As a malware analyst, I find new pieces of malware day in and day out. In fact, I see so many new malware samples that it’s difficult for me to determine which pieces would be really interesting for the public. Today, however, I found something that immediately caught my attention and that I thought would be interesting to share.
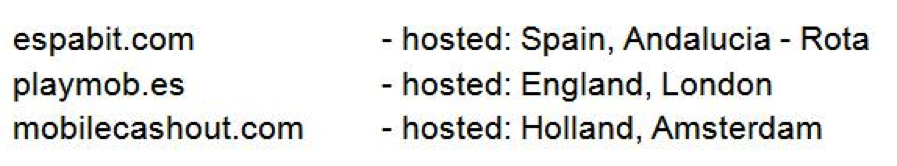
The three URLs listed above are websites that offer mobile monetizing kits, which are advertising kits that developers can implement in their mobile apps. The goal for developers is to monetize from advertisements. If a user clicks on one of the ads delivered by one of the above listed providers, he may be lead to a malicious subdomain.
The most visited of the three URLs is Espabit. According to our statistics, we know that Espabit’s servers get around 150,000 views a day and nearly 100% of the views are from mobile devices. This may not seem like that much compared to the number of Android users there are in the world, but it is still a considerable number. Espabit is trying to position themselves as a world leader in advertising, and their website may appear innocent, but first impressions can be deceiving.
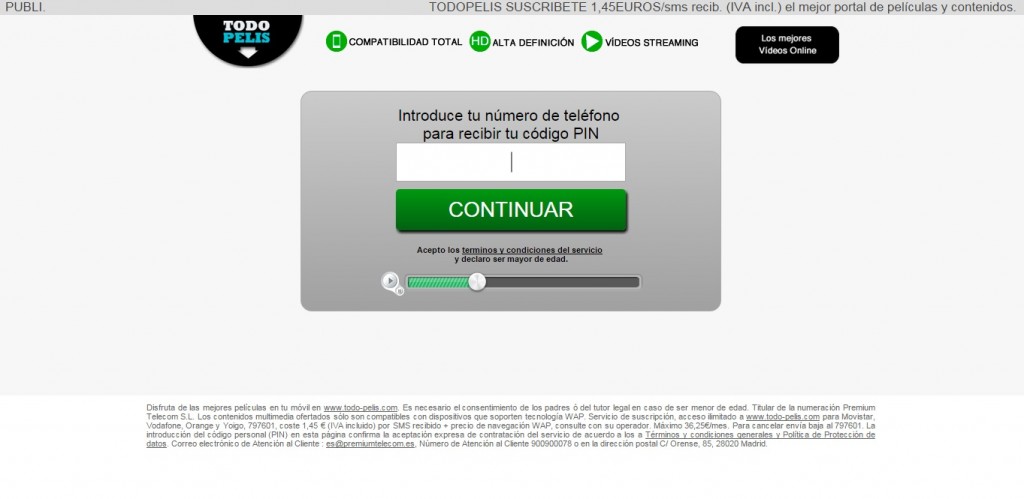
The most visited Espabit subdomain, with more than 400,000 views during the last few months, leads app users to pornographic sites via the ads displayed in their apps. The site displays a download offer for nasty apps (no pun intended) that have malicious behavior.

The above is just one example of the malicious links; there are many others hosted on the same server. The majority of the links lead to pornography or fake apps that all have one thing in common: They all steal money from innocent users.
How do they convince people to download their app? By posing as official Google Play apps. The apps are designed to look like they are from the official Google Play Store – tricking people into trusting the source. Since Android does not allow users to install apps from untrusted sources, the sites offer manuals in different languages, like English, Spanish, German, and French, explaining how to adjust Android’s settings so that users can install apps from untrusted sources, like these malicious apps. How considerate of them.
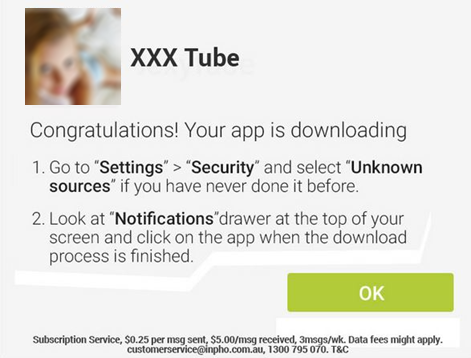
Now let’s take a deeper look at what the apps are capable of doing:
All of the “different” apps being offered by the three sites listed above are essentially the same in that they can steal personal information and send premium SMS. So far, we know about more than 40 of them stored on the websites’ servers. Most of the apps are stored under different links and, again, are offered in different languages (they want everyone to be able to “enjoy” their apps). The goal behind all of the apps is always the same: Steal money.
