US newspaper The New York Times has published a fascinating news story about what could be the largest bank robbery in history. According to the article, the thieves have stolen at least $300 million but this figure could be triple that amount, reaching almost $1 billion.
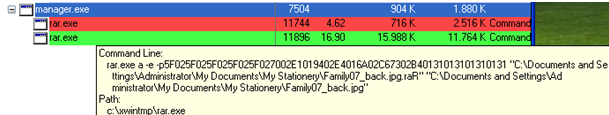
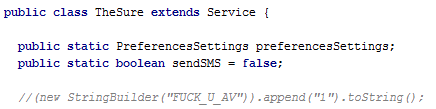
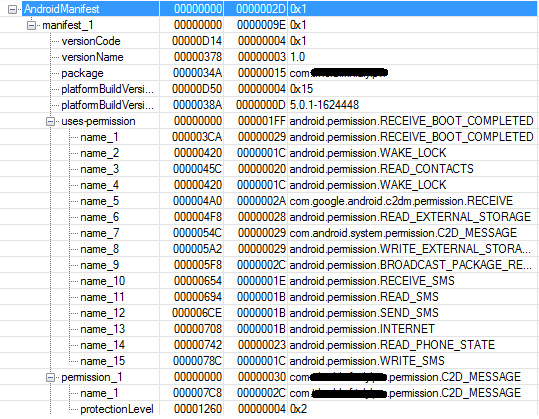
In order to carry it out, the thieves used malware to infect employees’ computers, compromise them and give the cyber-criminals access to the internal network. In this way the attackers studied the internal functioning of the bank’s daily routines, so that the transfers they planned to make did not attract any attention and blend in with the normal daily operations.
Today a report will be published that will clarify some of the questions surrounding the attack. I was struck by the way the article begins, with what seems like the beginning of a Hollywood story: an ATM in Kiev started “spitting out” cash without anyone touching it.
The most surprising aspect is not the act itself. A cash machine is just a computer and attacking it so that it can obey commands not given by the bank is perfectly possible. However, if one thing does not make sense, it is that the criminals even bothered to carry out this attack when they are capable of stealing millions of dollars without attracting any attention using transfers.

The answer to this mystery is simple. It is not a robbery but hundreds of them. Multiple banks from different countries are victims of the attack and in each one they have carried out the attacks that best adjusted to the level of comprise they achieved, according to what they were able to access, etc. In those in which they were able to carry out transfers and send money abroad, that is what they did. If they could not do this but were able to hack the cash machines, they took the money in this way.
Time to get serious
Cyber-criminals have compromised 100 banks in 30 countries. According to the information published so far, some employees received emails that infected their computers with malware. Once a computer has been compromised it is relatively easy –for them at least– to move across the internal network, compromising more computers and gaining access to all of the resources they need. When they had control of the key computer, they installed a Trojan which gave them full access to it.
In the light of the data published, it is clear that the losses that a robbery like this can generate are huge, and it is very noteworthy that an attack of this kind had gone unnoticed for so long (they had been working on it since the end of 2013). The banks I know take security very seriously. I have no doubt that they all had some kind of security solution installed and a team to make sure that it was operating correctly. Neither do I doubt that it was insufficient, although that is easy to say when we have just seen the magnitude of the attack.
What should they do? Is there any way to stop all of these attacks? No system is perfect or 100% attack proof. However, there are some measures that are relatively easy to implement that significantly increase security, preventing attacks like this.
Firstly, in a bank it is very debatable that any employee should be able to install and run (consciously or not) any software that has not been previously approved by the security team. Simply preventing the installation of unauthorized software will eliminate the majority of attacks carried out.
Remember that this attack has been described by a representative of the company investigating it as “one of the most sophisticated attacks the world has seen to date”, and the attackers still needed to send an email and an employee to open it and run the attachment (or click on a link).
You might think that the attack could have used an unknown vulnerability to compromise the computer, which has been done in the past and is perfectly plausible. In this case, simply visiting a website could compromise the computer. However, if you have a system that monitors the behavior of the processes running on each computer, these types of attacks can be detected. If the browser process, for example, downloads and tries to run an unknown program, automatically block it and problem solved.
Some readers could think that if it were that easy all large companies would use this type of system, if not on all computers at least on those that can access critical data and should be well protected. Unfortunately, there are very few solutions of this type on the market. Whitelisting-based applications, which basically only allow known files to be run, are very awkward to use in the day to day and on top of that, once they let a process run (the Internet browser, for example), they do not monitor it.
What is left? Well, from my 16 years of experience in the IT security world I can assure you that it is time to get serious. We must forget about fear and back disruptive technology that allows us to control everything that happens on our networks. They must be flexible enough to give me the option to “lock down” the network and not allow anything unknown to be installed or run, or to be a little more open provided that we have timely information on what is happening in the network.
This set of technologies and services, which we have been working on for more than 2 years, is available with Panda Advance Protection Service.
With the information that I now have on what is the largest bank robbery in history, I can say that if any one of the 100 banks affected had used Panda Advance Protection Service, they would have been protected and the attackers would probably not have been able to steal a penny.
The post The largest bank robbery in history appeared first on MediaCenter Panda Security.













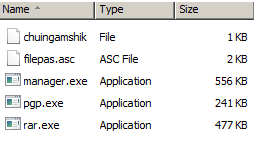 5 new files are created:
5 new files are created: