Stop by for a visit with Avast; booth 5K29.
New mobile apps, a live Wi-Fi hack, results of a global Wi-Fi experiment, a demonstration of mobile malware, and Avast mobile experts can all be found at Avast’s booth (hall 5 stand 5K29) at this year’s Mobile World Congress in Barcelona.
Open Wi-Fi Risks and Live Demonstration
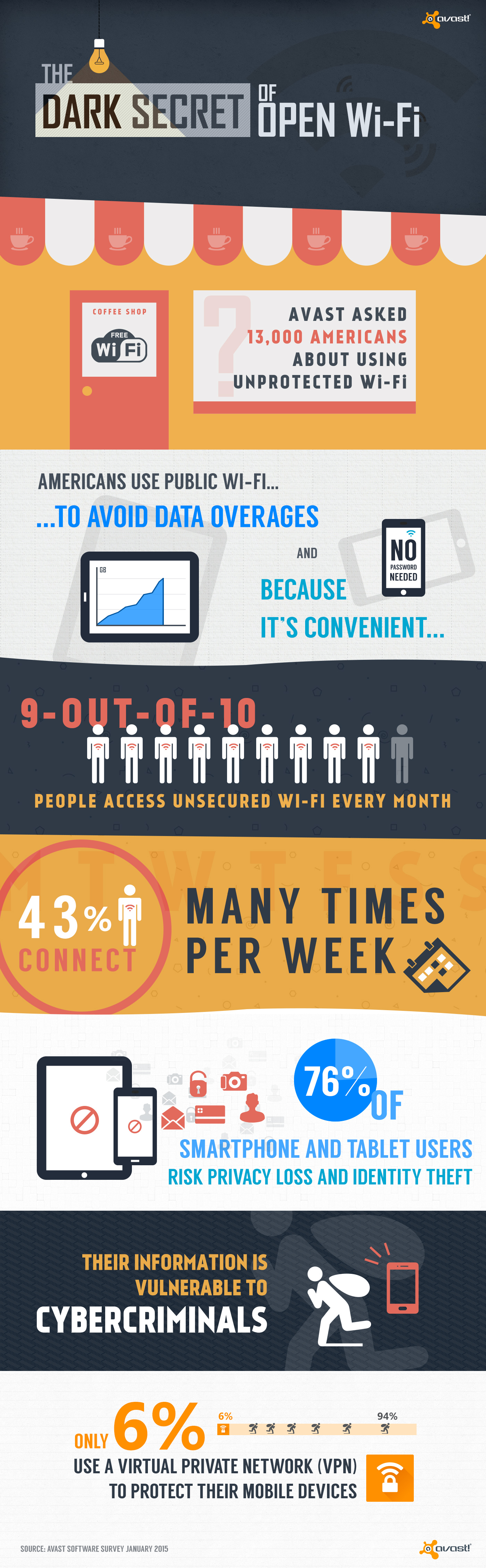
Connecting to public Wi-Fi networks at airports, hotels, or cafes has become common practice for people around the world. Many users are, however, unaware that their sensitive data is visible to hackers if they don’t use protection. This data includes emails, messages, passwords and browsing history – information you don’t necessarily want the guy sipping the latte next to you at the cafe to see. Avast experts traveled to different cities across the U.S., as well as Europe and Asia, to find out how much information is openly shared via public Wi-Fi. They found that one-third of browsing traffic in New York City, San Francisco and Chicago is openly visible for hackers.
At the Congress, Avast will conduct a Wi-Fi hack demonstration. The demonstration will allow visitors to see, first hand, what a hacker can access if they don’t use protection. Participants can connect to Avast’s (password protected) Wi-Fi network to browse and send messages as they normally would when connected to open Wi-Fi. To demonstrate how this information would look through the eyes of a hacker, their activities will be displayed on a screen at the Avast stand.
Mobile Malware and Simplocker Demonstration
Mobile malware is often perceived as a myth, yet Avast currently has more than one million samples of mobile malware in its database. Avast recently discovered a new variant of the mobile ransomware, Simplocker, which will also be demonstrated during the Congress. Visitors can see how the malware disguises itself, behaves, and will learn how they can protect themselves.
Introducing Avast’s New Suite of Apps
Avast will be introducing a suite of new apps at this year’s Mobile World Congress, including productivity and security apps for Android and iOS. Avast GrimeFighter and Avast Battery Saver address two of the most common complaints for Android users: storage concerns and battery life. Avast GrimeFighter helps users free extra storage on their devices by identifying unimportant data for one-tap removal, while Avast Battery Saver extends battery life up to 24 hours by learning the user’s behavior and optimizing features to preserve battery power.
Avast SecureMe is a dual solution app that helps iOS users identify secure Wi-Fi connections and protect personal data while using public Wi-Fi connections.
Wi-Fi Security, a feature available in Avast SecureMe, and coming soon to Avast Mobile Security for Android, prevents users from falling victim to Domain Name Server (DNS) hijacking by exposing vulnerabilities in routers they want to connect to.
We look forward to meeting you!
If you are attending this year’s Mobile World Congress, feel free to stop by the Avast booth to speak with Avast experts, learn more results from Avast’s global Wi-Fi experiment, see Avast’s new mobile apps and participate in the Wi-Fi demonstration. If you aren’t attending, make sure to check our blog, follow us on Twitter and Instagram, and like us on Facebook for updates during the Congress!
Note to media: If you would like to set up a meeting with Avast, please email [email protected].