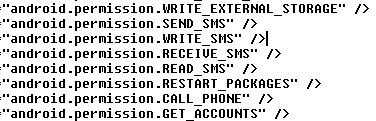
Some of the permissions the apps are granted when downloaded…
Once you open the apps, you get asked if you are 18 or older (they are not only considerate in that they offer their product in various languages, but they also have morals!).
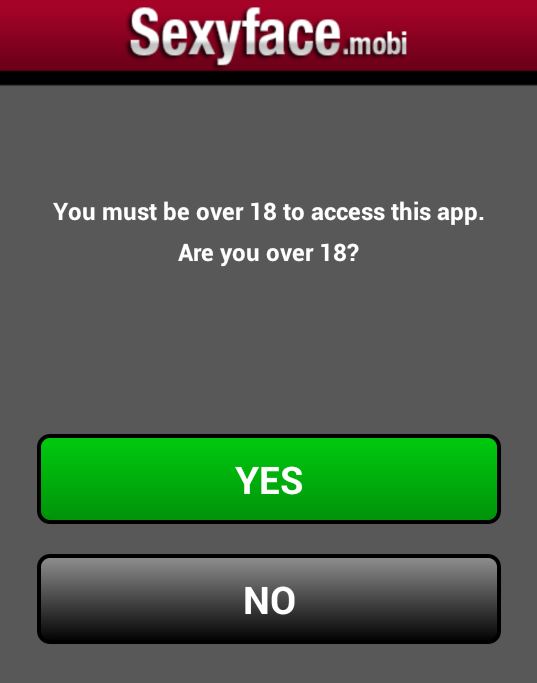
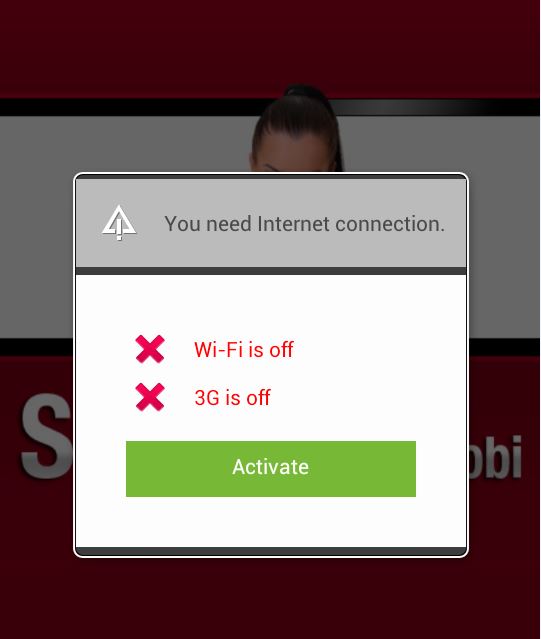
After you click on “YES” you are asked to connect your device to the Internet. Once connected to the Internet your device automatically starts sending premium SMS, each costing $0.25 and sent three times a week. That’s all the app does! The amount stolen a week does not seem like much, but that may be done on purpose. People may not notice if their phone bill is $3.00 more than it was the month before and if they don’t realize that the app is stealing money from them and don’t delete the app it can cost them $36.00 a year.
This malware is actually not unique in terms of the technique it uses. However, collectively, the three websites have around 185,000 views daily, which is a lot considering there is malware stored on their servers. Not everyone is redirected to malware, but those who are, are being scammed. Considering that the most visited malicious subdomain had around 400,000 views in the last quarter, it tells us that a large number of those visitors were infected. This means these ad providers are making a nice sum of money and it’s not all from ad clicks and views.
Although many mobile carriers around the world block premium SMS, including major carriers in the U.S., Brazil, and the UK, this case should not be taken lightly. These malware authors use social engineering to circumvent Google’s security and target innocent app users via ads. Think of how many apps you use that display ads, then think of all the valuable information you have stored on your phone that could be abused.
