Potentially 600m Samsung Galaxy phones are at risk of malicious compromise after a new exploit was discovered by a security researcher.
The post New exploit compromises Samsung Galaxy phones appeared first on We Live Security.
![]()
Potentially 600m Samsung Galaxy phones are at risk of malicious compromise after a new exploit was discovered by a security researcher.
The post New exploit compromises Samsung Galaxy phones appeared first on We Live Security.
![]()
Egor Homakov made it actually happen. In his blogpost he describes how he managed to find a way to generate an unlimited amount of money on Starbucks gift cards.
If you are like me the only thing you want to know now is “HOW?!” (and your second thought will probably be: I want this so bad!). So let me curve your enthusiasm right now: Homakov of course did the right thing and reported the exploit to Starbucks.
Now back to topic! What the security expert did was to use a vulnerability called “race condition”. He bought three Starbucks card for $5 each and tried to use the vulnerability to transfer money between the cards without it being deduced.
“So the transfer of money from card1 to card2 is stateful: first request POST /step1?amount=1&from=wallet1&to=wallet2 saves these values in the session and the second POST/step2?confirm actually transfers the money and clears the session”, Homakov writes and continues: “After 5 failed attempts I was about to give up. Race condition is a kind of a vulnerability when you never know if the app is vulnerable, you just need to try some more. […]But yeah, the 6th request created two $5 transfers from wallet1 with 5 dollars balance. Now we have 2 cards with 15 and 5 (20 in total).”
The only thing left to do was to buy something with this money in order to deliver the proof of concept. One chicken sandwich, a few bottles of water, and some gum later the new balance on his cards was $5.70.
Starbucks was pretty unhappy with the stunt despite Homakov adding the $10 to his account from his credit card and disclosing the bug immediately. They might have been even unhappier though, if a lot of hungry and coffee addicted customers would have abused the system …
The post Unlimited Free Coffee at Starbucks? A Hacker Made It Happen appeared first on Avira Blog.
This vulnerability is affecting all previous versions and can be leveraged via the comment section of a website running WordPress, by hiding malicious code that is executed on the server.
An attacker exploiting the flaw can execute arbitrary code on the server, create new administrator accounts, or make changes with the same privileges as the currently logged-in admin.
The bug is very similar to the one patched in 4.1.2.
The problem with this bug resides in the way WordPress stores the large comments (more than 64k): such comments are truncated when stored in the database, resulting in malformed HTML being generated.
Now one might ask why someone would allow a 64K comment in the first place. But, since it is allowed to comment in HTML, the full HTML is stored in the database.
If you add some formatting to the comment, the 64K can be consumed rather quickly.
By setting up special attributes of the supported HTML tags, the attacker can hide a short malicious JavaScript code in the comment and execute it without any visible sign when the administrator viewed it in the Dashboard before approving it.
As an immediate reaction to this exploit, WordPress 4.2.1 has begun to roll out as an automatic background update, for sites that support those.
You can also download WordPress 4.2.1 manually or update over to Dashboard → Updates and simply click “Update Now”.
For more information, see the release notes.
The post WordPress 4.2.1 Patches Zero-Day exploit appeared first on Avira Blog.
Biohacking or wetware hacking is the practice of engaging biology with the hacker ethic. It encompasses a wide spectrum of practices and movements one of which are the “grinders” who design and install do-it-yourself body-enhancements such as magnetic implants.
It sounds rather “out there”, right? But it apparently isn’t, as Wahle decided to demonstrate. You only need a good stomach. In order to show that an implanted NFC chip can be sneaked passed scanners at the airport and other high-security locations, he had to not only acquire a chip designed to normally be injected into cattle but also needed to use a needle that was rather big and made him want to vomit.
Said chip has a NFC (Near Field Communications) antenna which pings Android phones that are in close vicinity and then asks them to open a link. If followed, the link will lead to a malicious file which, once installed, will establish a connection to a remote computer from which the owner can carry out further exploits. With the right amount of social engineering this could become a real danger.
“In Miami, Wahle and Soto are planning to detail the steps hackers will need to go through to add implants to their arsenal, including how to acquire the hardware and program the chip. Could this be the beginnings of the democratisation of malevolent biohacking?” writes the Forbes magazine in its article. And security consultant Rod Soto adds: “This is just the tip of the iceberg … anyone can do this.”
