Apple services is very straightforward.
- Go to My Apple ID.
- Select Manage your Apple ID and sign in.
- Select Password and Security.
- Under Two-Step Verification, select Get Started and follow the onscreen instructions.
For help and advice on implementing Two Factor Authentitcation on Apple services, I’d recommend visiting the official Apple FAQ page.
Google Adds Grace Period to Disclosure Policy
Google announced that it was adding a 14-day grace period to its 90-day vulnerability disclosure deadline if the affected vendor says it will have a patch ready inside the extension.
Threatpost News Wrap, January 30, 2015
Dennis Fisher and Mike Mimoso discuss the Ghost glibc vulnerability and its repercussions, the Apple iOS and OSX patches, the link between the Regin APT platform and the NSA. Plus Super Bowl predictions!
Unpatched Apple Vulnerabilities Latest Google Project Zero Disclosures
Three unpatched Apple OS X vulnerabilities were disclosed by Google’s Project Zero research team. Project Zero discloses if a bug is not patched within 90 days of reporting it to the affected vendor.
Thunderstrike! How a radar-proof rootkit could infect your Mac
A security researcher describes how malware could infect your Mac’s boot ROM, and spy on your activities, with little chance of you ever realising.
The post Thunderstrike! How a radar-proof rootkit could infect your Mac appeared first on We Live Security.