All malicious apps we found and described here are detected by Avast as:
Android:Erop-AG [Trj]
Android:Erop-AJ [Trj]|
Android:Erop-AS [Trj]
Some of SHA256:
DBEA83D04B6151A634B93289150CA1611D11F142EA3C17451454B25086EE0AEF
87AC7645F41744B722CEFC204A6473FD68756D8B2731A4BF82EBAED03BCF3C9B
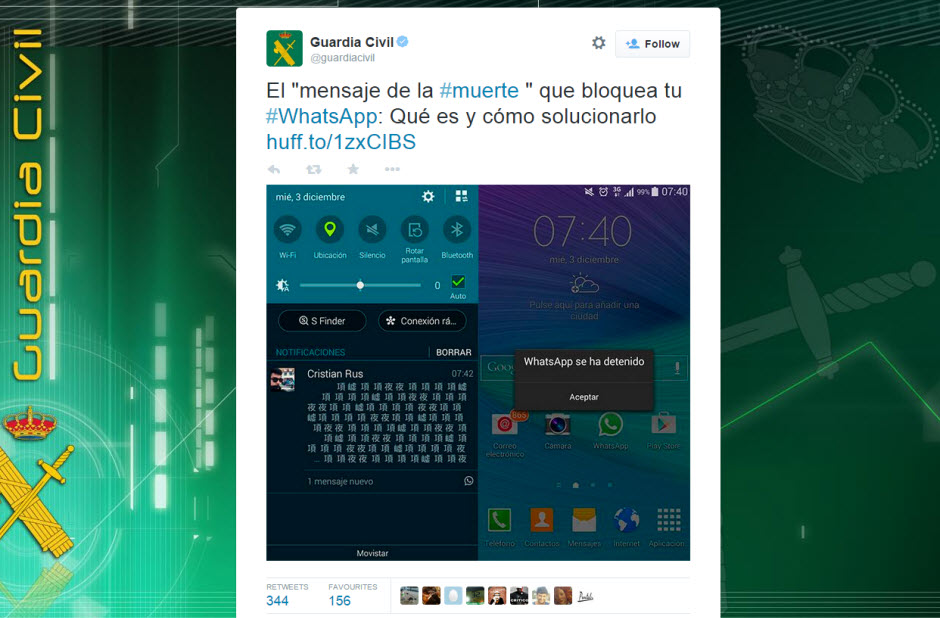
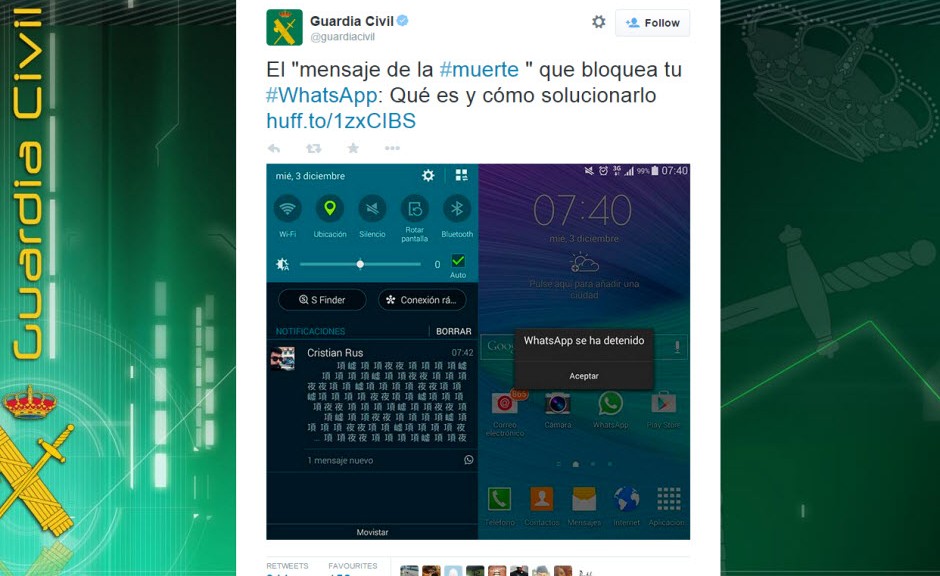











