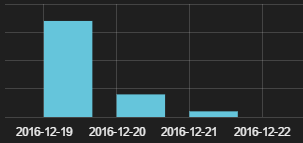
Safeguarding your company’s confidential information, in many cases, calls for having your employees create and properly manage a series of passwords. Not only should they choose complex credentials, but they should also vary among themselves. And they definitely should not be saved in easily accessible places, like a text document.
Password managers come in handy in this task that is so indispensable to corporate security. For their part, companies that have Apple devices for their employees have the Keychain as an ally: it is a password manager in the cloud that makes things really easy when defending corporate privacy via robust password selection.
Activating this tool is simple: just go to iCloud Settings from an iPhone or an iPad and activate the Keychain option. From a Mac you go to the “System Preferences” menu.
Once activated, all the passwords used by the employee will be stored in iCloud, with its own encryption. Once uploaded to the cloud, it will be possible to use those credentials on all devices that are synchronized and authorized to do so.
However, the Apple Keychain is much more than just a place to store passwords in the cloud. In fact, it allows users to completely forget about the clutter of having several passwords since, when they sign up for the service, the keychain suggests complex and distinct options to those already used and automatically saves it. No need to commit anything to memory.
It is also possible to store credit card data and certificates to sign documents digitally. Thus, Apple encryption and its cloud service are one hundred percent responsible for security on the platforms used by employees.
By combining this tool with the right protection to avoid threats, your company’s confidential information will be safer. It makes sure that your passwords are secure and that they will not be stored remotely in any place. And those who want to spice up their passwords can still edit them (or delete old ones) to make them even more complex. When corporate security is at stake, it can never hurt to add extra layers of protection.
The post Keychain, Apple’s Cloud-Based Tool That Safeguards Your Data appeared first on Panda Security Mediacenter.