The InterContinental Hotels Group has revealed that 12 of its hotels suffered a data breach between August and December last year.
The post InterContinental Hotels Group confirms suspected data breach appeared first on WeLiveSecurity
![]()
The InterContinental Hotels Group has revealed that 12 of its hotels suffered a data breach between August and December last year.
The post InterContinental Hotels Group confirms suspected data breach appeared first on WeLiveSecurity
![]()
Keep your WordPress site updated, or risk having hackers modify the content of any post or webpage.
The post 100,000+ WordPress webpages defaced as recently patched vulnerability is exploited appeared first on WeLiveSecurity
![]()
Strategic cybersecurity the key to keeping the threat of cyberattacks at bay, a new report states.
The post Strategic cybersecurity will stymie ‘expanding threat landscape’ appeared first on WeLiveSecurity
![]()
A significant number of US citizens have experienced a data breach and are concerned over the security of their personal information, a study reveals.
The post Over half of US citizens ‘have experienced a data breach’ appeared first on WeLiveSecurity
![]()
A new way of looking at cybersecurity, no longer viewing it as a goal in itself, but instead something that is directly connected to business needs.
The post Cybersecurity: 5 basic lessons for everyone appeared first on WeLiveSecurity
![]()
Phishing – a hacking technique using fraudulent emails to trick people into handing over their bank account details – continues to be a major threat to personal security. Because these techniques are so successful, criminal continually refine them, making it harder than ever to avoid them.
Fortunately, there are a few steps you can take to better protect yourself – and they are all quite simple.
Phishing emails are so effective because it is very hard to tell them apart from the real thing – they look just like the emails your bank sends. They are also intended to scare you, suggesting that your account has been compromised and you must act immediately to protect yourself.
No matter how concerned you may be, you should never click the links in an email. Even if you are 100% certain that the message comes from your bank.
Instead, you should type the bank’s address yourself into the browser window to make sure you are visiting the correct website. Once successfully logged in, you will be able to access electronic versions of the messages your bank has sent you – including any alerts. If the message is not repeated here, you can safely assume that the email was fraudulent.
You should also bear in mind that all banks typically send printed letters through the post when there is a serious problem with your account.
All of the banks provide guidance on what a real email looks like – here’s an example from Lloyds Bank. Take a few minutes to acquaint yourself with the information provided and you’ll save yourself a lot of stress in future.
And just to re-emphasise the importance of never clicking links in an email, here’s what Lloyds has to say;
“We never link directly to our Internet Banking log on page, or a page that asks for security or personal details.”
Computer security software, like Panda Gold Protection, include tools to identify and block phishing emails before you can be tricked by them. It is absolutely essential that every PC, Mac and Android smartphone you own is protected by some form of security software to stop phishing (and other cyberattack techniques) compromising your devices.
Once installed, don’t forget to carry out a regular scan (once a week is ideal) to check to see whether any malware or viruses have breached your defences. Malware can be just as damaging as a phishing email, monitoring what you do on your computer, and stealing passwords for instance. Running a regular scan will give you a chance to identify and delete these malicious apps before you are too badly compromised.
Protecting against phishing emails is generally just a case of using your common sense. No matter how scary an email looks, take a second to check your online account yourself. Don’t forget that you can always visit your local branch, or the phone banking service to confirm that everything is ok.
Take the first step towards protecting yourself against phishing emails by downloading a free trial of Panda Security now.
The post How to prevent phishing appeared first on Panda Security Mediacenter.
A recent indie horror film called It Follows explores an interesting moral grey area. In that film a shape-shifting creature slowly but unstoppably chases a victim. This victim -who faces the inevitable prospect of being worn down and caught- can pass on this curse to someone else by sleeping with them. The question the film poses: Would you sacrifice someone else in order to save yourself?
A recently discovered type of malware is, strikingly, asking internet users the very same question in a real world setting. The context is admittedly far less grandiose –replace shape-shifting monsters with computer hackers- though the name of the new type of malware certainly feels like an allusion to its worthiness as a cyber suspense thriller.
Popcorn Time Ransomware, which is named after but unrelated to a bittorrent client, encrypts the contents of your computer or device (using AES-256 encryption) so you cannot access them. Then it gives you a choice; you can pay a ransom, or sell out people you know.
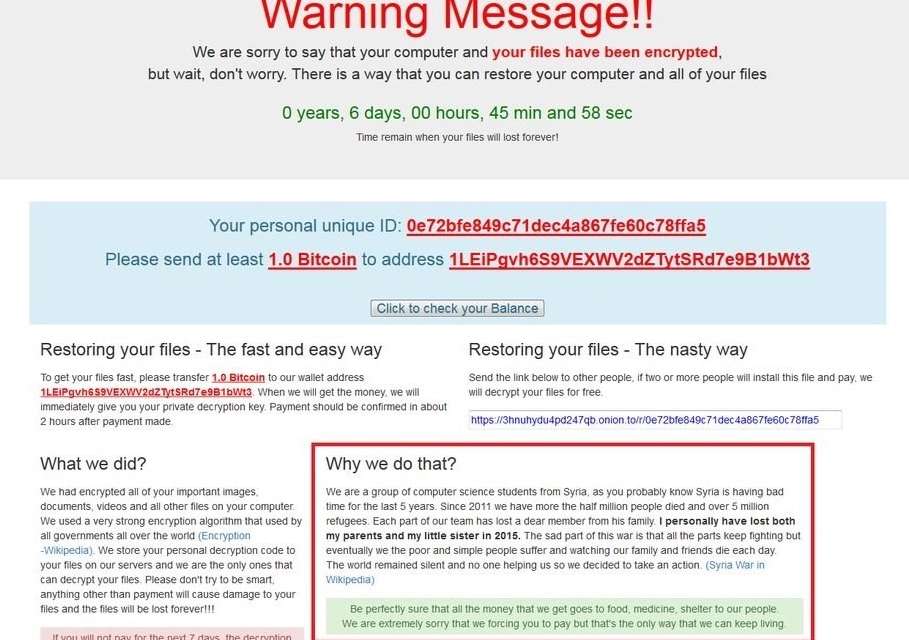
MalwareHunterTeam, who discovered the new ransomware, have reported cases where victims have been given the ability to restore their files for one bitcoin (worth roughly $770 and £610). The second option though, described by its anonymous developers as “the nasty way”, is to send the link on to other people. “If two or more people install this file and pay, we will decrypt your files for free,” the developers say.
If that wasn’t surprising enough, a read of the developers’ information on the ransomware message throws yet another curveball at the infected computer’s owner. The money you are forced to send will, the infectors say, be used as charity.
The Popcorn Time ransomware developers claim to be computer science students living in war-torn Syria. Due to their horrific circumstances, living with the death of friends and relatives and “with no one helping”, they claim, they are taking things into their own hands. “Be perfectly sure that the money we get goes toward food, medicine and shelter to our people,” they say before actually apologizing for their actions. “We are extremely sorry we are forcing you to pay but that’s the only way we can go on living.” There is, of course, no way to verify this information and it may be completely untrue.
A general rule though is that backing up important files regularly to an external hard drive or cloud storage keeps you one step ahead of any potential attackers. It is also best to download only from reputable sources and be wary of email links that could be part of a phishing attack.
Fear of hackers using our devices to spy on us has long been a fascination in Hollywood. As far back as 1983 the film WarGames explored the realm of computer hacking. Much has changed since then. Hackers have been vilified as well as championed in popular culture; Mr Robot is part of an anti-establishment organization, whilst the popular, hacker founded, Icelandic Pirate Party are making use of a Robin Hood trope to describe their political stance.
The post A New Ransomware Is Testing Our Morality appeared first on Panda Security Mediacenter.
The IT threat landscape has changed dramatically over the last three-four years.
With no shortage of threat actors, from hacktivists to nation-states, criminals to terrorists, all of them are now after something new.
It’s no more just about stealing your money, credit cards and defacing websites, as now they are after the intellectual property, mass attacks and most importantly, our critical
![]()
Cybercrime is victimizing US companies and consumers, but a gap in cybersecurity skills presents a problem for the federal government. ESET’s Stephen Cobb investigates.
The post Desperately seeking cybersecurity skills appeared first on WeLiveSecurity
![]()
Many businesses are actively encouraging their employees to use social media at work, hoping that they will become “brand advocates”, talking about the company’s products and services. Employers also hope that their worker’s accounts will help to give the company a “human” face.
But as good as these intentions are, you should carefully consider whether you really want to use your social media accounts at work. Because there are a few potential issues to be aware of.
Social media is a brilliant tool for sharing links, videos and interesting information with your friends online. But not all those links go to good places – quite often those pages will have adware, malware or computer viruses lurking in the background, trying to download themselves onto your computer.
If malware does install itself on your work computer, it could cause serious damage to the rest of the network. The time and costs associated with fixing these issues could seriously hurt your company – and maybe even lose you your job, even if it was an accident.
There are dozens of examples of situations where someone has made a joke online, but one of their followers has taken offence. The issue quickly escalates, as strangers offer criticisms – and sometimes even threats.
The fall-out from these incidents also affects that person’s employer – some people wrongly assume that the individual and their company are inextricably linked. So the company must act to regain control of the situation – including sacking the employee involved.
With so much interesting information available on Facebook, Twitter, Instagram etc, it is very easy to spend hours catching up on what people are sharing. But if you spend too long on non-work related tasks, you will run into problems getting your actual work done.
When the quality of your work starts to decline, you could be disciplined by your employer – and potentially sacked if things go too far.
Before you start using your personal social media accounts at work, you should have a conversation with your boss. You should ask how your employer expects you to behave:
It is only by establishing these guidelines up front that you can hope to avoid accidentally breaking one of them, risking your job. By being smart, both you and your business avoid trouble and gain the benefits offered by social media.
The post The risks of using personal social media at work appeared first on Panda Security Mediacenter.