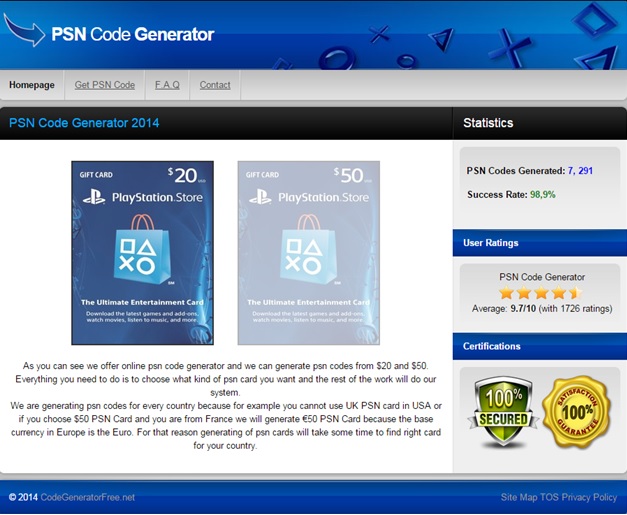
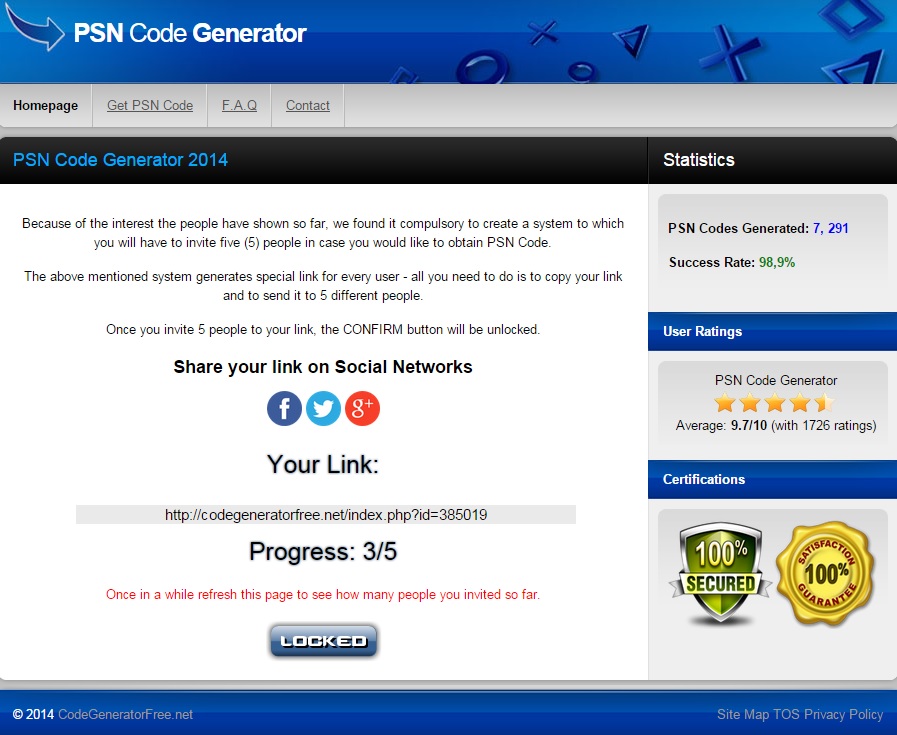
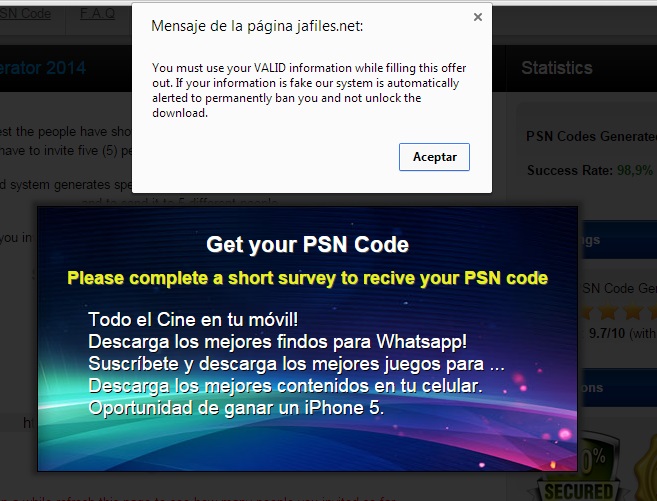
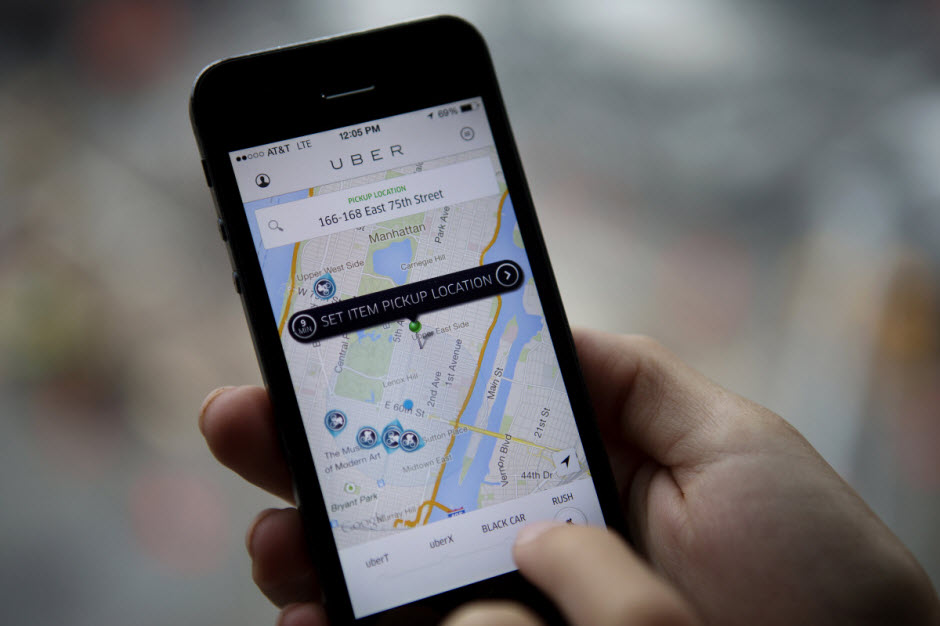 The emergence of Uber has put taxi drivers around the world on red alert. Just this week, the Spanish High Court has ordered the company to cease operations on the grounds of unfair competition with taxi drivers.
