Malware creation continues to break records on an international level, as proven with the data from Q1 of 2016. Experts are identifying new malware samples every day that endanger the internet security on all of our devices.
Our day-to-day lives are effected, if not immersed, in unprecedented technological changes. As the world continues to become more digital, our personal and work environments continue to be susceptible to the +227,000 new threats that lurk on the internet. Although our online habits continue to change and reflect these developments, we must remember that technology also opens the door for extremely aggressive cyber-attackers who are financially motivated. But, if we take preventative and adequate security measures, we will be able to protect ourselves from financial harm.
Panda Security would like to accompany our users in their digital transformation by offering solutions for a wide variety of devices and for different budgets; let’s work together to prevent, detect, and remove any kind of malware that is trying to sneak into your computer (and your bank account). Taking care of our computers’ “health” is the best way to save money… don’t wait until it’s too late! Tools like our Panda Cloud Cleaner are the best for working against cyber-crime.
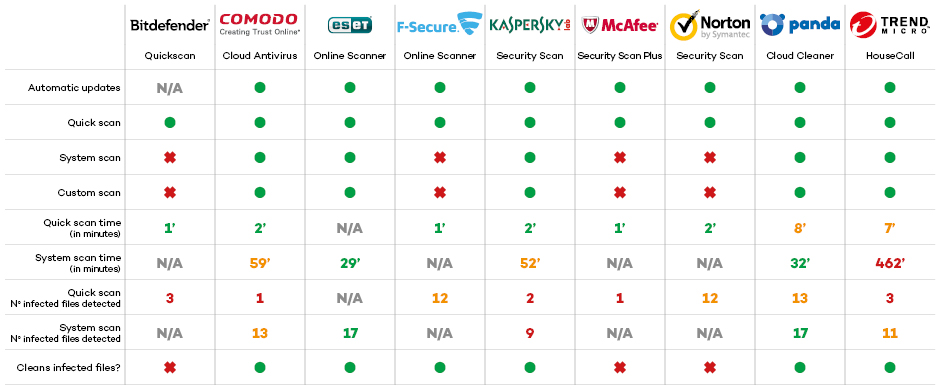
In a recent test comparison, Panda Cloud Cleaner has proven to be one of the best free anti-virus tools in the market. Among the number of solutions tested and analyzed, Panda Cloud Cleaner was rated as outstanding in analysis modes (it is both fast and complete), and was able to eliminate all malware without having to install another anti-virus tool.
As you can see, Panda Security’s solution is rated as one of the most effective solutions for detecting and disinfecting malware.
Businesses maximize their profits by taking advantage of the newest technology and latest products that are lighter, more efficient, and easy-to-use. One of the tools you can add to this is the newly designed Panda Cloud Cleaner, with new ways to detect, disinfect, inform, and protect from the start. Panda’s top priority is to keep users safe and maximize security in all aspects of our digital lives.
The post The Most Effective Tools to Keep Your PC Malware-free appeared first on Panda Security Mediacenter.