The post Hackers Could Exploit Phones With an Implanted NFC Chip appeared first on Avira Blog.
iOS and OS X the most vulnerable operating systems? Don’t confuse vulnerabilities with exploits, or patch frequency with insecurity.
The post Operating System Vulnerabilities, Exploits and Insecurity appeared first on We Live Security.
An automated attack targeting users of the open source Rejetto webserver and file-sharing application tried to inject the IptabLes DDoS tool.
In this post we want to share with you a question that arose from the first post in this series: whether exploits are the same as malware. What are we talking about? The best way to debunk any myth is to start by understanding what it is we are talking about.
The post Myths about malware: an exploit is the same as malware appeared first on We Live Security.
![]()
Reports of the first in-the-wild exploits targeting the Bash vulnerability have surfaced, as have complaints the first patches for the bug are incomplete.
After an analysis of a payload distributed by Rig Exploit kit, the AVAST Virus Lab identified a payload as Tinba Banker. This Trojan targets a large scope of banks like Bank of America, ING Direct, and HSBC.
 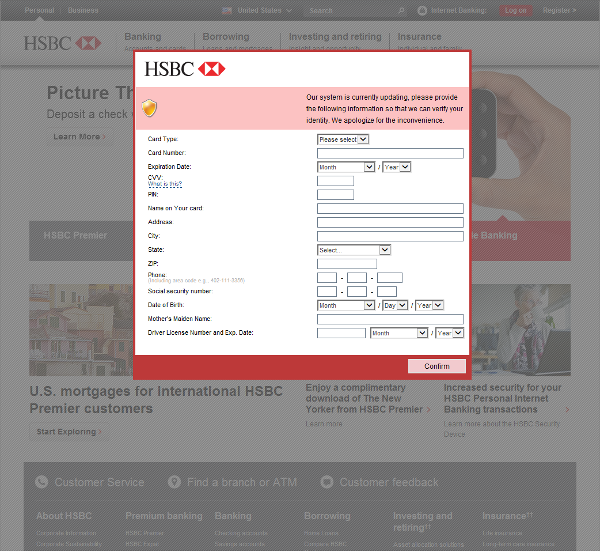
In comparison with our previous blogpost, Tinybanker Trojan targets banking customers, this variant has some differences,  which we will describe later.
The example of an injected form targeting Wells Fargo bank customers is displayed in the image below.
Differences from the Czech campaign
In the case of the Tinba “Tiny Banker” targeting Czech users, the payload was simply encrypted with a hardcoded RC4 password. However, in this case, a few more steps had to be done. At first, we located the folder with the installed banking Trojan. This folder contained an executable file and the configuration file – see the next figure for the encrypted configuration file.
At first, XOR operation with a hardcoded value 0xac68d9b2 was applied.
Then, RC4 decryption with harcoded password was performed. After RC4 decryption, we noticed AP32 marker at the beginning of the decrypted payload, which signalized aplib compression.
Therefore, after aplib decompression, we got the configuration file in plaintext. After studying this roughly 65KB long plaintext file, we noticed that it targets financial institutions worldwide.
Targeted financial institutions
 Screenshots of targeted banks
Conclusion
Keep your software up-to-date. Software updates are necessary to patch vulnerabilities. Unpatched vulnerabilities open you to serious risk which may lead to money loss. For more protection, use security software such as avast! Antivirus with Software Updater feature. Software Updater informs you about  updates available for your computer.
SHA’s and detections
Exploits
CC0A4889C9D5FFE3A396D021329BD88D11D5159C3B42988EADC1309C9059778D
1266294F6887C61C9D47463C2FE524EB1B0DA1AF5C1970DF62424DA6B88D9E2A
Payload
856E486F338CBD8DAED51932698F9CDC9C60F4558D22D963F56DA7240490E465
88F26102DB1D8024BA85F8438AC23CE74CEAE609F4BA3F49012B66BDBBE34A7B
avast! detections: MSIL:Agent-CBZ [Expl], SWF:Nesty-A [Expl], Win32:Banker-LAU [Trj]
Acknowledgement
This analysis was done collaboratively by David Fiser and Jaromir Horejsi.
Thank you for using avast! Antivirus and recommending us to your friends and family. For all the latest news, fun and contest information, please follow us on Facebook, Twitter and Google+. Business owners – check out our business products.