The emergence of Uber has put taxi drivers around the world on red alert. Just this week, the Spanish High Court has ordered the company to cease operations on the grounds of unfair competition with taxi drivers.


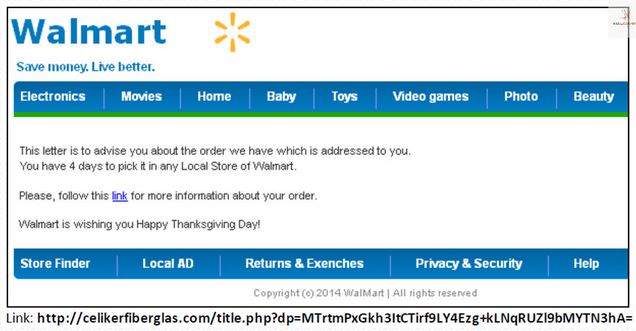
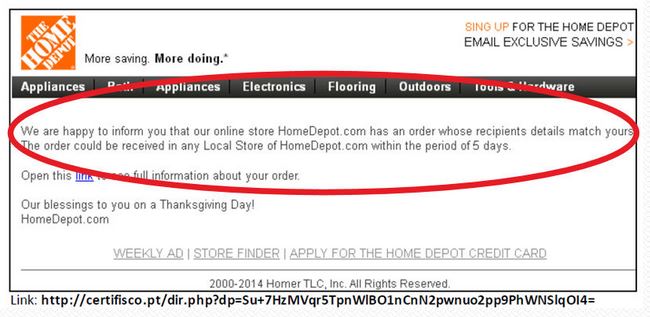
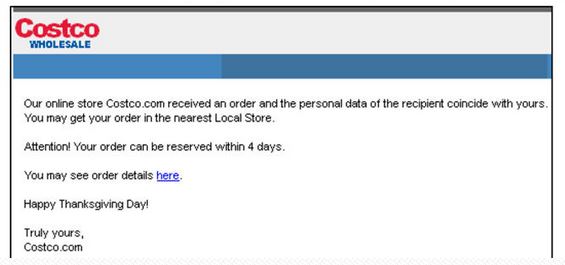
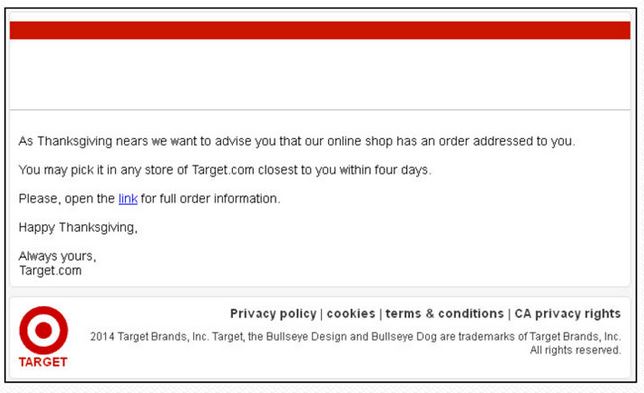
 Many of us now prefer to shop online: you can avoid the queues, it’s easier to compare goods and prices…
Many of us now prefer to shop online: you can avoid the queues, it’s easier to compare goods and prices…